
Description
DEFINITION
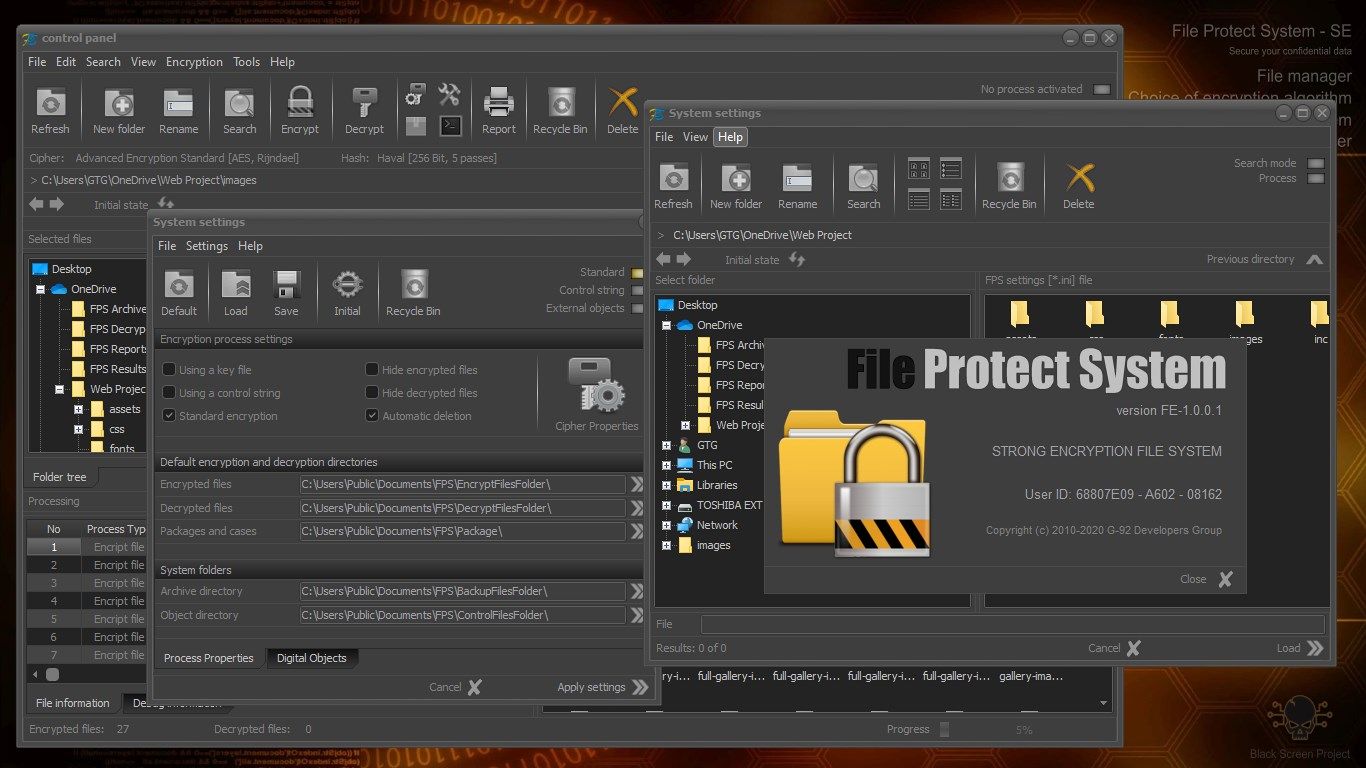
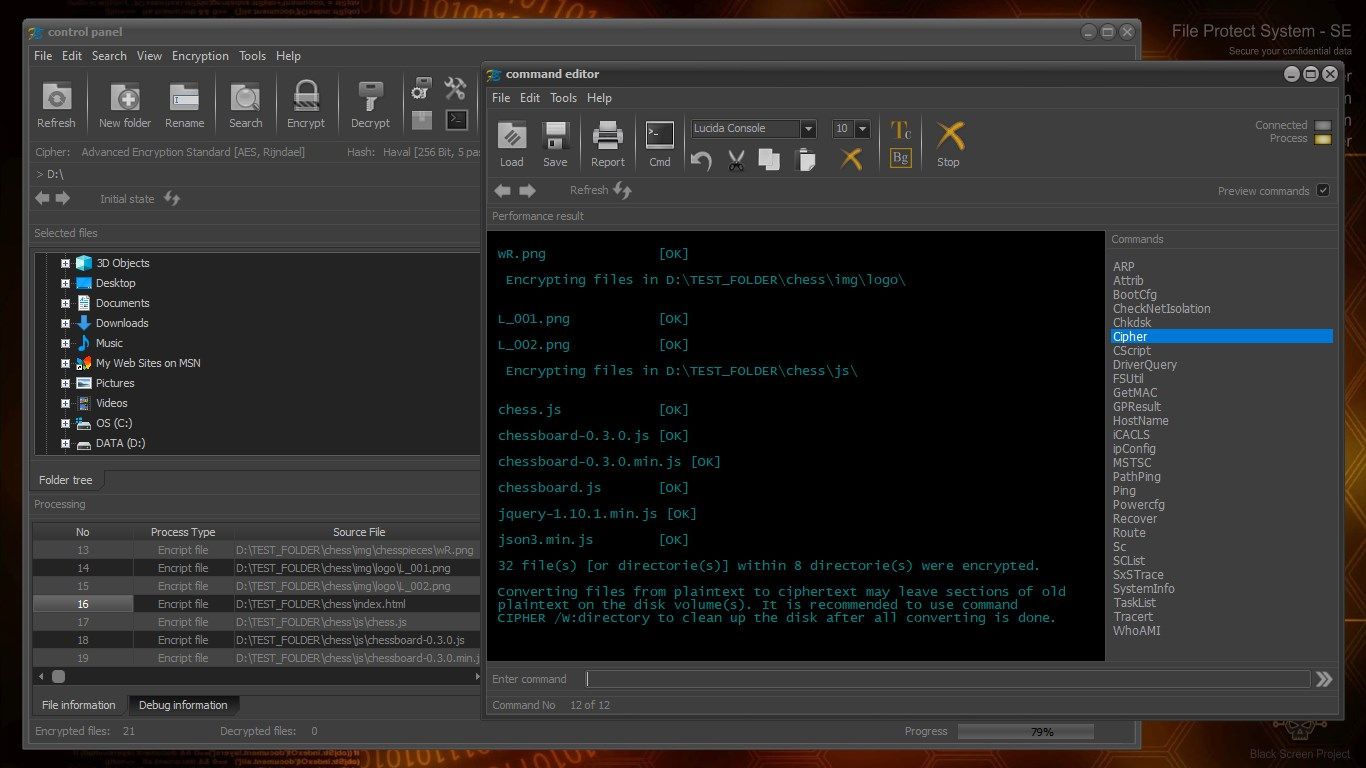
File Protect System (FPS) is a software application for