
FPM II spe

App details
About FPM II spe
FILE PACKAGE MANAGER DESCRYPTION
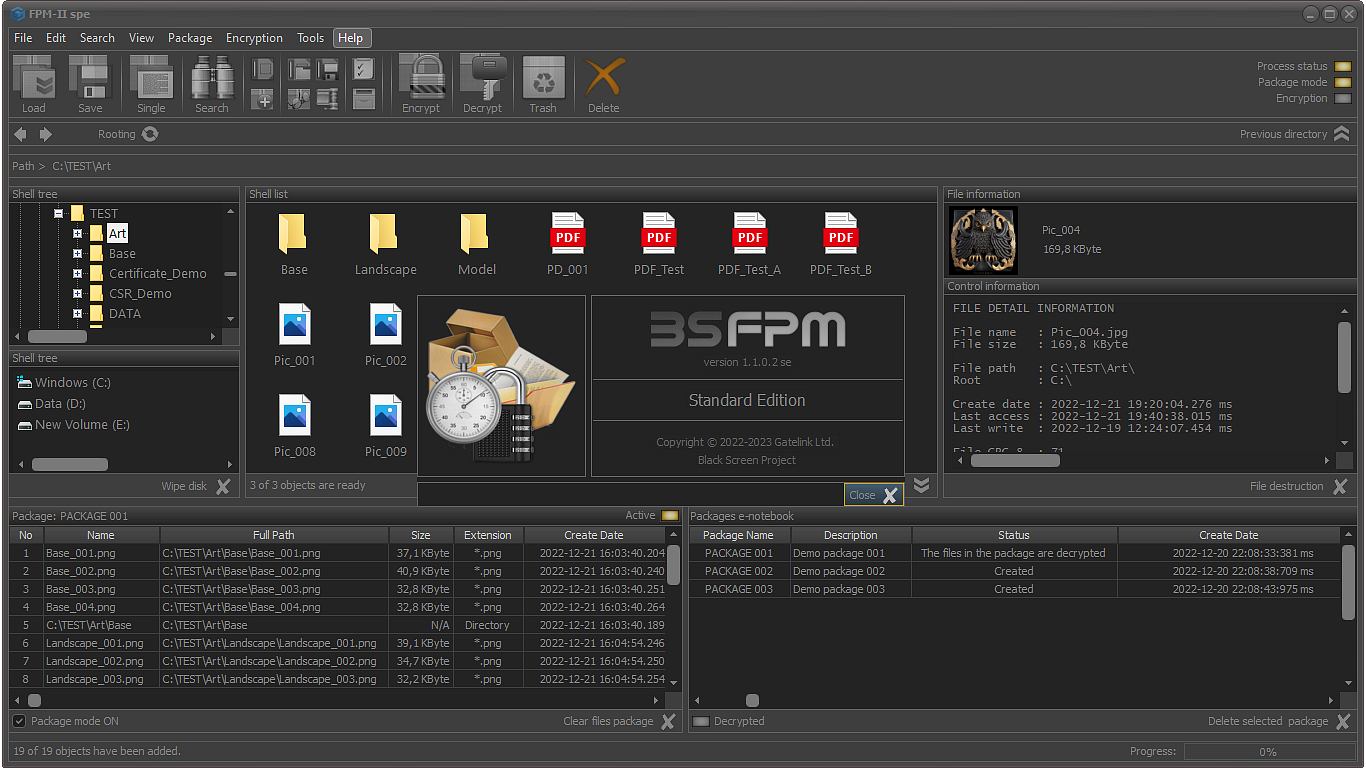
File Package Manager (FPM) is a specialized application for encrypting files and folders located on local, network, server or external data medias.
