
CPM II fe
App details
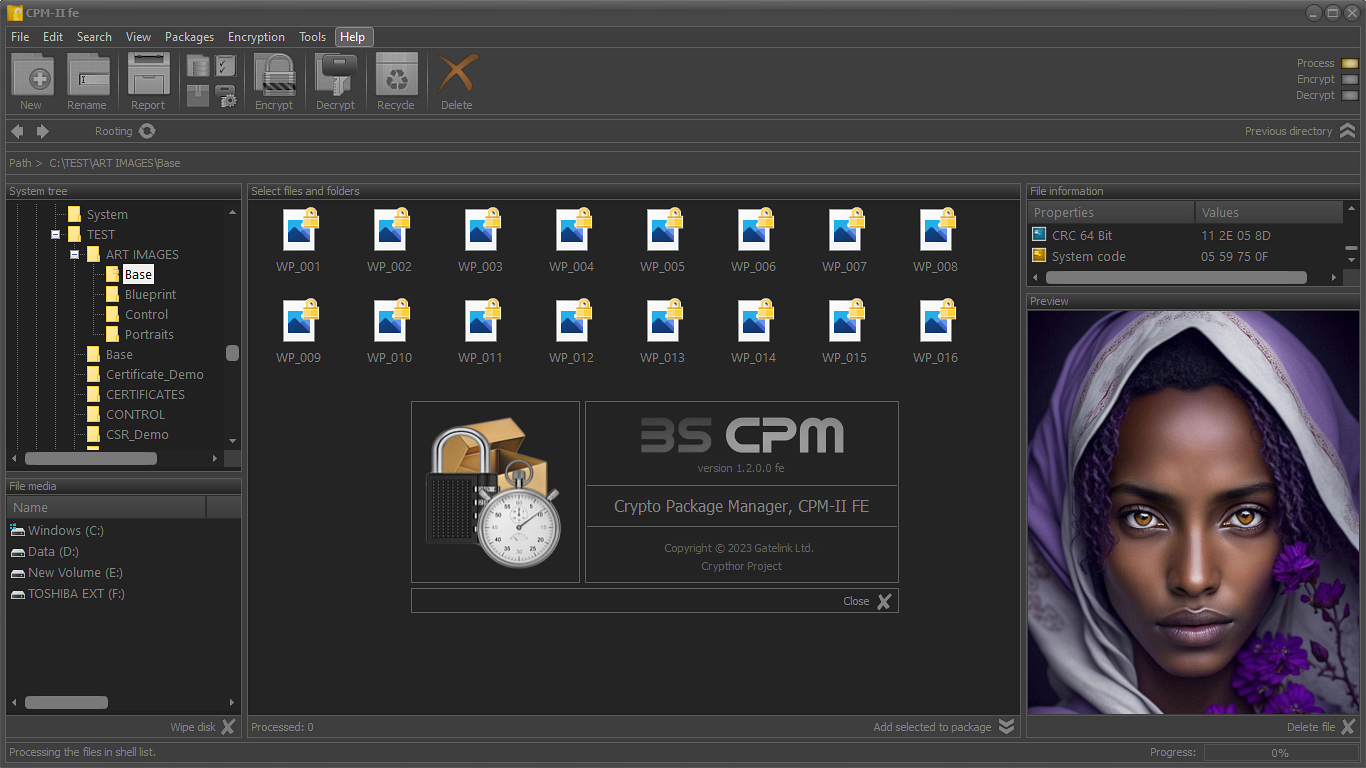
About CPM II fe
DEFINITION
Crypto Package Manager (CPM II) is a specialized application for strong encrypting files and folders located on local, networks, servers, or external data media.