protection of personal data and critical information.
This protection is performed by reliable strong encryption of files and folders.
CUSTOMIZABLE AND EASY
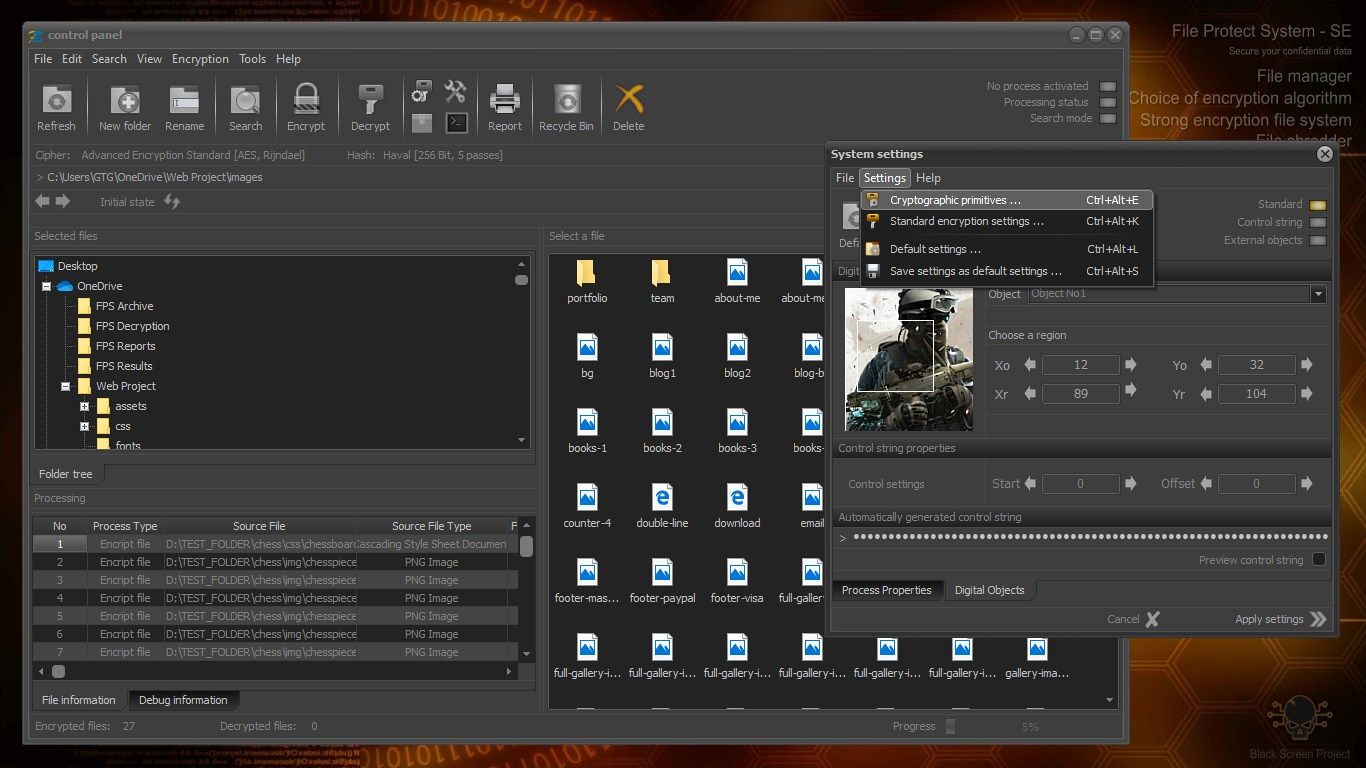
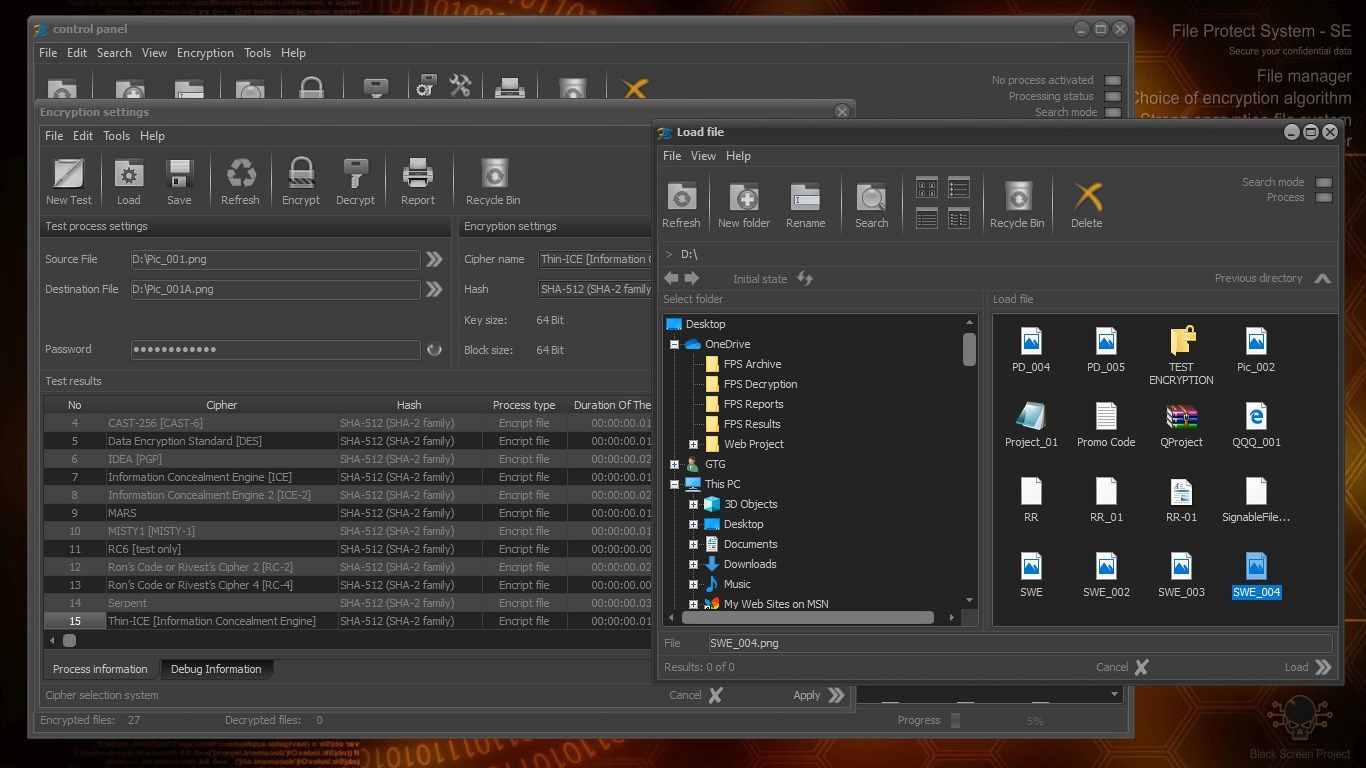
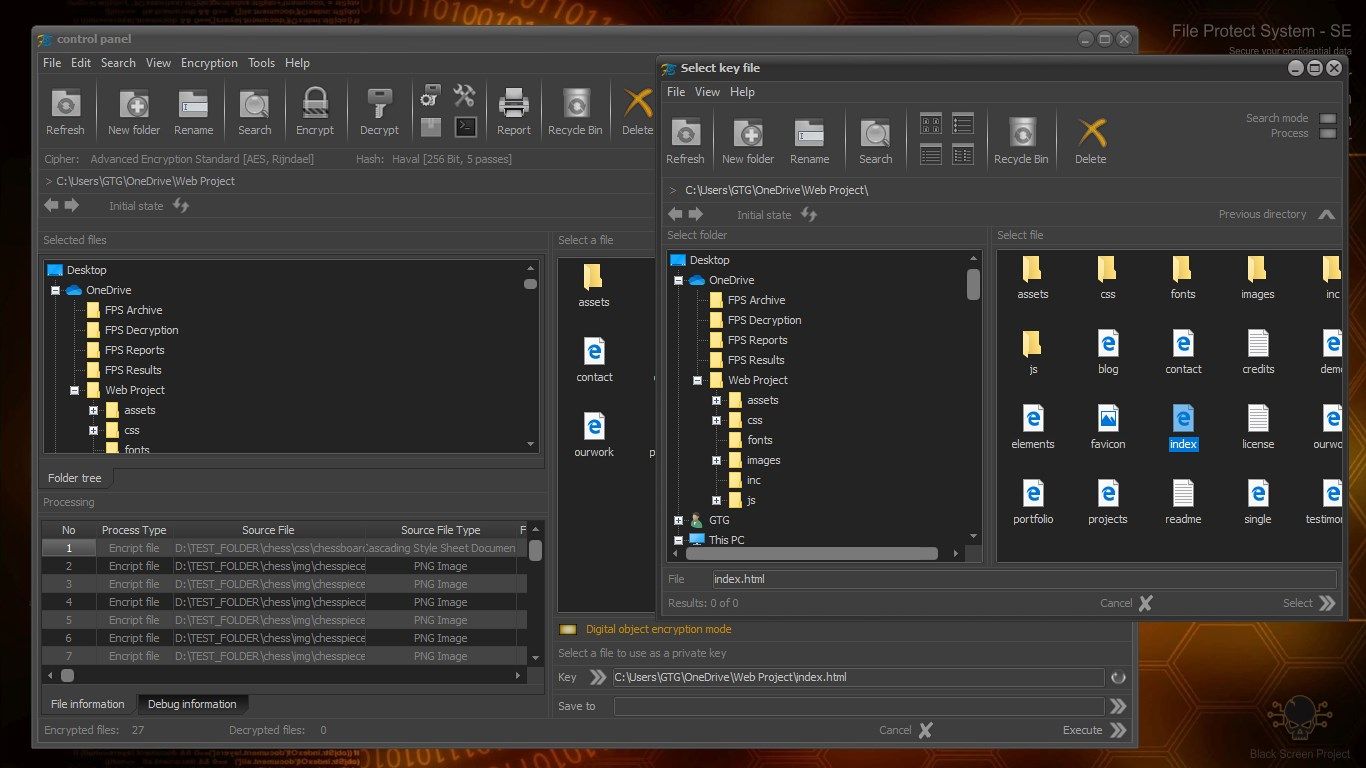
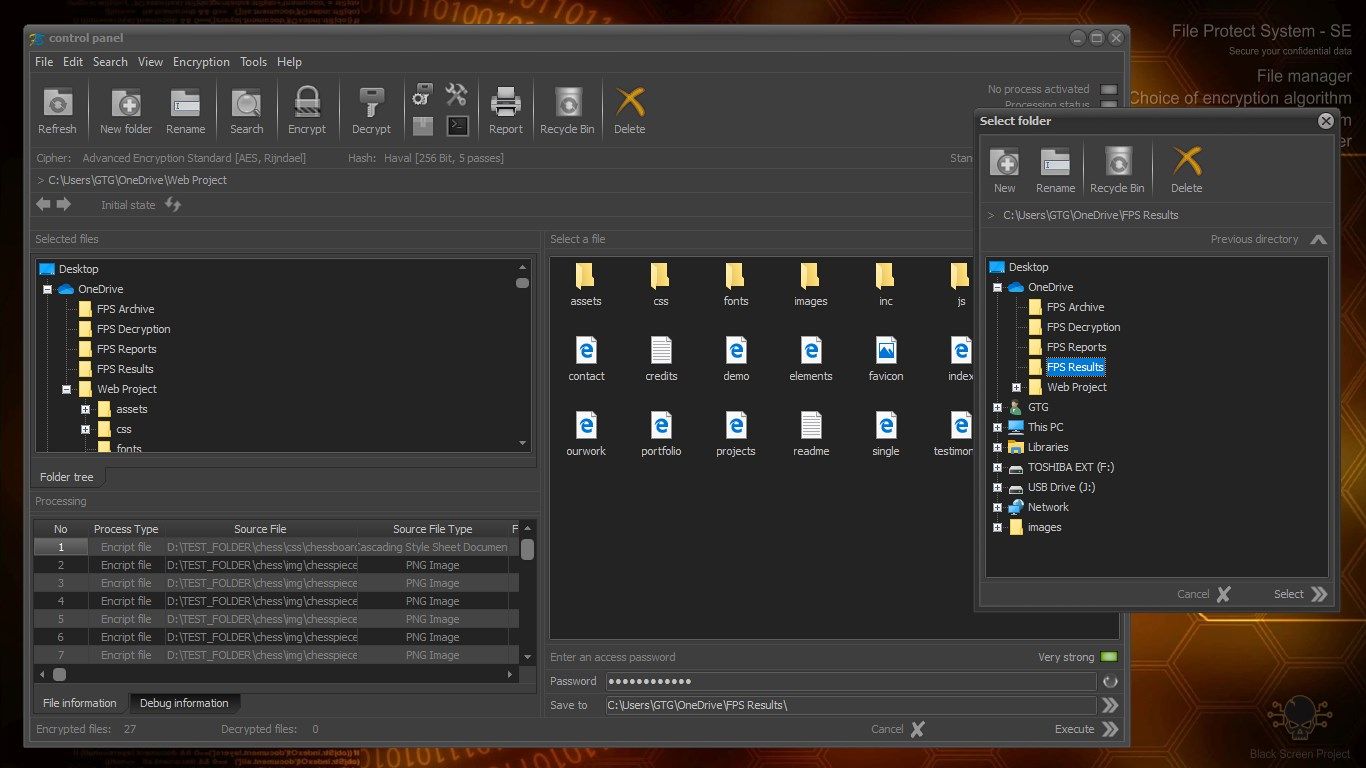