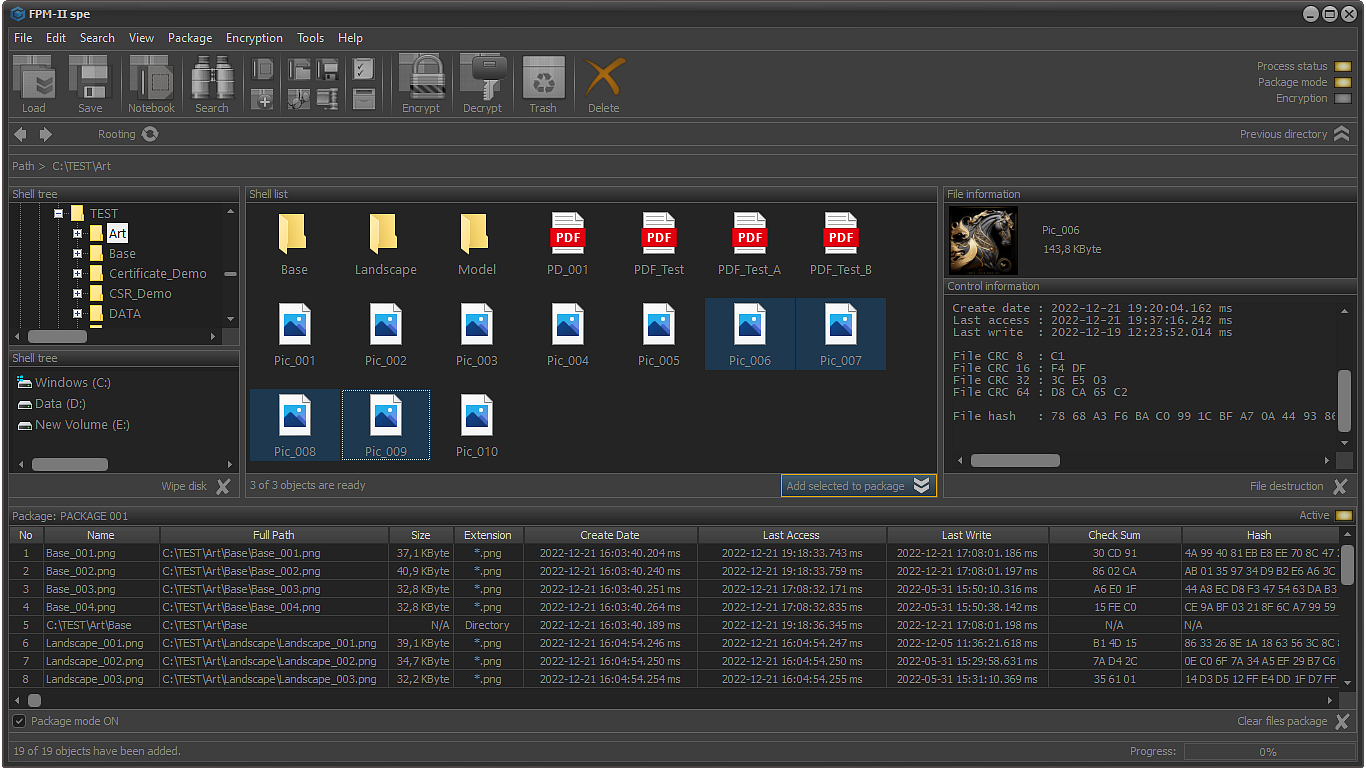
The application allows the following actions:
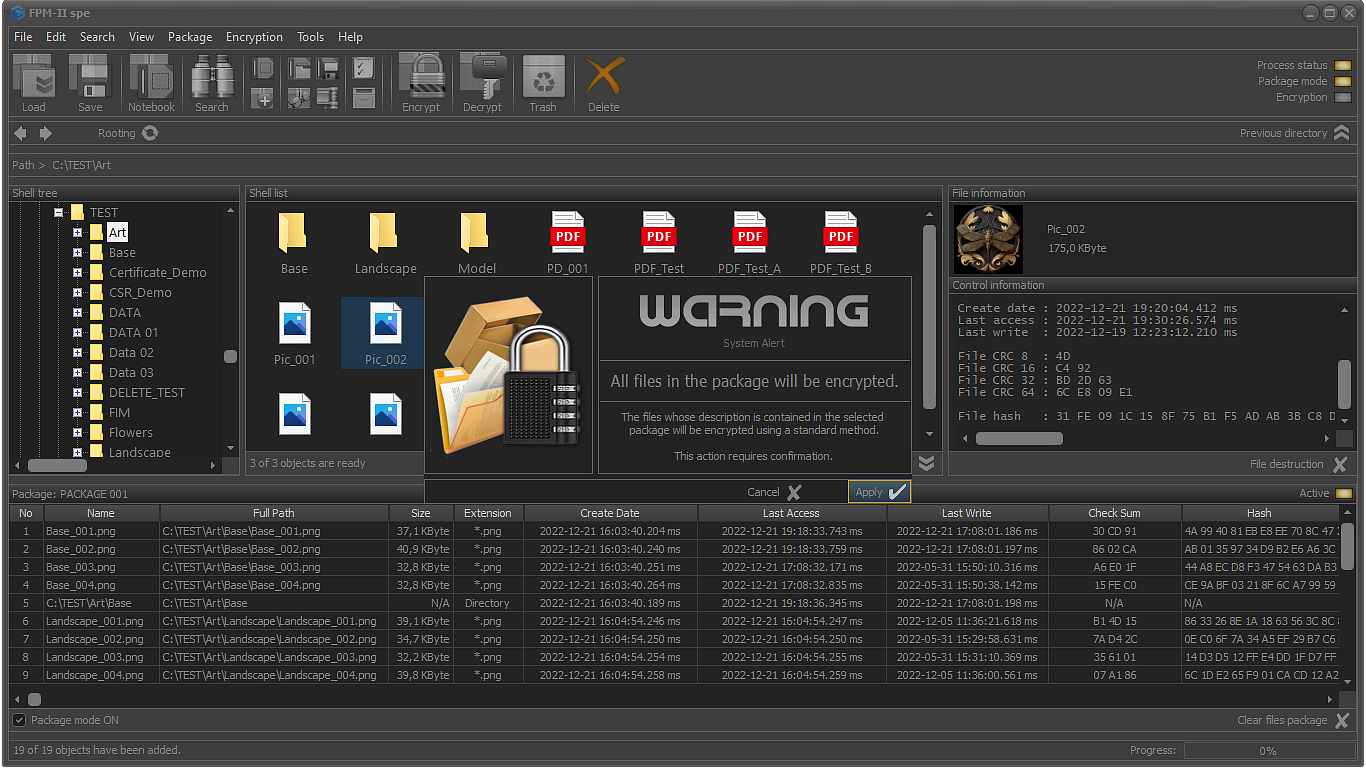
- Encrypting the files in the package;
- Decrypting the files in the package;
- File integrity check;
- File modification control;
- Checking the current status of files and directories;
- Mutual overlapping of the files in the package;
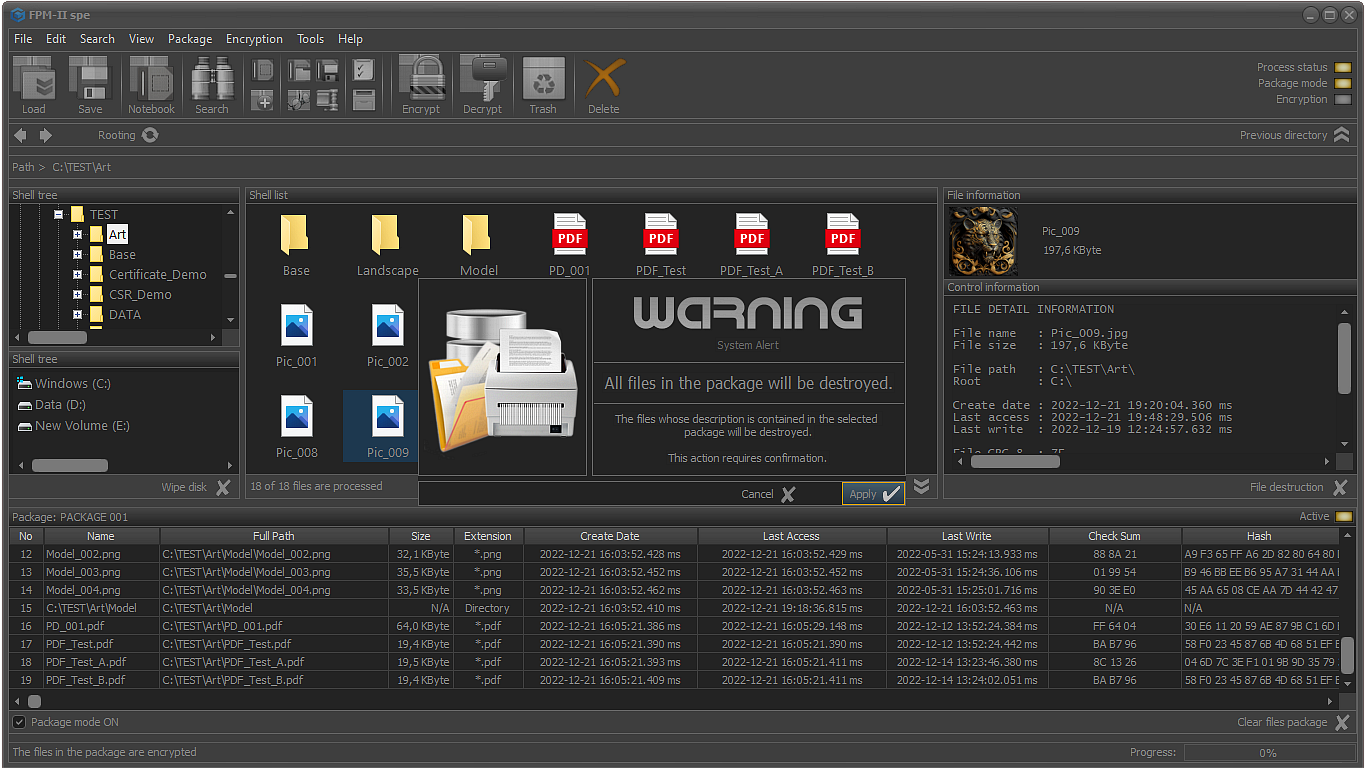
- Shredding and/or sanitizing the files saved in the package etc.
All operations on the files and folders saved in the package are performed only when the files and folders are physically accessible. If they cannot be accessed (deleted, physically inaccessible network drive or other reason), this will be reflected in the packet, recording the time when this finding was made.
If encryption is performed on the files in the package, all accessible files will be encrypted using the selected crypto primitives.
FILE PACKAGE DESCRYPTION
File bundles are spreadsheets that contain meta information about files and directories that are physically located on one or more physical devices.
File packages are a tool for executing meta-scenarios related to processing critical data.
Note: The application can be used independently or as an integrated module of crypto systems such as FPS, Cryptor, FDM, Database Protection System (DPS), Cloud Encryption Manager (CEM), etc.
