
Network Penetration Testing - Tools, Methods & Attacks
App details
About Network Penetration Testing - Tools, Methods & Attacks
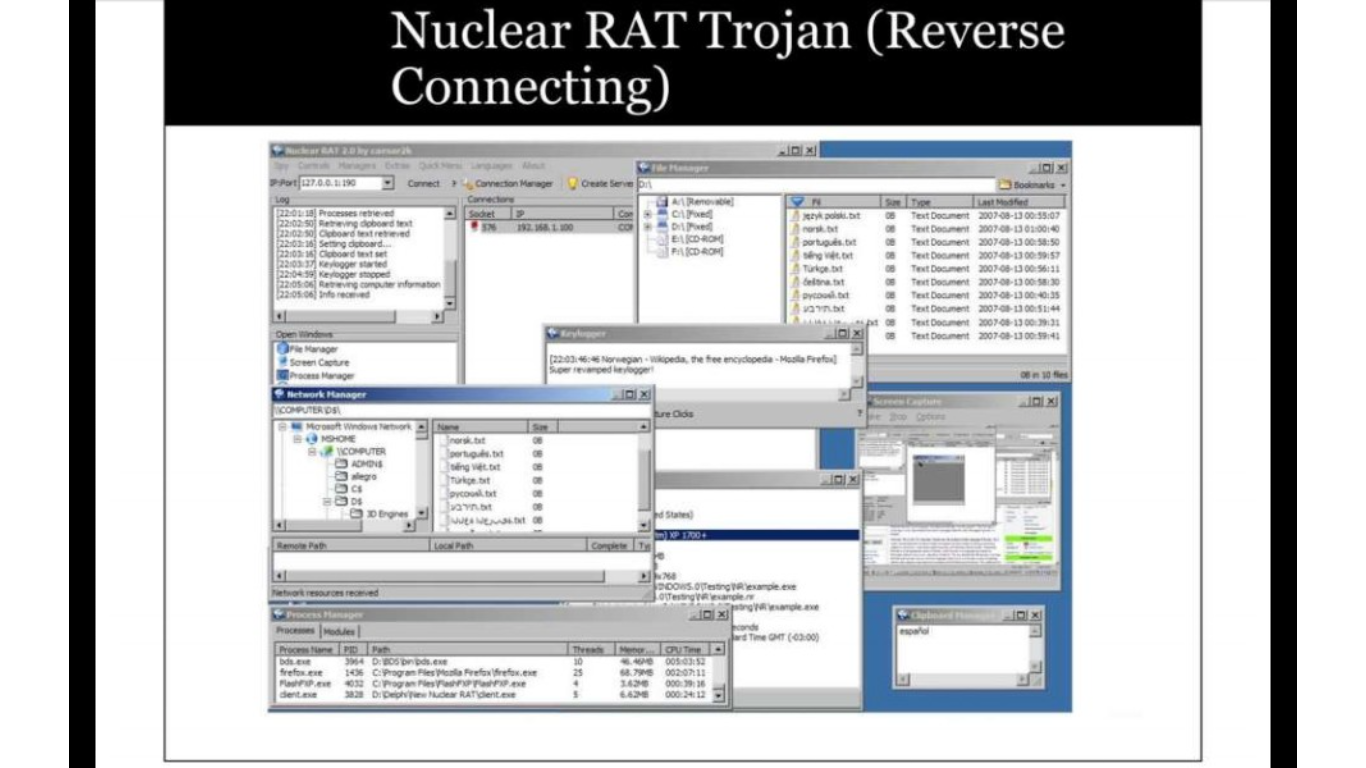
Network Penetration Testing - Tools, Methods & Attacks is a guide on Advanced Web and Mobile Application Penetration Testing. This guide provides information on how to detect Trojans, types of Trojans, ICMP tunnelling & indications of Trojans Attacks.
