
Web Penetration Recon Tools, Methods and Attacks
Reviews:
0
Category:
Books & reference
Description
This is an Advanced Guide on Web Penetration Recon Tools, Methods and Attacks which provides detailed guide on Modern Modes of
Network Server Penetration Testing using Python Tools and Scripts modules. The content of this guide include:
- Advanced Attacks and Defense using Python
- Building a Vulnerable Virtual Environment
- Burp Suites - Vulnerabilities Scanners and Tools
- DDoS and BOTNETs Tools and Attacks
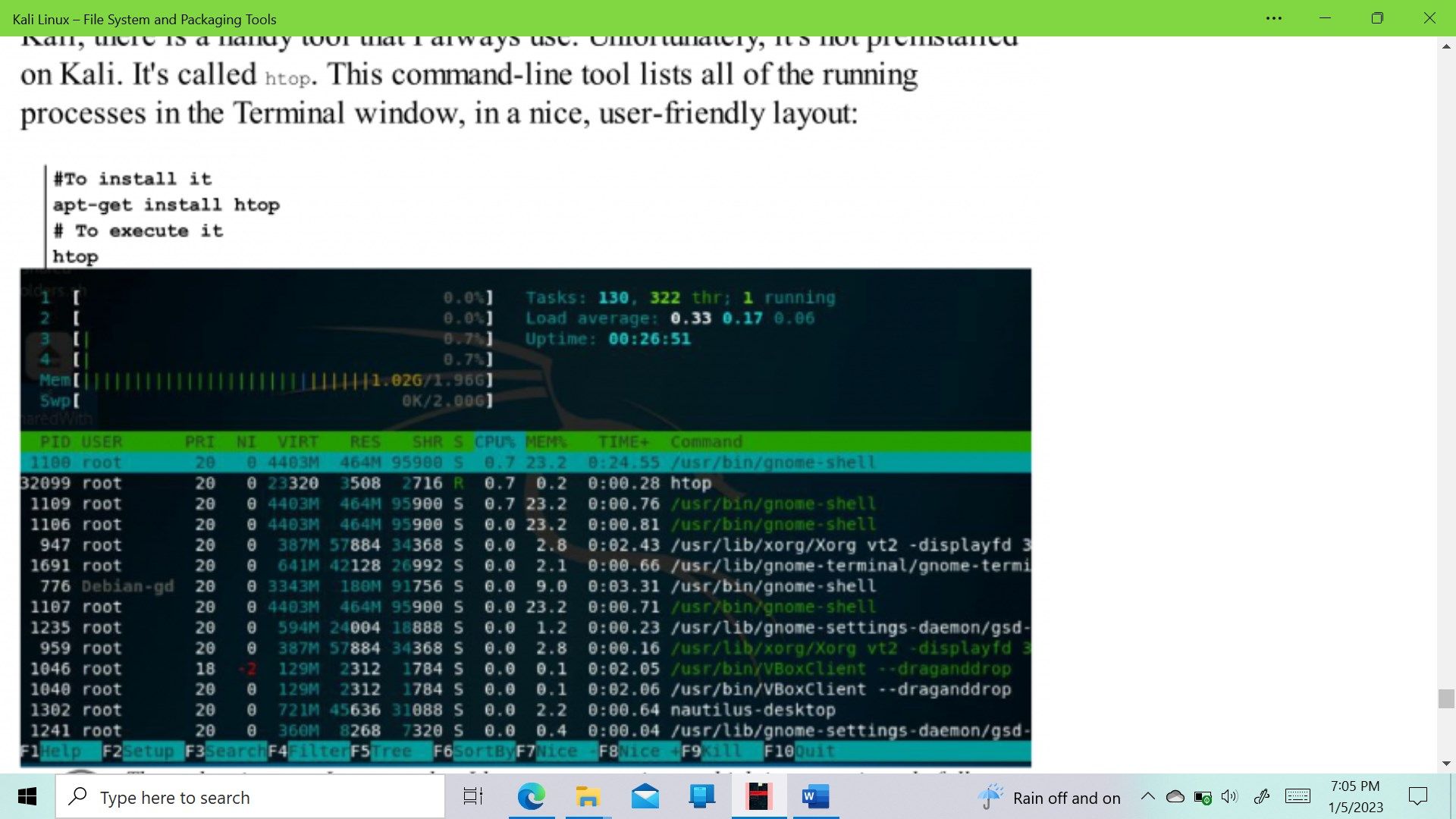
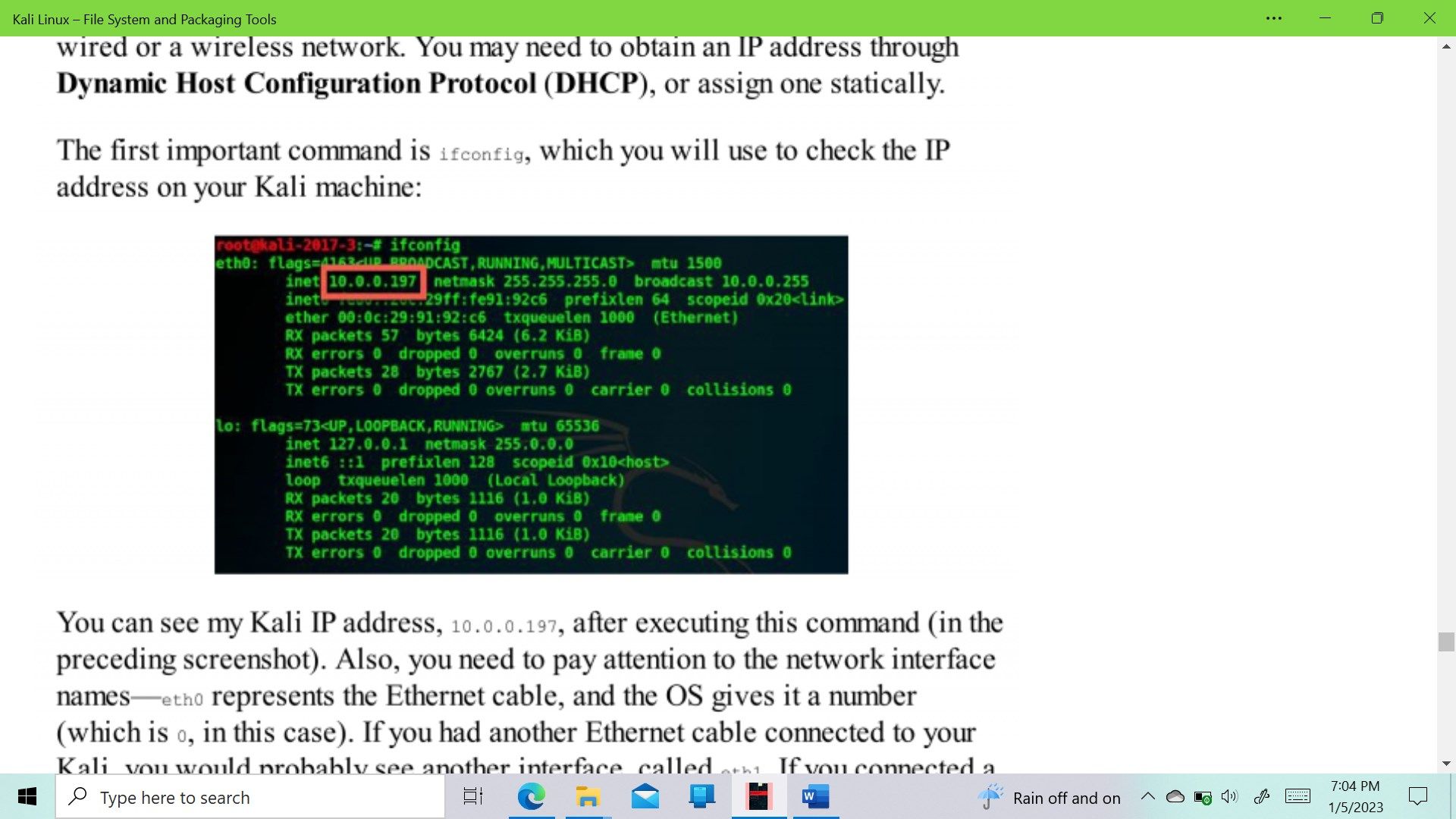
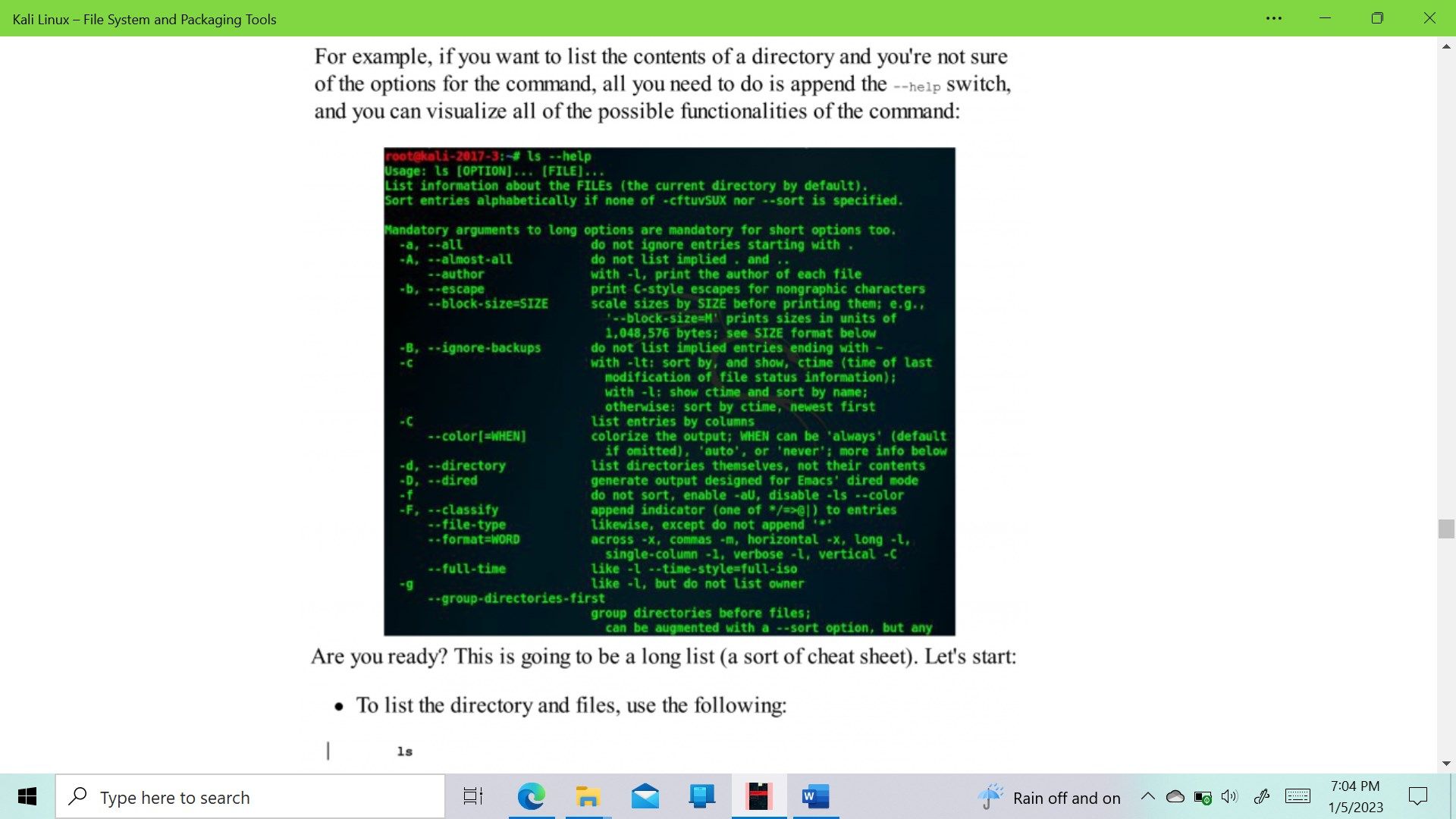
- Kali Linux - File System and Packaging Tools
- Penetration Testing With NMAP, OpenVAS and Metasploit
- PenTest Automation using Python
- Real Practical Web Penetration Testing
- Web Application Vulnerabilities -XSS, CSRF, SQLI
- Web Penetration Recon Tools, Methods and Attacks
- Man-in-the-middle Attacks, ARP Watcher and MAC Flooder
- Password Sniffer, Sniffer Detection, IP Spoofing and SYN Flooder