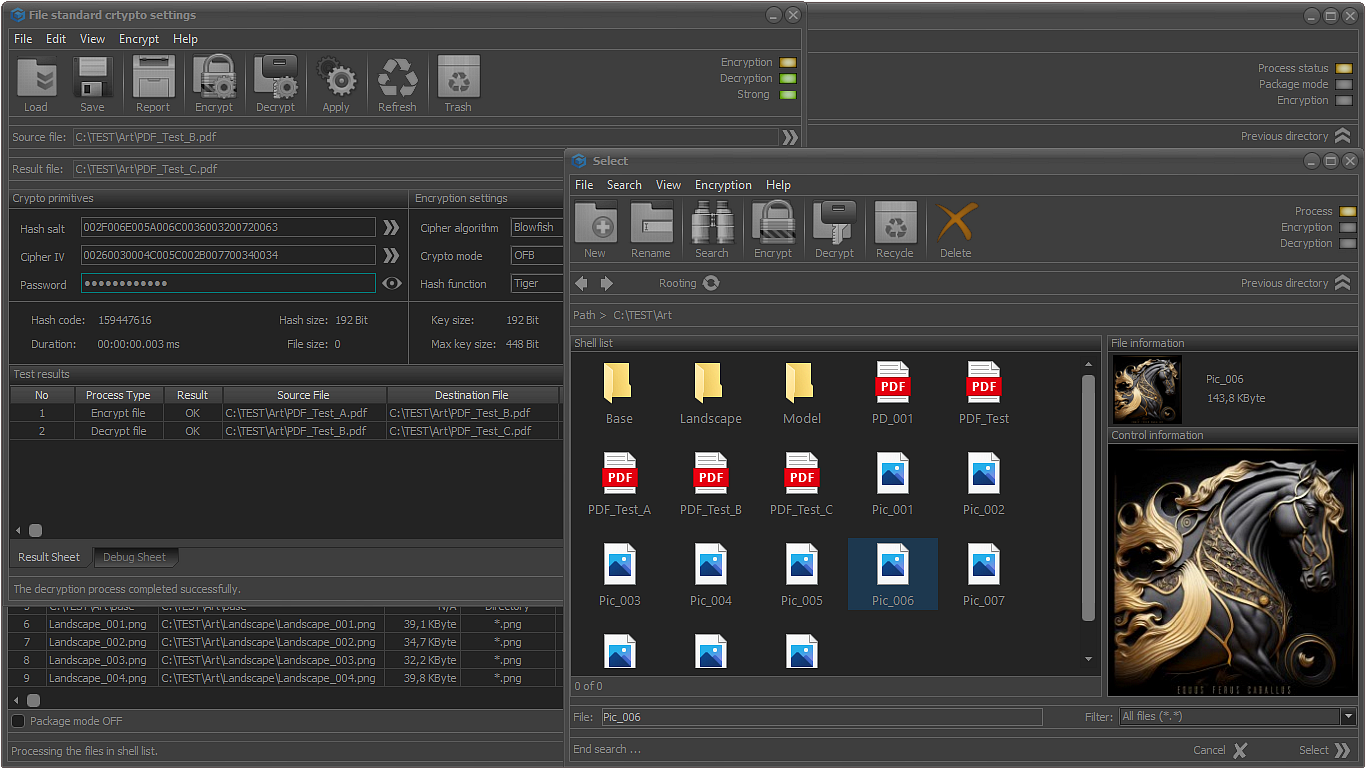
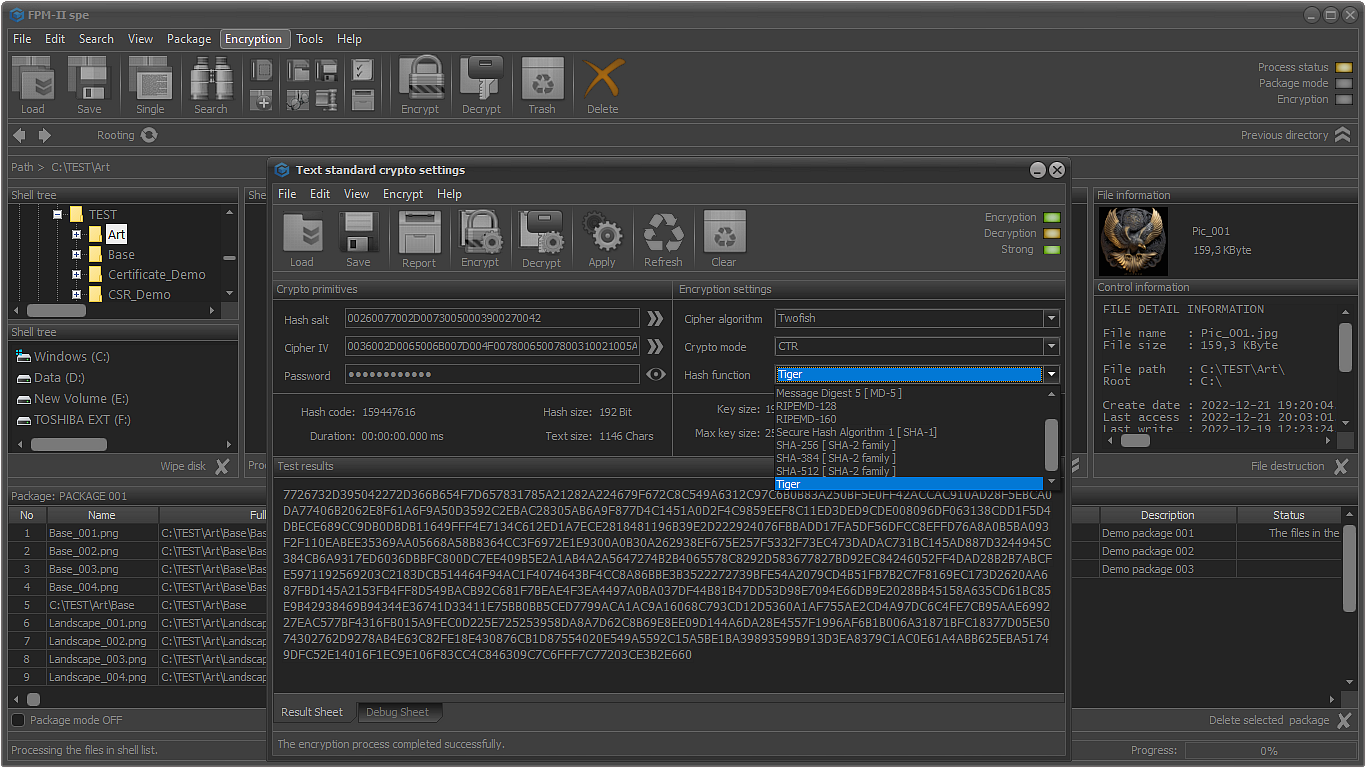
ENCRYPTION ALGORITHMS AND HASH FUNCTIONS
The application includes the following standard encryption algorithms:
- Advanced Encryption Standard (block size of 128 bits, key lengths: 128, 192 and 256 bits)
- Blowfish
- Haval (256 bit, 5 passes)
- CAST-128 (CAST-5)
- CAST-256 (CAST-6)
- Information Concealment Engine (ICE)
- Information Concealment Engine 2 (ICE-2)
- ICE Encrypt
- MISTY-1 (Mitsubishi Improved Security Technology)
- Ron’s Code 2 or Rivest’s Cipher 2 (RC-2)
- Ron’s Code 4 or Rivest’s Cipher 4 (RC-4)
- Ron’s Code 5 or Rivest’s Cipher 5 (RC-5)
- Ron’s Code 6 or Rivest’s Cipher 6 (RC-6)
- Serpent
- Tiny Encryption Algorithm (TEA)
- Twofish
Affordable hash functions:
- Secure Hash Algorithm 1 [SHA-1]
- RIPEMD-160
- Haval [256 Bit, 5 passes]
- Message Digest 5 [MD-5]
- Message Digest 4 [MD-4]
- Tiger
- RIPEMD-128
- SHA-256 (SHA-2 family)
- SHA-384 (SHA-2 family)
- SHA-512 (SHA-2 family)
USED STANDARDS
Standards for Security Categorization of Federal Information and Information, FIPS 199:
- FIPS 200 - Minimum Security Requirements for Federal Information and Information Systems;
- NIST SP 800-60 - Guide for Mapping Types of Information and Information Systems to Security Categories;
- NIST SP 800-53 - Recommended Security Controls for Federal Information Systems;
- NIST SP 800-53A, (Guide for Assessing the Security Controls in Federal Information Systems.
ISO standards:
- ISO 10116: Information Processing — Modes of Operation for an n-bit block cipher algorithm.
- ISO 9797: Data cryptographic techniques — Data integrity mechanism using a cryptographic check function employing a block cipher algorithm.