The application allows the following actions:
- Encrypt or decrypt selected files and folders;
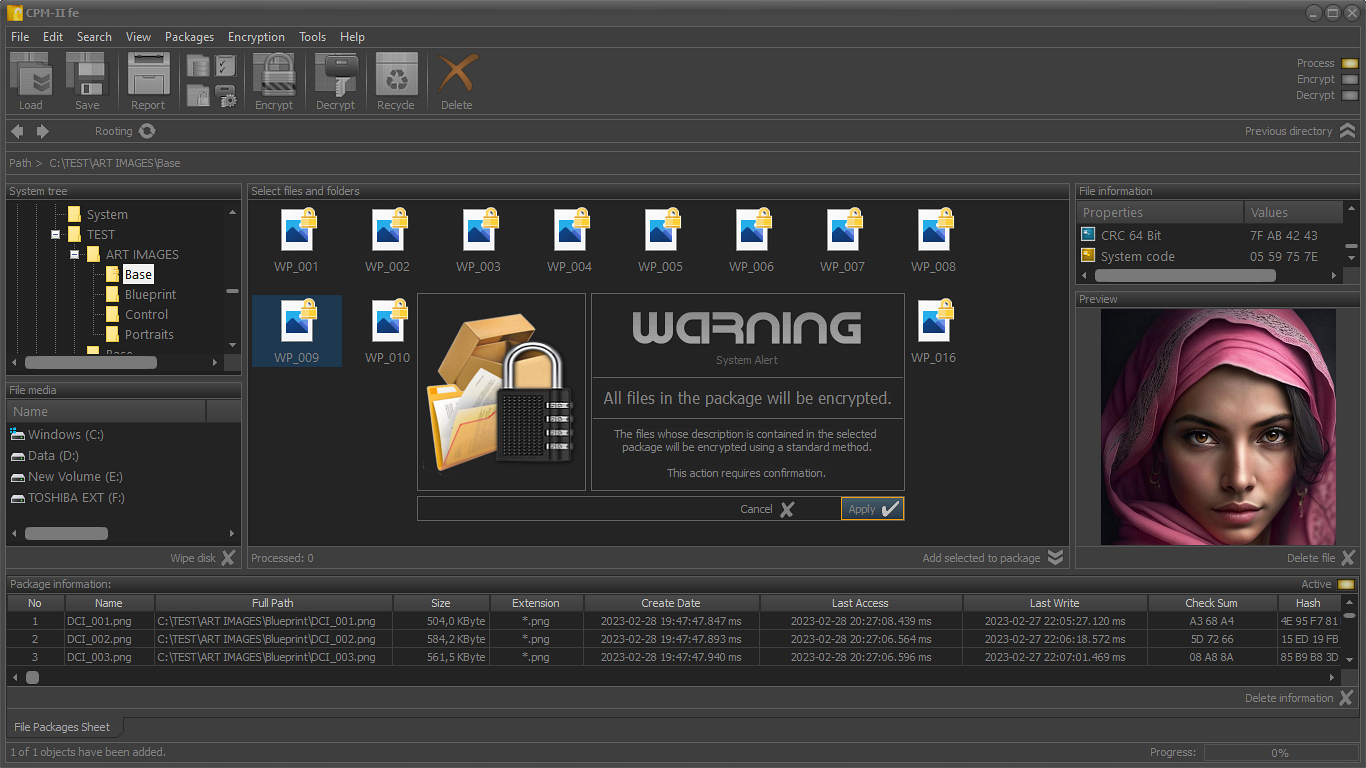
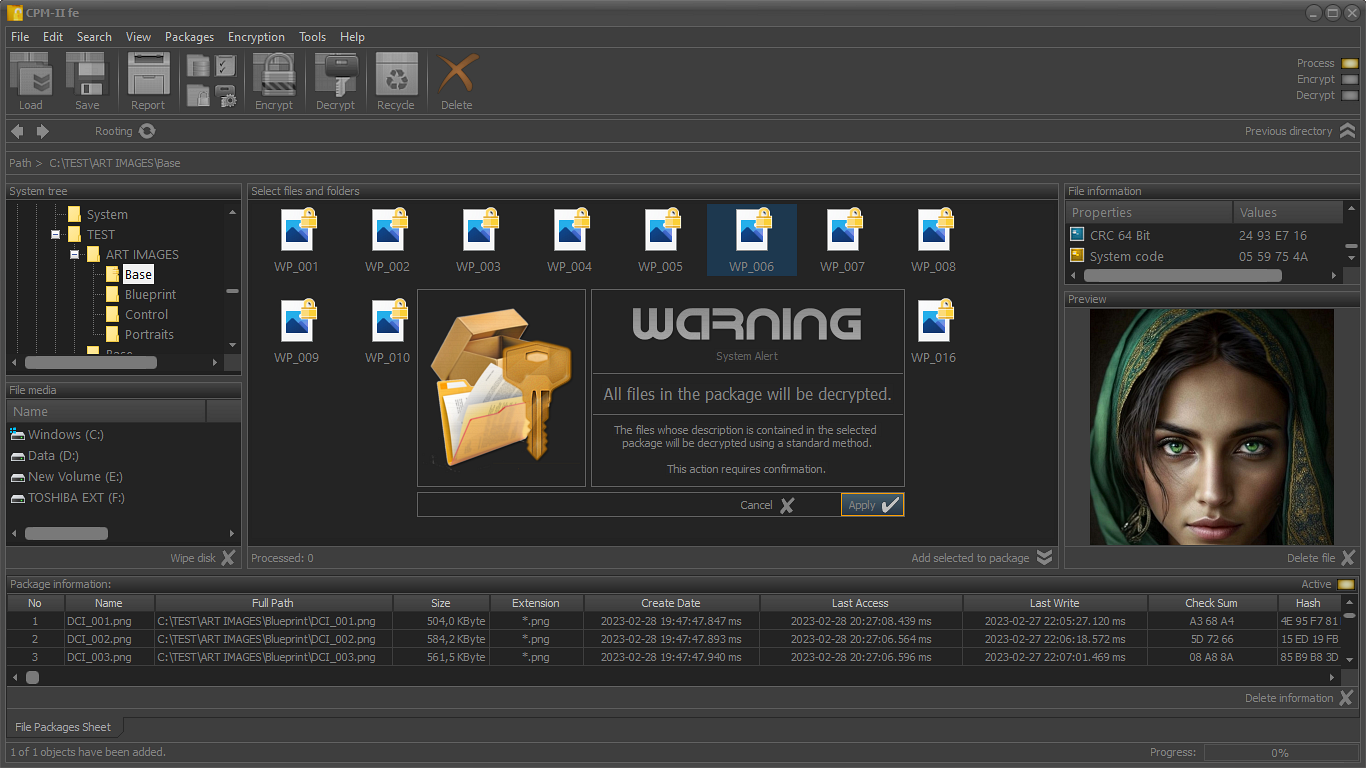