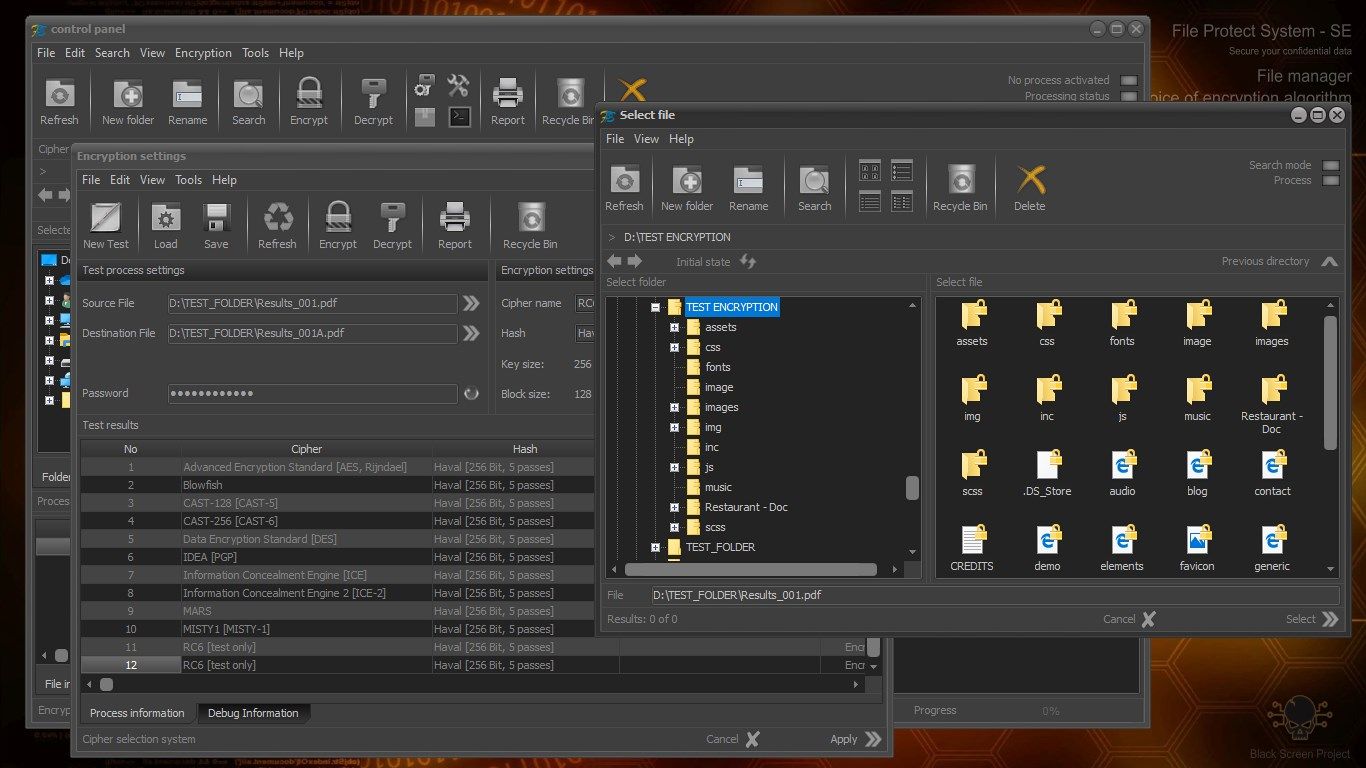
Working with FPS does not require special knowledge. The interface is intuitive. Working with the application is very similar to that of File Explorer. Users can choose between a large number of encryption algorithms. Settings can be saved, which allows customization of the system.