- Setup and application of the following Recon Tools: Fierce, theHarvester, SubBrute, CeWL,
DirBuster, WhatWeb, Maltego etc. - Web Application Vulnerabilities Attacks and Defense - Remote and Local File Inclussion,
Croos-Site Scripting (XSS), Cross-Site Request Forgery (CSRF), SQL Injection (SQLi),
and Command Injection Attacks. - Linux kernel exploitation
- UserLand versus kernel land
- Linux kernel vulnerabilities
- Memory corruption & Kernel Stack vulnerabilities
- Linux Exploit Suggester
- Linux return oriented programming
- Linux hardening
- Corporate Network and Database Exploitation
- Insecure SNMP configuration
- Database server exploitations
- TCP communication
- ICMP scanning
- SSDP scanning
- UDP Scanning
- Host-based & Network-based Intrusion detection systems
- Machine learning for intrusion detection
- Insecure SNMP configuration
- DNS security
- DNS attacks
- Sniffing attacks - ARP Poisoning & MAC spoofing
- WireShark & DDoS attacks - SYN flooding, ICMP flood attack
- Defending against DDoS attacks
- Software-Defined Network penetration testing
- SDN attacks & SDNs penetration testing
- Attacks on database servers - Excessive privileges, SQL injection, Weak authentication & Exposure of backup data
- Active Directory and Kerberos - Active Directory attacks
- Lightweight Directory Access Protocol
- PowerShell and Active Directory
- Using PowerView for Active Directory Attack
- Dumping all domain credentials with Mimikatz
- Dumping LSASS memory with Task Manager (get domain admin credentials)
- Dumping Active Directory domain credentials from an NTDS.dit file
- Docker & Kernel Exploitation
- Building a penetration testing laboratory
- Exploiting Git and Continuous Integration Servers
- Installing Jenkins
- Continuous integration attacks
- Continuous integration server penetration testing
- Continuous security with Zed Attack Proxy
- Metasploit and PowerShell for Post-Exploitation
- Nishang PowerShell for penetration testing and offensive security
- Dissecting Metasploit Framework
- Bypassing antivirus with the Veil-Framework
- Writing your own Metasploit module
- Weaponized PowerShell with Metasploit
- PowerSploit - AntivirusBypass, Exfiltration, Persistence, PowerUp, PowerView
- Defending against PowerShell attacks.
- LAN Exploitation
- MAC attack
- DHCP attacks
- DHCP starvation
- Rogue DHCP server
- VLAN hopping attacks
- Spanning Tree Protocol attacks
- VoIP Exploitation
- Installing Nexpose for Modern Server Penetration Testing
- Advanced Linux Exploitation
- Linux attack vectors - Network, Host & Application Threats
- Linux enumeration with LinEnum
- OS detection with Nmap
-
Burp Suites - Vulnerabilities Scanners and Tools
-
DDoS and BOTNETs Tools and Attacks
-
Kali Linux - File System and Packaging Tools
-
Penetration Testing With NMAP, OpenVAS and Metasploit
-
Web Application Vulnerabilities -XSS, CSRF, SQLI
-
Password Sniffer, Sniffer Detection, IP Spoofing and SYN Flooder
-
Setup and application of the following Recon Tools: Fierce, theHarvester, SubBrute, CeWL, DirBuster, WhatWeb, Maltego etc.
-
Corporate Network and Database Exploitation
-
Host-based & Network-based Intrusion detection systems
-
Advanced Attacks and Defense using Python
Product ID:
9P2BDQ9B095W
Release date:
2023-01-25
Last update:
2023-02-01