- ISO 9798-2: Information technology — Security technicues — Entity authentication mechanisms — Part 2: Entity authentication using symmetric techniques.
- ISO 10118-2: Information technology — Security technicues — Hash-functions — Part 2: Hash-functions using an n-bit block cipher algorithm.
- ISO 11770-2: Information technology — Security technicues — Key management — Part 2: Key management mechanisms using symmetric techniques.
Key features
-
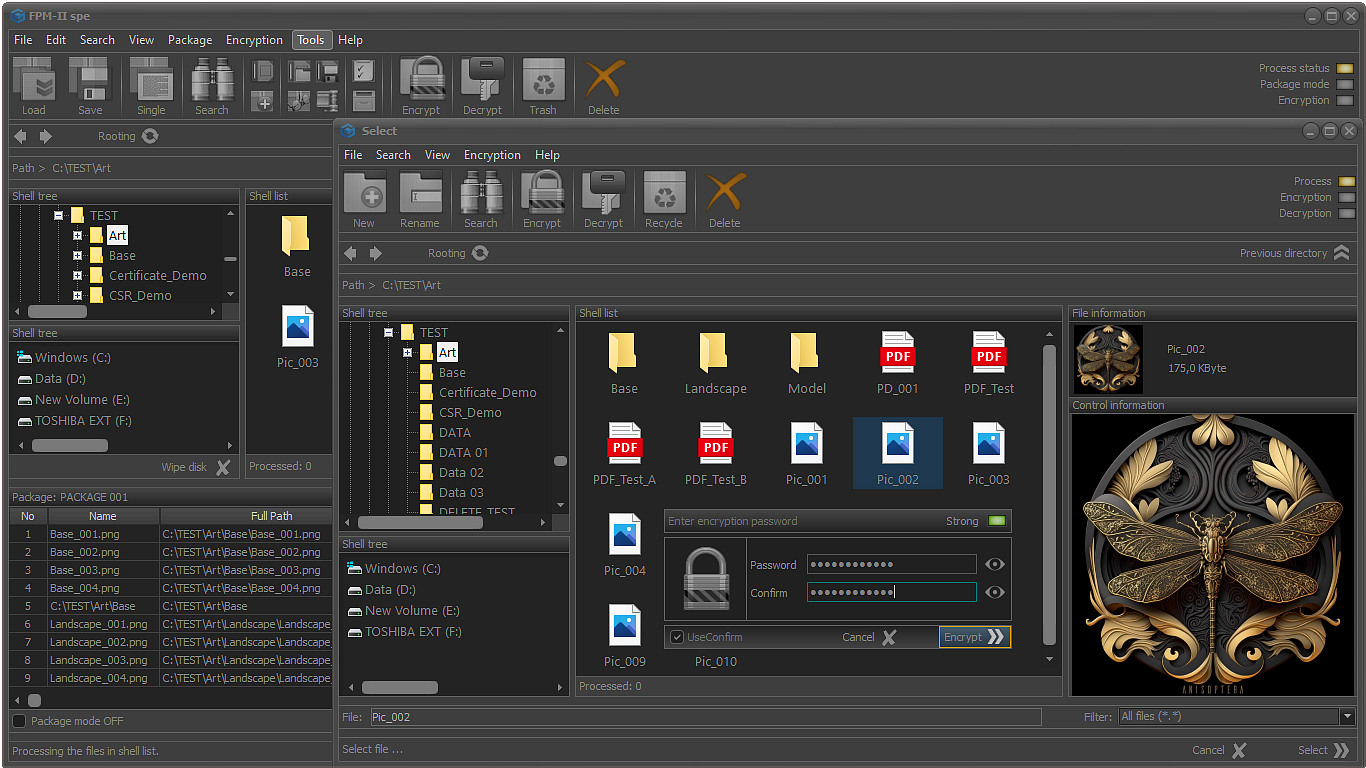
Encrypt files and folders using a combination of cryptographic primitives.
-
Hybrid file and folder encryption using a combination of crypto primitives.