This guide is useful for beginners and advanced users
There are 10 different sections to this book, laid out as a football playbook The 10 sections are:
-
BeforeGame: This is all about how to set up your attacking machines and the tools we’ll use
throughout the book. -
Before the Start: Before you can run any plays, you need to scan your environment and understand
what you are up against. We’ll dive into discovery and smart scanning. -
The Fast Drive: Take those vulnerabilities which you identified from the scans, and exploiting those systems. This is where we get our hands a little dirty and start exploiting boxes.
-
The Hot Throw: Sometimes you need to get creative and look for the open target. We’ll take a look at how to find and exploit manual Web Application findings.
-
The Lateral Pass - After you have compromised a system, how to move laterally through the
network. -
The Screen - A play usually used to trick the enemy. This chapter will explain some social engineering tactics.
-
The OnPointside Kick - A deliberately short kick that requires close distance. Here I will describe attacks that require physical access.
-
The Sneak - When you only need a couple of yards a quarterback sneak is perfect.
Sometimes you get stuck with antivirus (AV); this chapter describes how to get over those small hurdles by evading AV. -
Special Forces - Cracking passwords, exploits, and some tricks.
-
Post-Game Analysis - Reporting your findings
Before we dig into how to attack different networks, pivot through security controls, and evade AV, I
want to get you into the right mindset. Imagine you have been hired as the penetration tester to test the overall security of a Fortune 500 company. Where do you start? What are you your baseline security tests?