- Secure file packages;
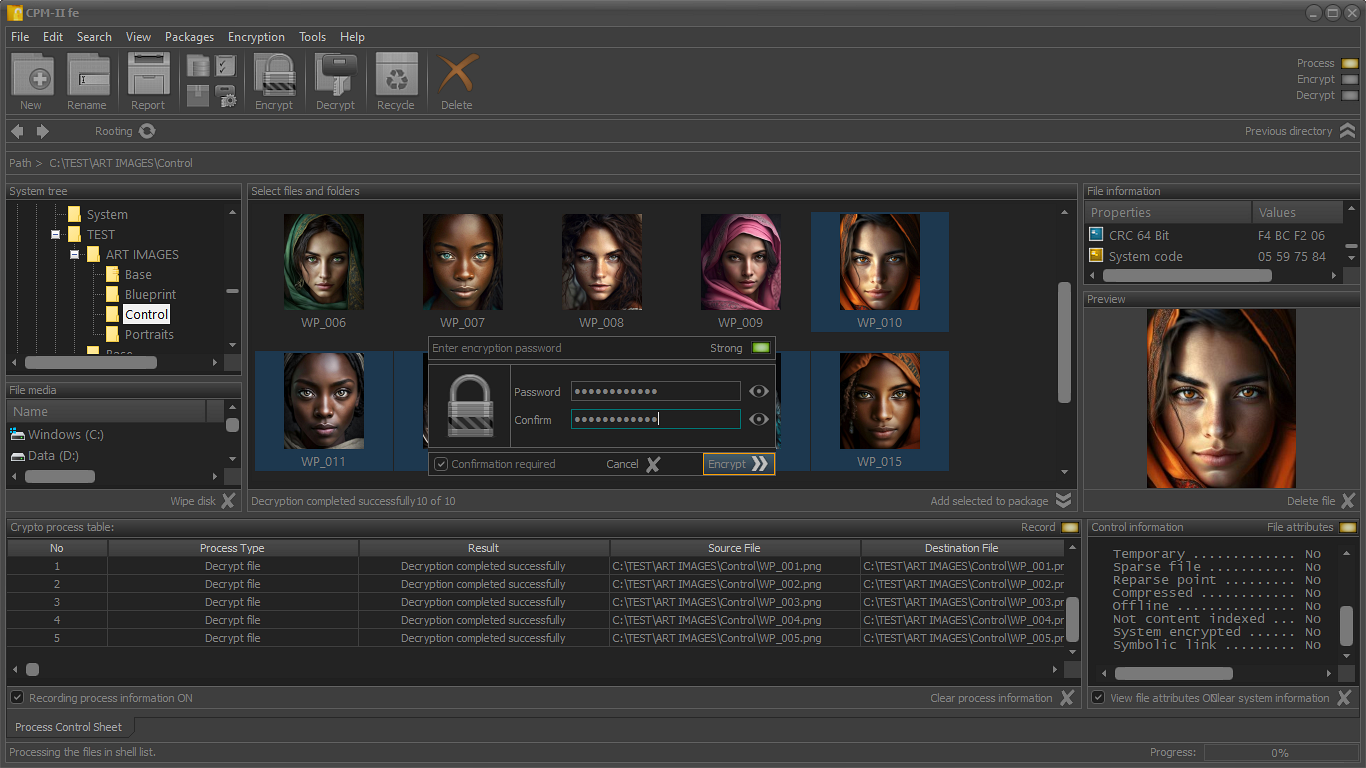
- Encrypting the files in the package;
- Decrypting the files in the package;
- File integrity check;