-
Encrypt and decrypt file packages.
-
Encrypt files and folders located on various data storage devices (data servers, network or mobile devices, etc.).
-
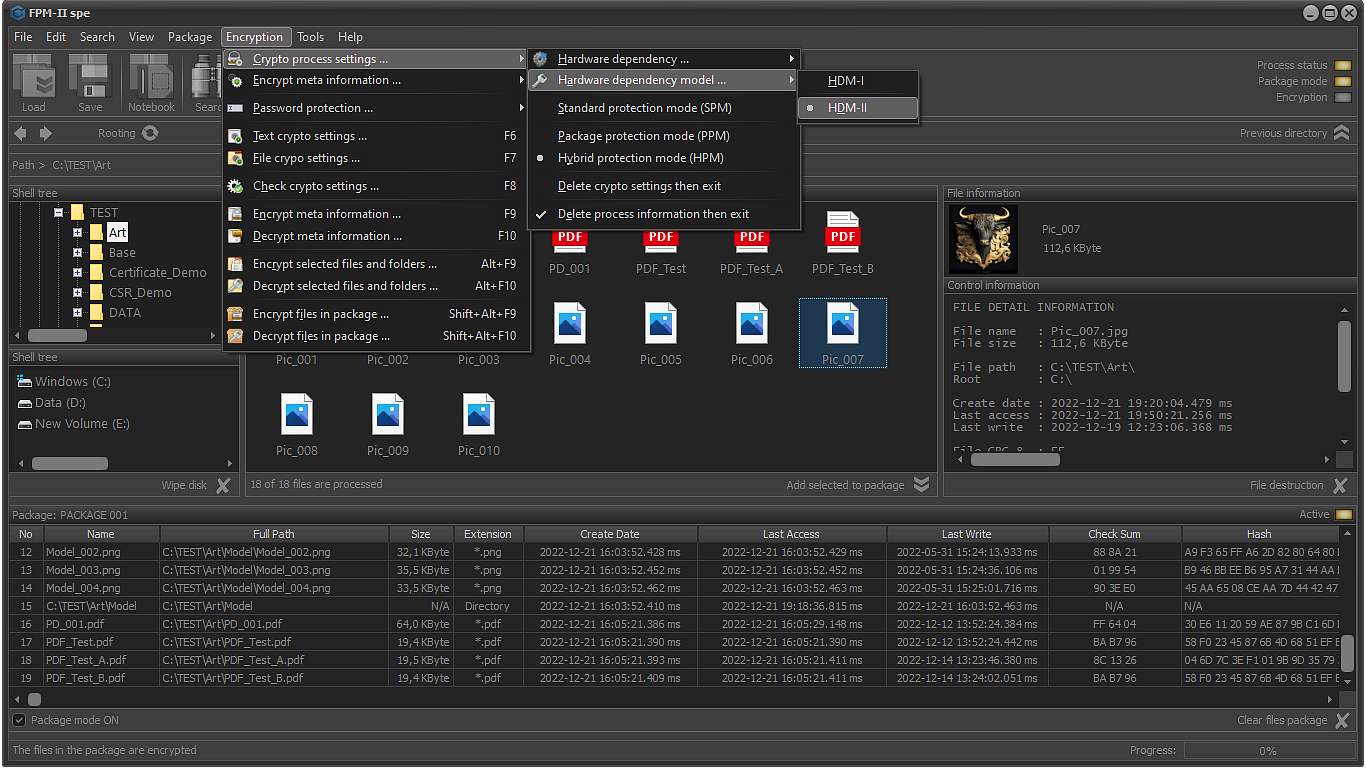
Protection depending used hardware (HDM-I, HDM-II)
-
All meta information encryption
-
The work data selective destruction after the end of the session.
-
BS Standard and Ultra files desroyers.
-
Real time crypto processes control.
-
File integroty monitorinf, FIM.
-
Files and folders shredding functions.
-
Electronic notebooks for file packages.
-
Professional crypto process reports etc.