AVAILABLE VERSIONS
- Free Edition (FPS-fe) - Limited Edition version. Used for educational.
- Light Edition (FPS-le) - Personalized, accountant and law firms.
- Standard Edition (FPS-se) - Designed for small and medium-sized businesses.
- Semi-Professional Edition (FPS-spe) - Used by hotels, development units and software companies.
- Professional Edition (FPS-pe) - Focused on industrial processes and large data sets.
- Enterprise Edition (FPS-ee) - Used by industry and bank structures and corporations.
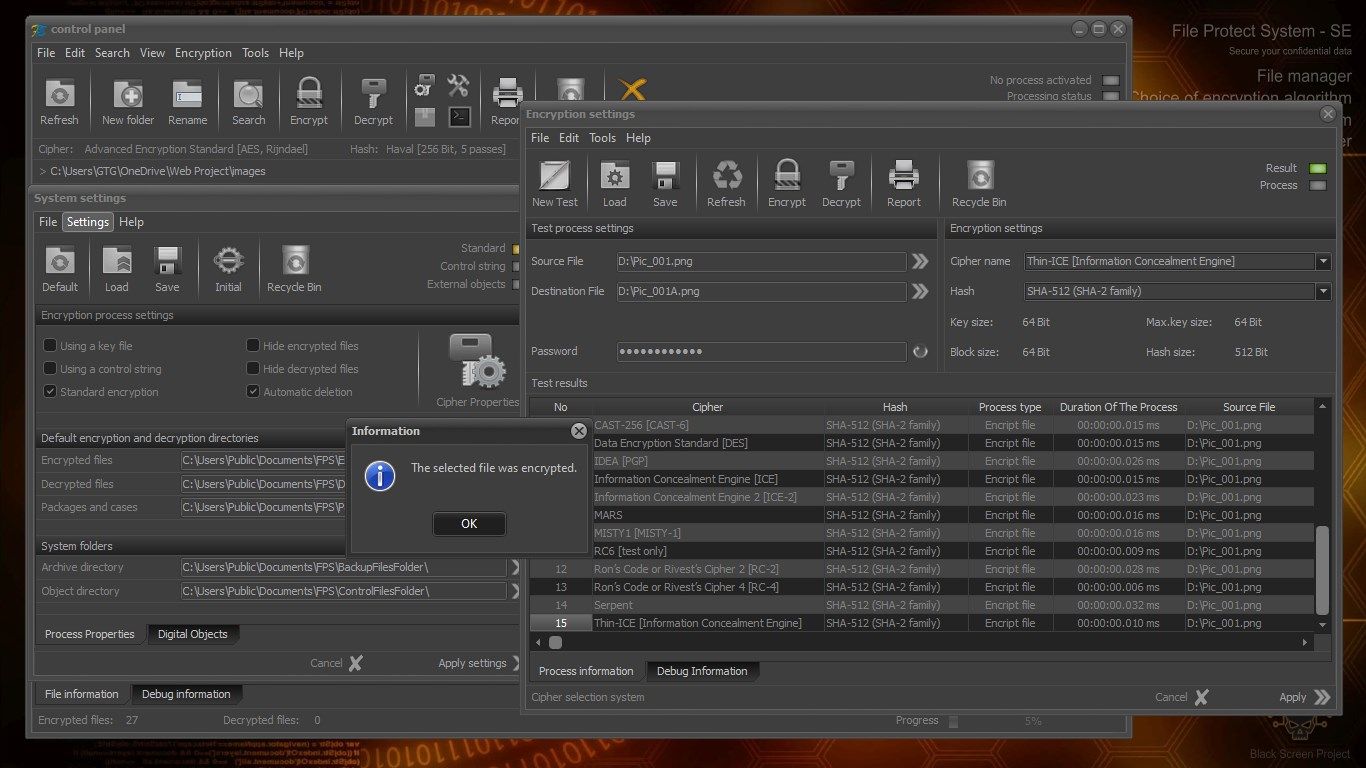
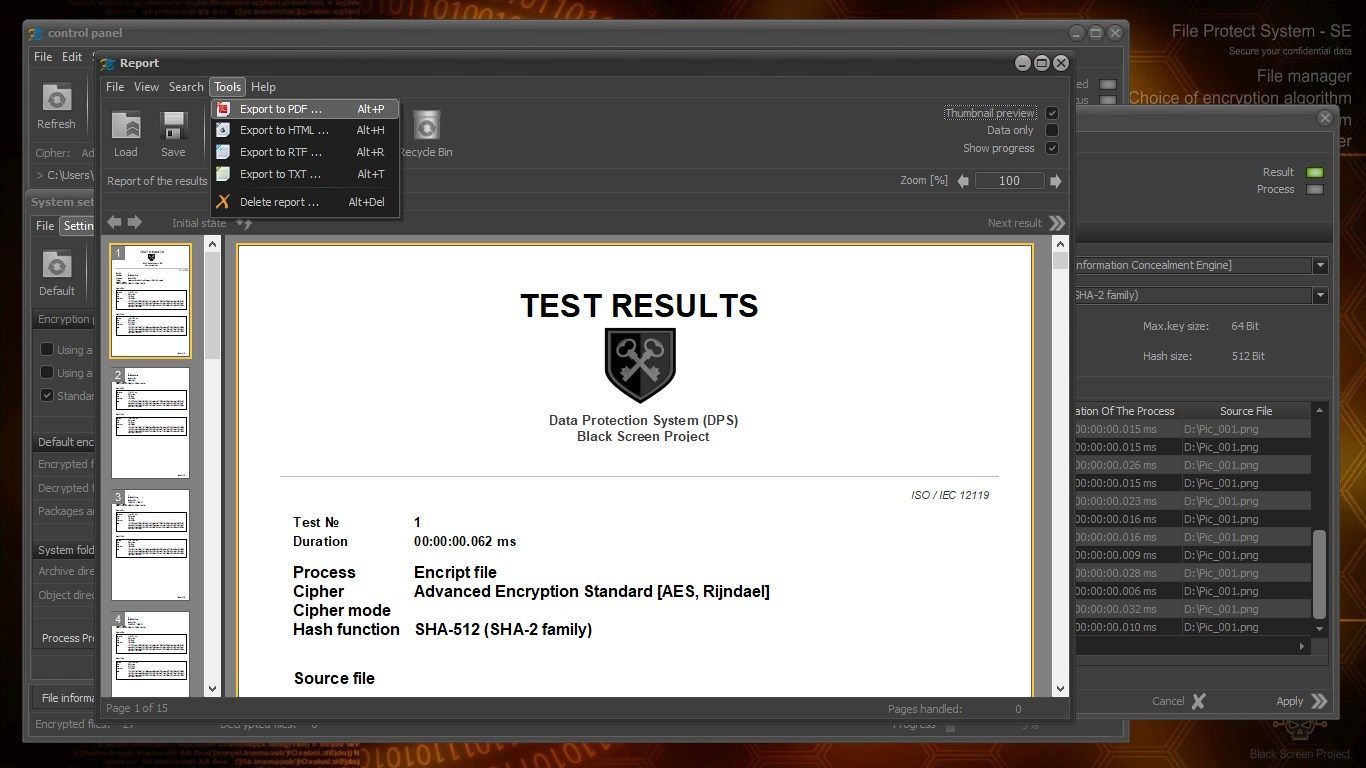
ENCRYPTION ALGORITHMS AND HASH FUNCTIONS
The application includes the following standard encryption algorithms:
- Advanced Encryption Standard (block size of 128 bits, key lengths: 128, 192 and 256 bits)
- Blowfish
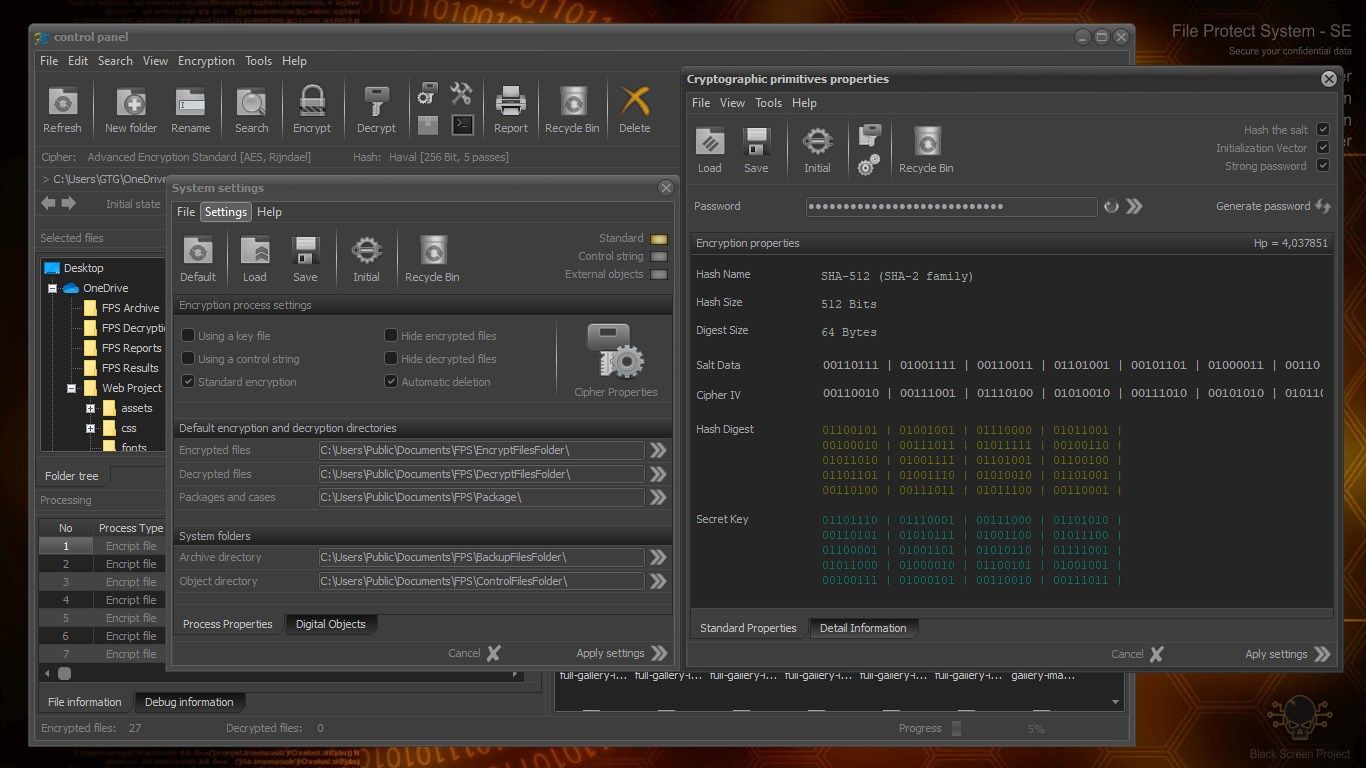
- Haval (256 bit, 5 passes)
- CAST-128 (CAST-5)
- CAST-256 (CAST-6)