- File modification control;
- Checking the current status of files and directories etc.
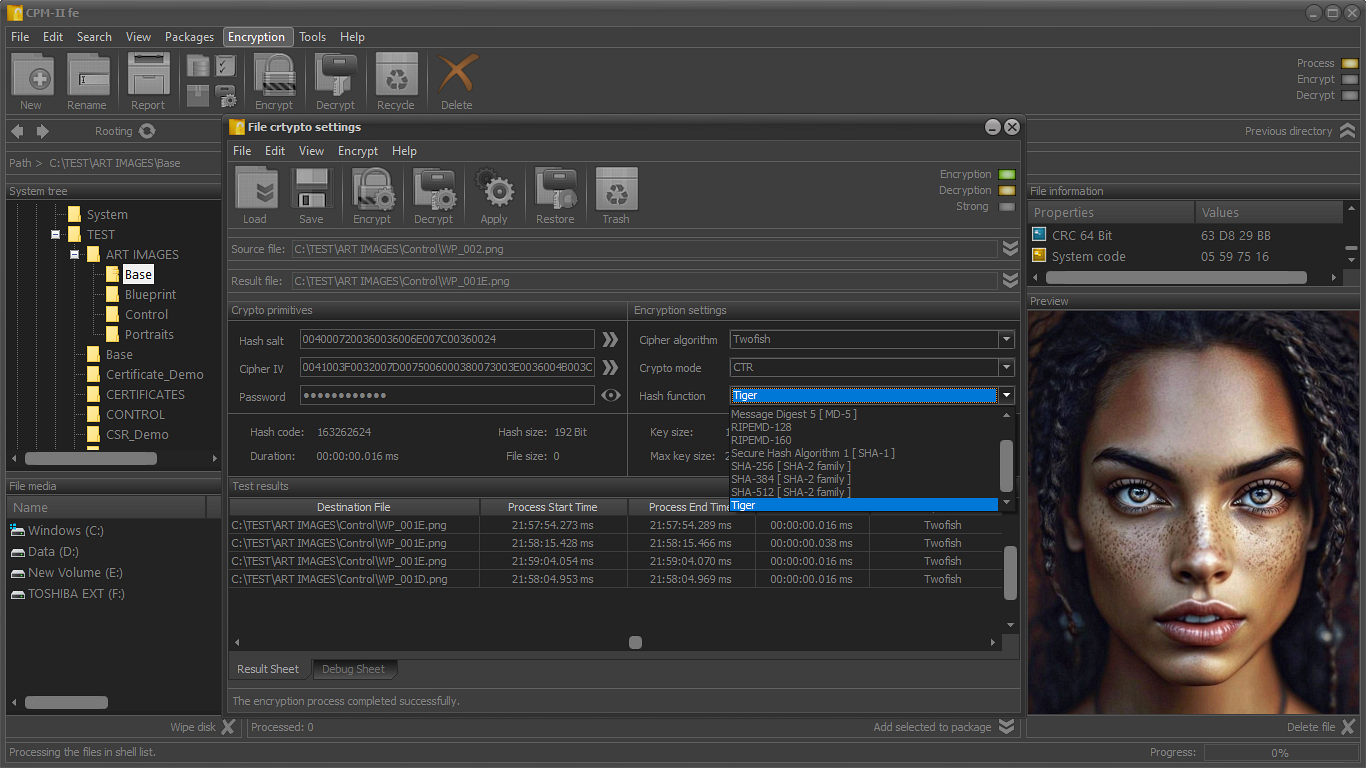
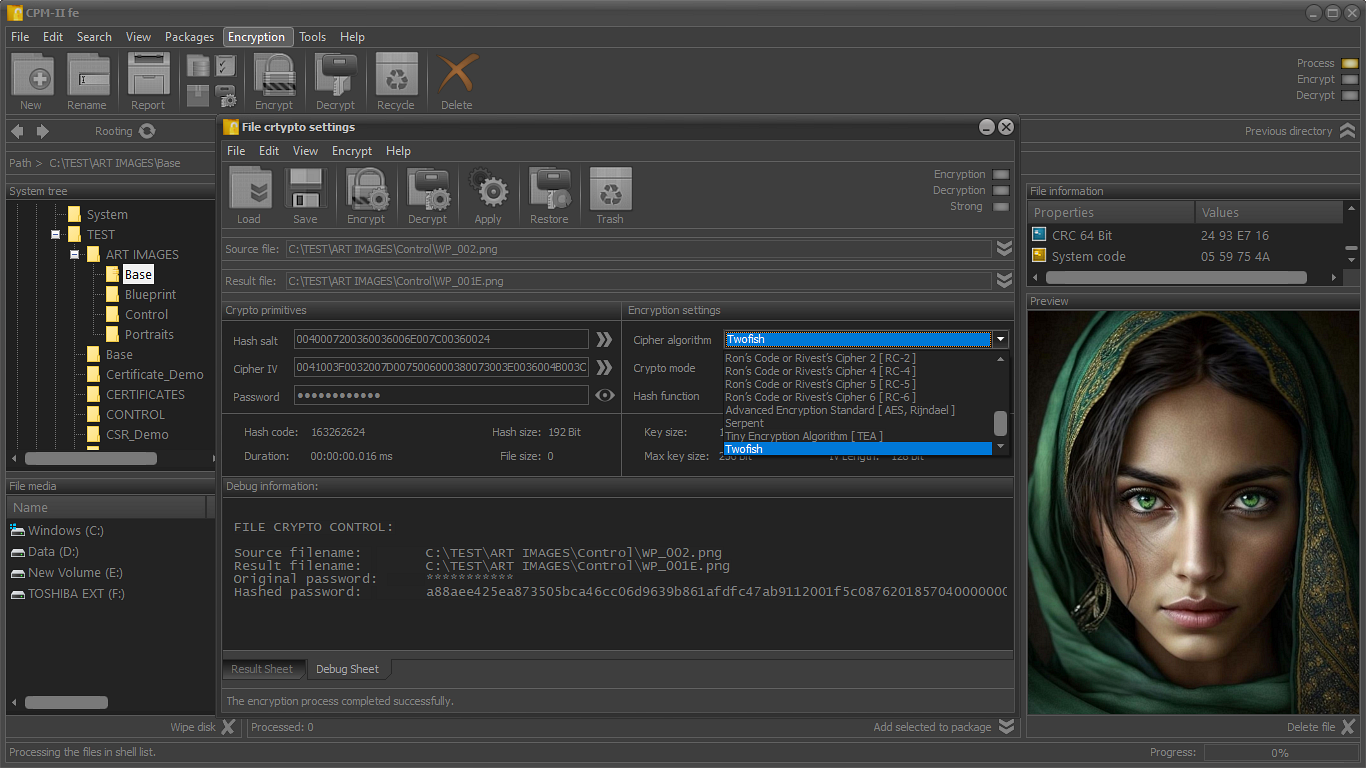
