
CORA-X Lite

App details
About CORA-X Lite
CORA-X lite encrypts (CORAfies) sensitive information contained in select files and/or folders.
Why is CORA ‘Quantum Safe’?
CORA is a new, probabilistic encryption that is safe from all computers, including quantum computers. Just about everything is unique; forget about 256 bit, or 512 bit encryption - with CORA encryption varies between 1,200,000 bits and 2 million bits. We don’t want any thief to know anything, including the size of an encryption key.
What is a ‘Multiple Use Pad’?
One Time Pads (OTPs) were long ago identified by Claude Shannon as ‘Perfect encryption’, however, they are not practical as they can only be used once. With a little bit of math and creativity, MUPs are One Time Pads that are reusable, practical and efficient.
How can we know that MUPs are reusable?
The breaking of OTPs when reused is well known. History buffs might enjoy researching the “Venona project”, however, the bottom line is that OTPs and the manner in which they can be broken is used more than once is well know. CORA would happily provide evaluation application in which the same MUP may be used to CORAfy hundreds of messages, any 2 of which would break an OTP.
Why does CORA ‘make hacking irrelevant’?
CORA uses Multiple Use Pads (One Time Pads that are reusable), AES encryption and distributed files (CORA blocs). Each and every CORAfied (encrypted) file results in 2-40 CORA blocs that are distributed across files, devices, or clouds. A hacker would have to know where each CORA bloc resides and obtain each bloc without exception or corruption. Then the hacker would have to obtain the MUP and system files, which are themselves distributed so that they only exist in memory.
Why is CORA unbreakable?
Imagine having just 50 files CORAfied.
There would be 100-2000 CORA blocs. Which blocs go together? Are all the blocs on the same device, or Cloud? Where is the ‘Key’? How large is the MUP?
For simplicity, say there were just 200 CORA blocs that a hacker stole; there might be 2 blocs that go together, or 40. Lets say the order doesn’t matter, then there would be 10^42 different combinations, and that is without any other complications, such as ‘needing the MUP’ or knowing its size.
What happens if I lose my “Key”?
It is crucial that you use the built in “Backup & Restore” engine to backup you your “User data” and “System data”! CORA is designed to be “unbreakable” when proper implemented. Unlike other security products, if you lose, or corrupt your “Key”, it will be impossible to break the encryption! You “must” use the Backup and Restore engine!
Where is the Encryption Key?
The System binaries, including the MUP are dispersed, ideally across multiple devices. CORA-X is designed to be loaded ‘once’ when the computer (or server) is rebooted. At that time the administrator (or user) provides the dispersed files (i.e. plugs in a USB flash drive, and/or points to a location in the Cloud) and loads the system files. These dispersed files are then removed so that the system is in memory ‘only’.
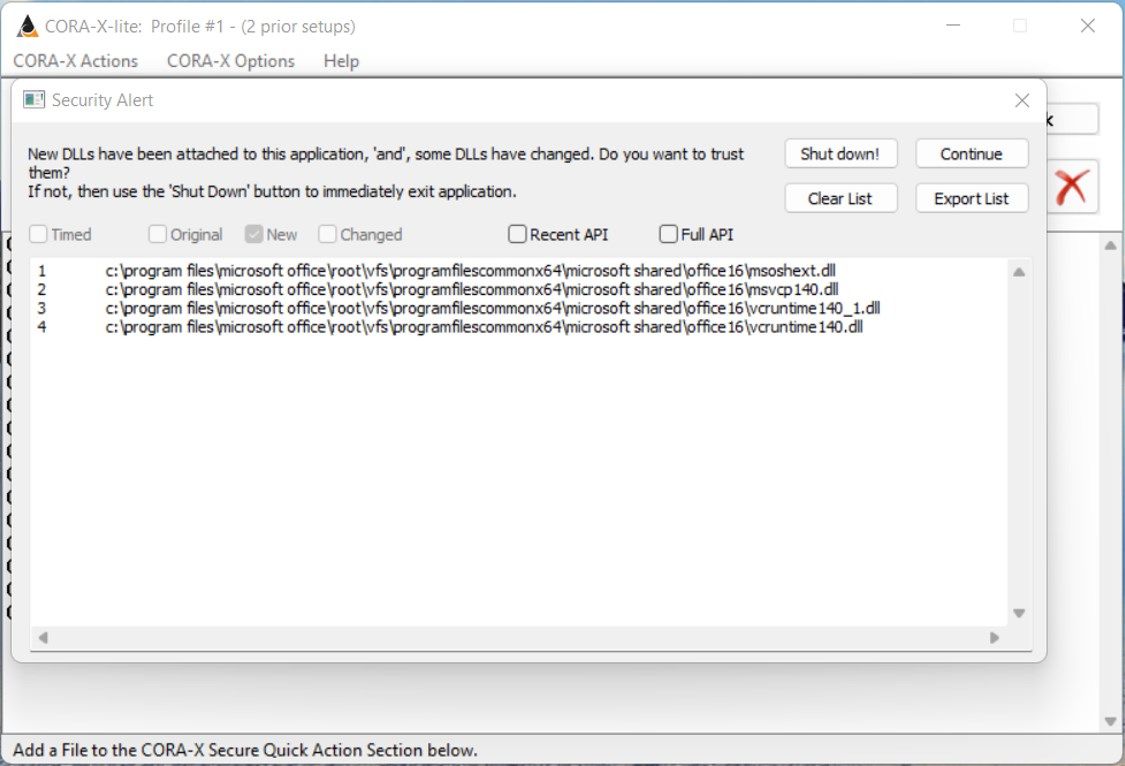
Is there are risk to “in memory” data?
Even so called ‘protected memory’ needs to be monitored. For this reason, CORA-X will advise you if a hither to unknown process attaches to CORA-X’s memory. Many of these security warnings may be safe as there are many system processes (mostly built into Windows OS) that will attach to memory, such as your anti-virus program (as expected). If an ‘unexpected’ process attaches and you are concerned, you may instantly abort CORA-X.
What is needed to ‘read’ CORAfied (encrypted) data?
- The MUP – without corruption (dispersed key).
- The System data supporting the MUP (part of the dispersed key).
- The CORA catalog for a particular file.
- Each and every CORA bloc, without exception or modification.
Key features
-
Quantum Safe, unbreakable Encryption when properly implemented. Probabilistic encryption - everything may vary. Fast and efficient. Promotes good cyber hygiene.