
Alerteer

App details
About Alerteer
ENTERPRISE SECURITY IS FACING A MASSIVE THREAT
Organizations, large and small, are facing increasing threats to their safety and security. Physical security of their assets and personnel, electronic security including the security of their IT infrastructure, and the security of their information (and Data) are all under constant attack. Someone out there is constantly trying to do “bad things” and succeeding.
EVERYONE is at a risk NO ONE IS IMMUNE
What is the solution?
A lot is being to prevent breaches; however, breaches are happening. A foolproof way to prevent attacks has not been developed. The first step to reduce damage is get awareness about them “as and when they happen” through Real-Time Alerts. This way immediate, adequate and effective counter-measures can be initiated to contain the damage and in relevant cases, even track down the culprits. Any action or response AFTER an attack happens, is a mere reaction and a matter of postmortem analysis and forensic investigations.
The true answer is “Be Aware, Be Alert”
SOLUTIONS MUST BE INTEGRATED INTO AN ENTERPRISE LEVEL SECURITY
Significant amounts of resources are being deployed to combat security threats; however, these efforts are in silos with each having its own strategies, management and staff with little communication between them. In today’s environment, physical threats have an impact on IT operations, and cyber threats have an impact on physical operations. Everything is interconnected. To treat cyber and physical threats separately creates unnecessary confusion, delays, inefficiencies and increases expenses significantly …