The encryption of the files for which meta-information is available in the packages and which are physically accessible is performed based on session crypto mechanisms.
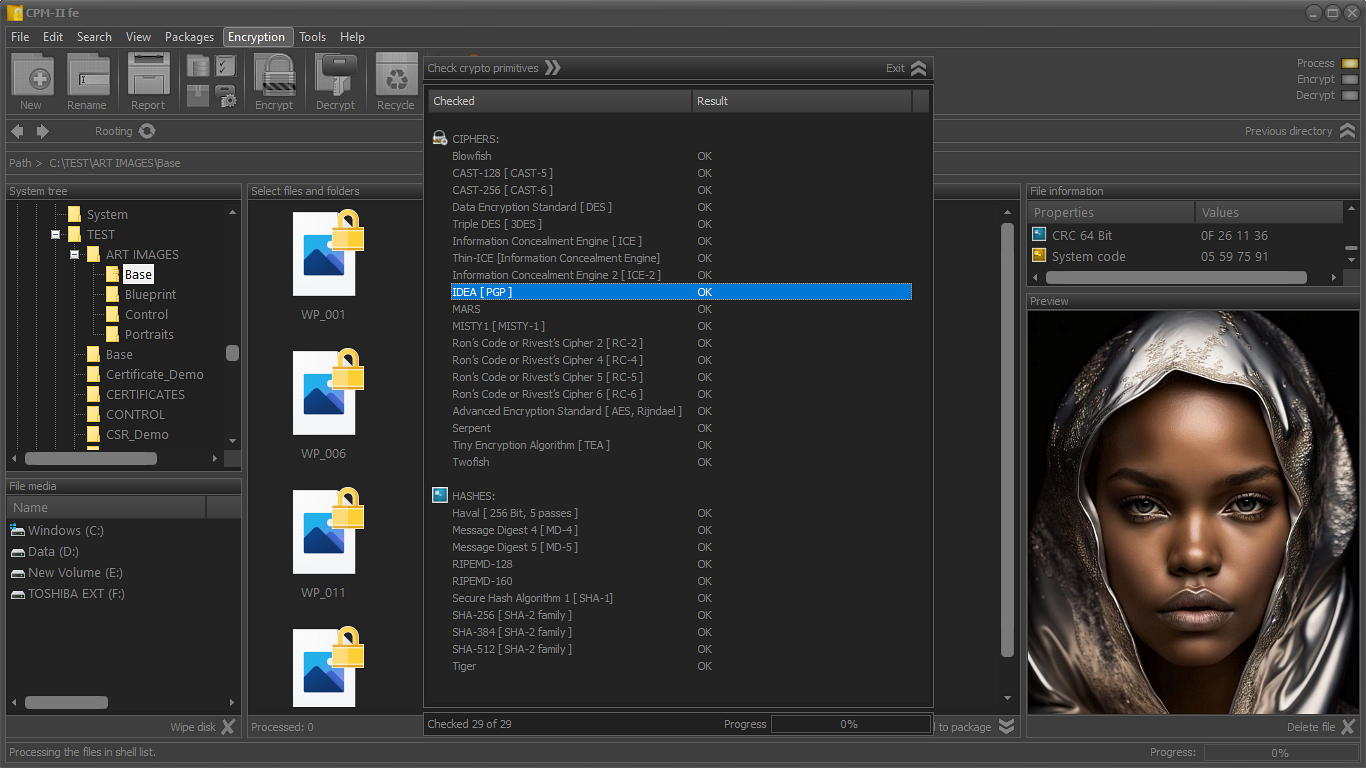
Each crypto mechanism uses a set of proven cryptographic primitives. Configuration of crypto primitives is done automatically.