- Information Concealment Engine (ICE)
- Information Concealment Engine 2 (ICE-2)
- ICE Encrypt
- MISTY-1 (Mitsubishi Improved Security Technology)
- Ron’s Code 2 or Rivest’s Cipher 2 (RC-2)
- Ron’s Code 4 or Rivest’s Cipher 4 (RC-4)
- Ron’s Code 5 or Rivest’s Cipher 5 (RC-5)
- Ron’s Code 6 or Rivest’s Cipher 6 (RC-6)
- Serpent
- Tiny Encryption Algorithm (TEA)
- Twofish
Affordable hash functions:
- Secure Hash Algorithm 1 [SHA-1]
- RIPEMD-160
- Haval [256 Bit, 5 passes]
- Message Digest 5 [MD-5]
- Message Digest 4 [MD-4]
- Tiger
- RIPEMD-128
- SHA-256 (SHA-2 family)
- SHA-384 (SHA-2 family)
- SHA-512 (SHA-2 family)
USED ISO STANDARDS
ISO 10116: Information Processing — Modes of Operation for an n-bit block cipher algorithm.
ISO 9797: Data cryptographic techniques — Data integrity mechanism using a cryptographic check function employing a block cipher algorithm.
ISO 9798-2: Information technology — Security technicues — Entity authentication mechanisms — Part 2: Entity authentication using symmetric techniques.
ISO 10118-2: Information technology — Security technicues — Hash-functions — Part 2: Hash-functions using an n-bit block cipher algorithm.
ISO 11770-2: Information technology — Security technicues — Key management — Part 2: Key management mechanisms using symmetric techniques.
USA STANDARDS
Encryption: Data Encryption Standard (DES) - FIPS 46-3
Encryption: DES Modes of Operation - FIPS 81
Encryption: Advanced Encryption Standard (AES) - FIPS 197 (with keys sizes of 128 and 256 bits)
Hashing: Secure Hash Algorithm - FIPS 180-2 (using SHA-256 and SHA-384)
Guidelines on Electronic Mail Security - Special Publication 800-45 Version 2
-
strong encryption files and folders
-
file shreddes
-
crypto constructor
-
crypto analyzer
-
merging crypto primitives
-
batch processing mode