Even after billions of dollars of expenditures, organizations keep incurring millions and billions of dollars of cost as a consequence of attacks. Current measures are failing repeatedly and most of the time the actions taken are largely reactive in nature, focusing on postmortem forensic analysis of the breach/attack. Security solutions can no longer be in silos.
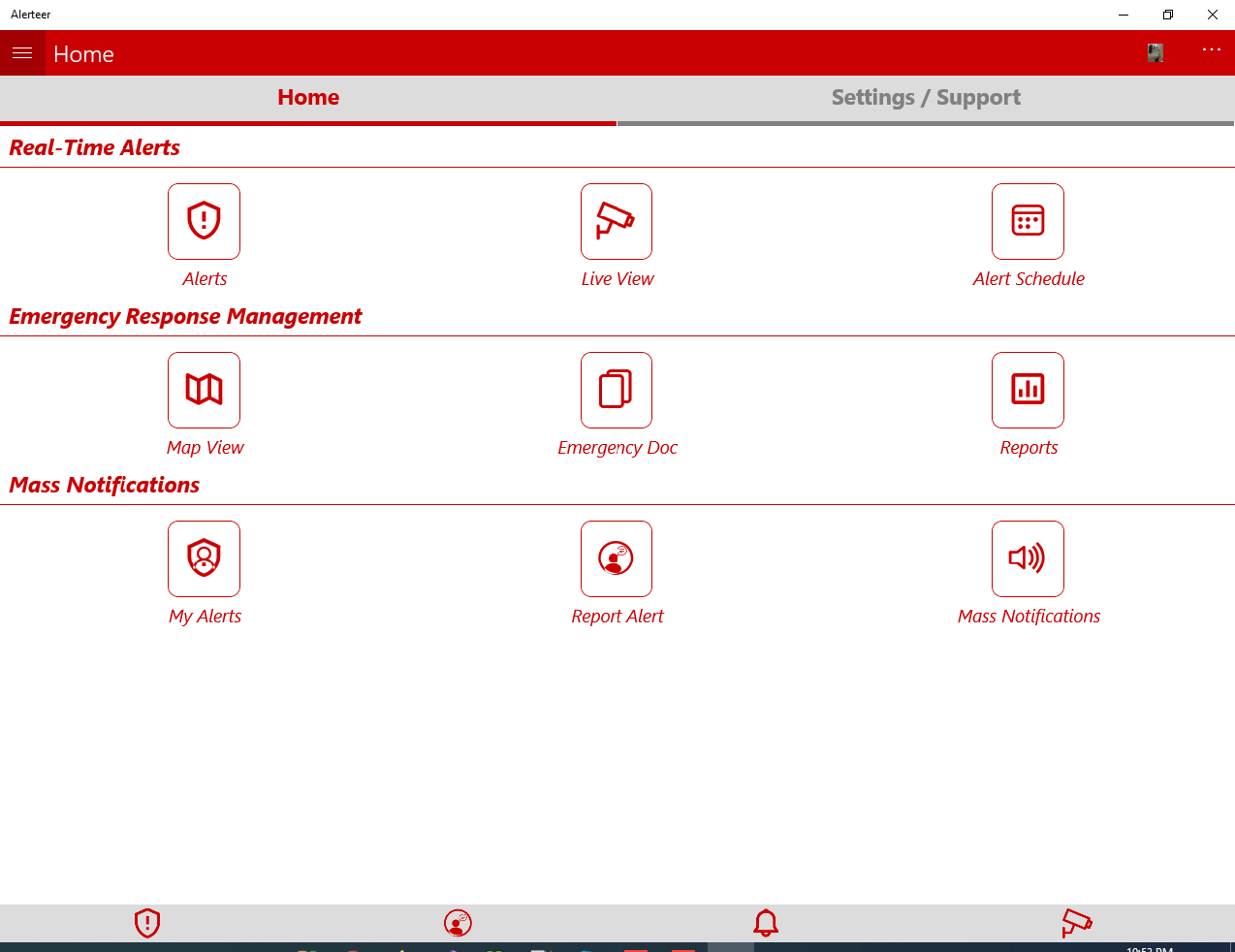
Key features
-
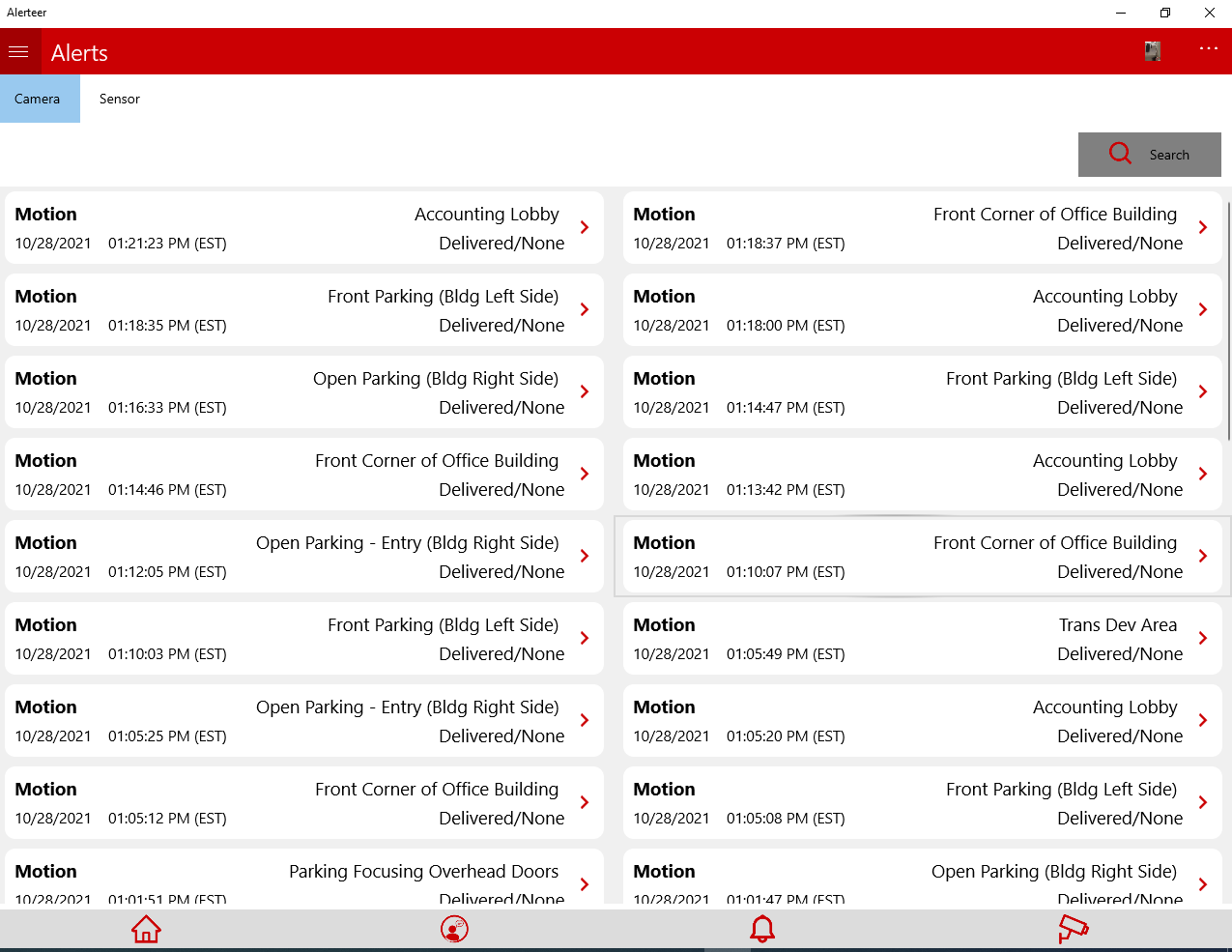
Real-Time Alerts
-
Just-in-Time Detection
-
Mass Notifications
-
Emergency Response Management
-
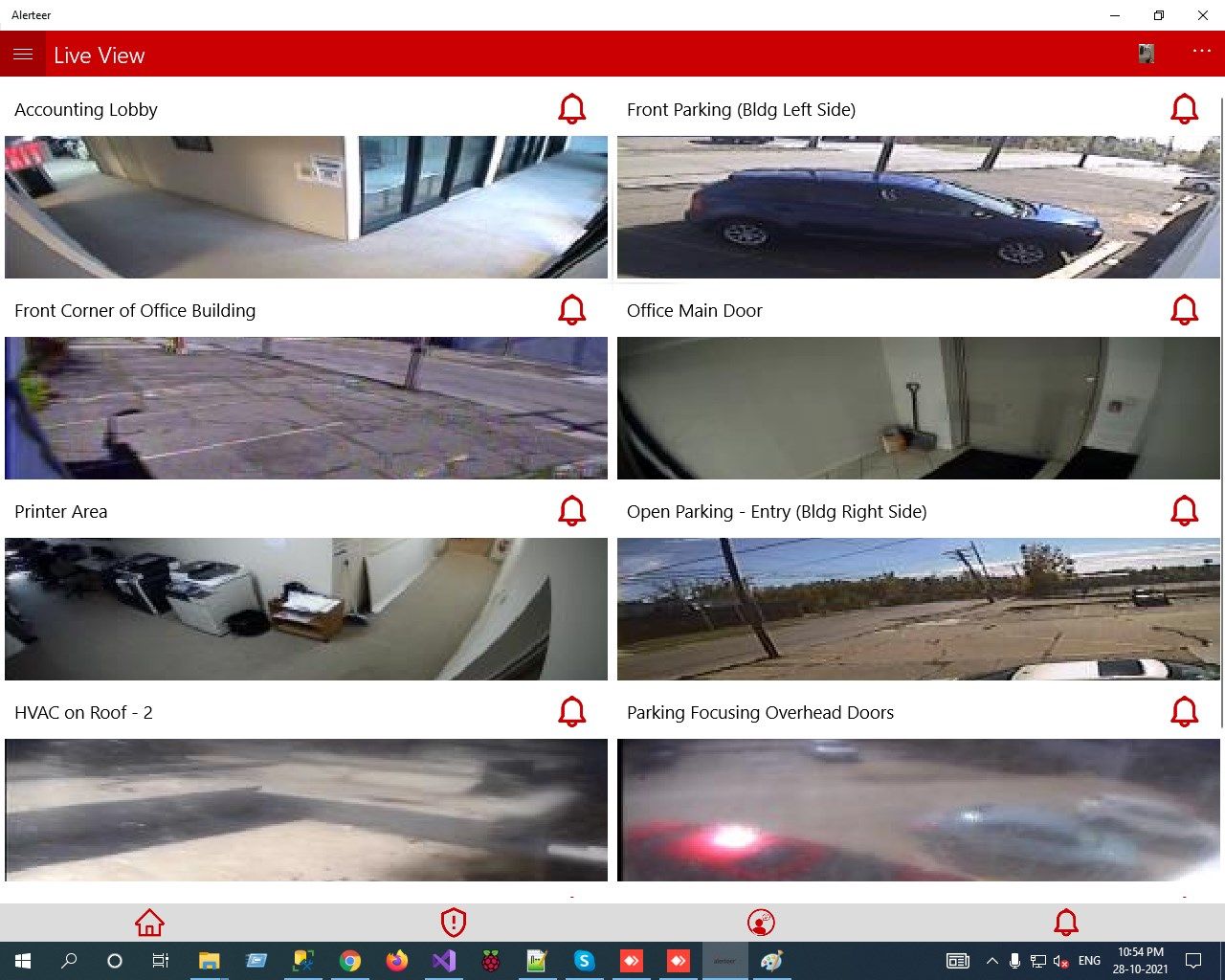
Automated Security Monitoring
-
Advanced Video Analitics