All operations on the files and folders saved in the package are performed only when the files and folders are physically accessible. If they cannot be accessed (deleted, physically inaccessible network drive, or other reason), this will be reflected in the packet, recording the time when this finding was made.
FIELD OF APPLICATION
Protecting large arrays of files located on different media is a complex and difficult process to implement. The use of file packages allows the automation of this process, increases the efficiency of service, and significantly improves the security of corporate solutions.
Storing, editing, transferring, and destroying files is a process, the importance of which is often overlooked by both users and those responsible for security.
Statistics show that threats related to gaining unsanctioned access by unauthorized persons are related to this problem.
With the help of CPM, it is possible to neutralize all these problems through a highly effective professional cryptosystem using secure file packages.
CPM uses some of the most effective standard digital data encrypting algorithms used by government organizations and corporate structures.
TECHNOLOGICAL SOLUTIONS
The correct choice of algorithms and software technologies for the encryption of digital data is a guarantee of the high efficiency and reliability of the application.
The application uses a set of standard algorithms to build specialized mechanisms for encrypting digital data.
The following standard algorithms are used in the base version:
STANDARD ENCRYPTION ALGORITHMS
- Advanced Encryption Standard (block size of 128 bits, key lengths: 128, 192, and 256 bits)
- Blowfish
- CAST-128 (CAST-5)
- CAST-256 (CAST-6)
- Information Concealment Engine (ICE)
- Information Concealment Engine 2 (ICE-2)
- ICE Encrypt
- MISTY-1 (Mitsubishi Improved Security Technology)
- Ron’s Code 2 or Rivest’s Cipher 2 (RC-2)
- Ron’s Code 4 or Rivest’s Cipher 4 (RC-4)
- Ron’s Code 5 or Rivest’s Cipher 5 (RC-5)
- Ron’s Code 6 or Rivest’s Cipher 6 (RC-6)
- Serpent
- Tiny Encryption Algorithm (TEA)
- Twofish
AFFORDABLE HASH FUNCTIONS
- Secure Hash Algorithm 1 [SHA-1]
- RIPEMD-160
- Haval [256 Bit, 5 passes]
- Message Digest 5 [MD-5]
- Message Digest 4 [MD-4]
- Tiger
- RIPEMD-128
- SHA-256 (SHA-2 family)
- SHA-384 (SHA-2 family)
- SHA-512 (SHA-2 family)
Key features
-
A highly reliable system of encryption of selected files and folders.
-
Crypto mechanisms control modules.
-
Crypto mechanisms test system.
-
Real time crypto processes control.
-
Editing, and deleting files' meta information in packages.
-
Encryption of the files whose information is contained in the package.
-
Deleting of the files whose information is contained in the package.
-
Script editor (protected CMD Manager).
-
High-speed encrypt processing etc.