How do you provide consistent testing for all of your clients and when do you deviate from that line? This is how I am going to deliver the messages of this guide.
Key features
-
[Ethical] Social Engineering techniques and preventions
-
[Ethical] Networks Penetration Tools
-
Installation of Virtual Environments
-
How to use high level penetration tools like SMBexec, Veil, Burp, PowerSploit etc
-
Network external scanning & discovery scripts
-
Web Applications Scanning & Spider Applications
-
Executing metasploits and WarFTP
-
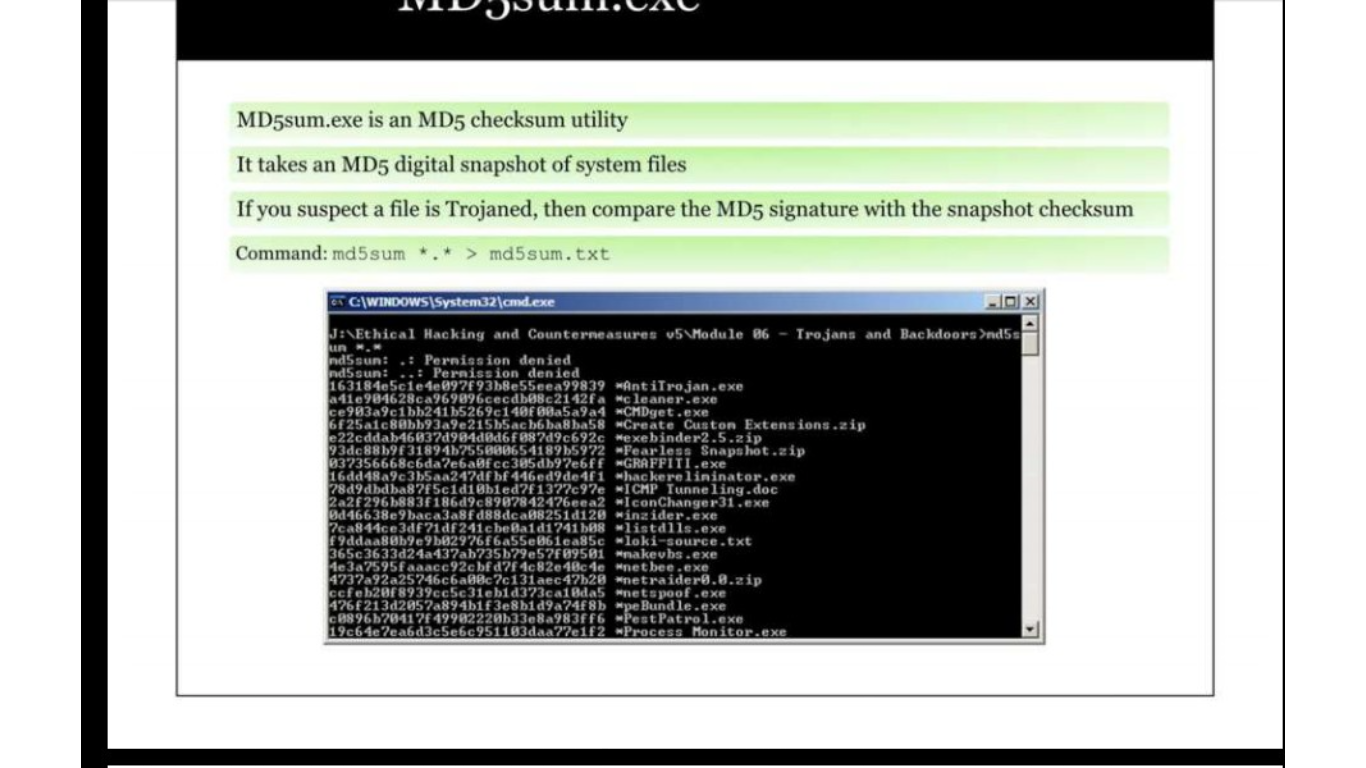
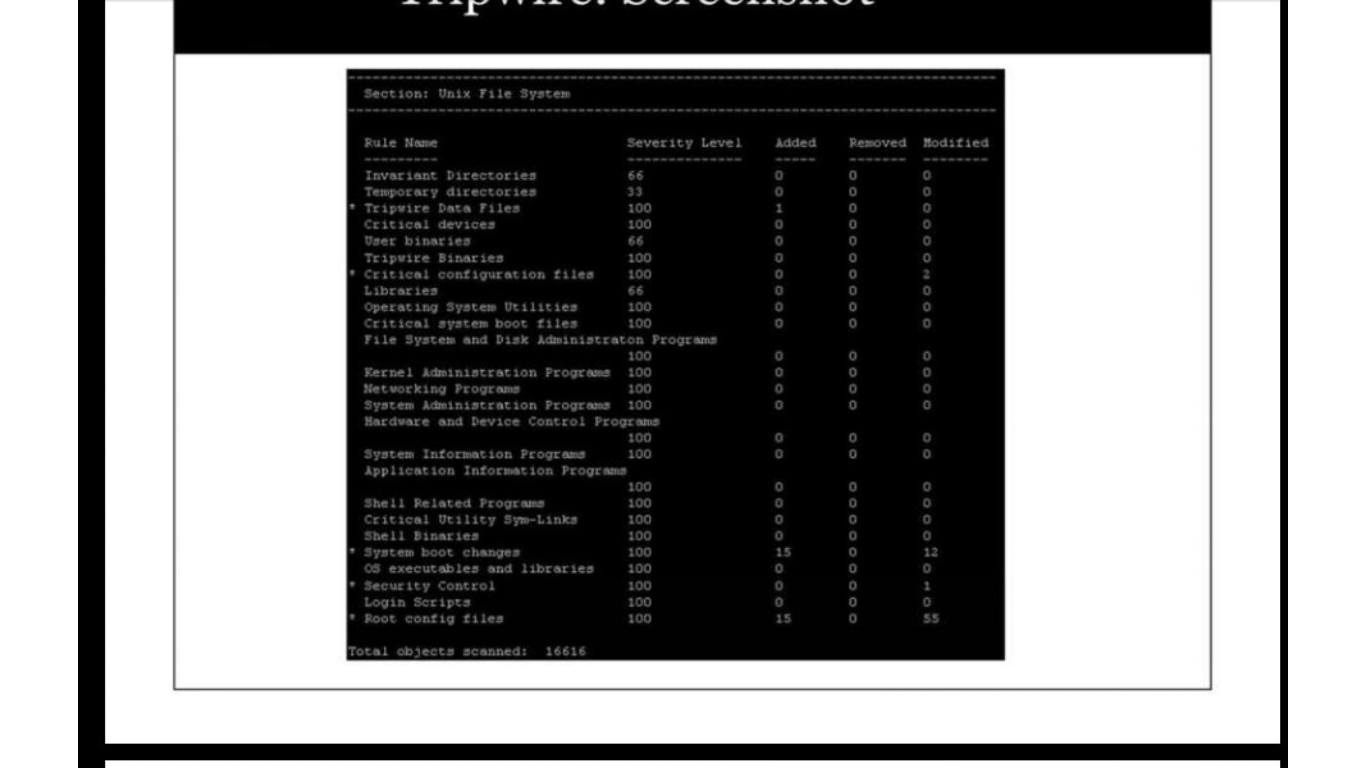
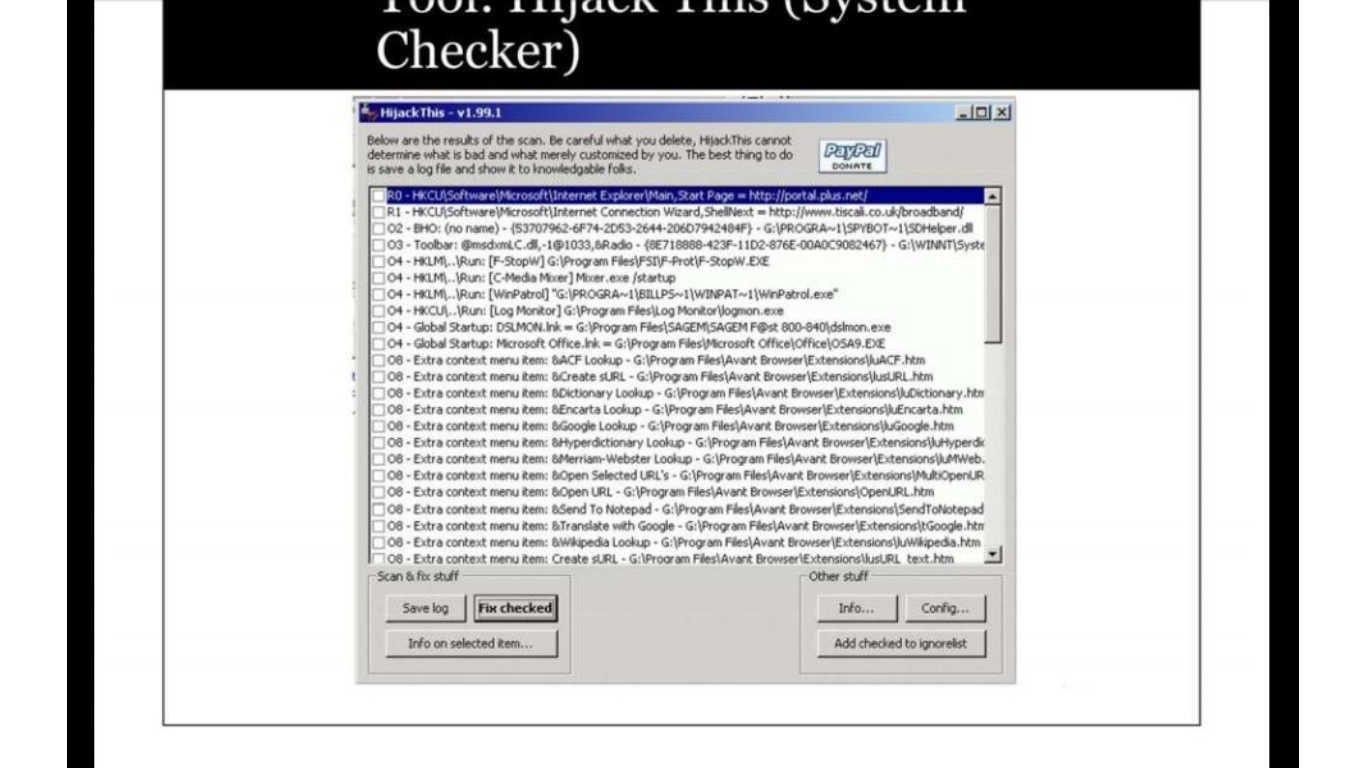
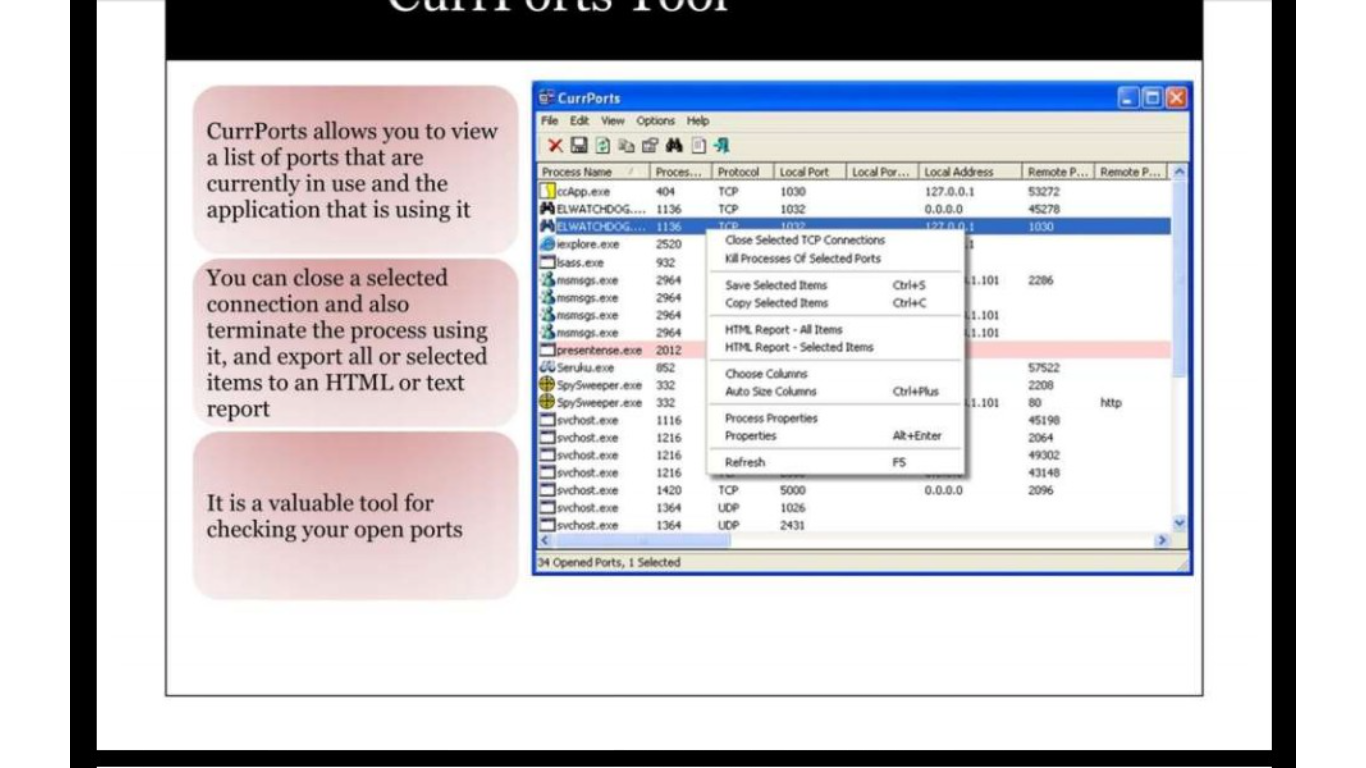
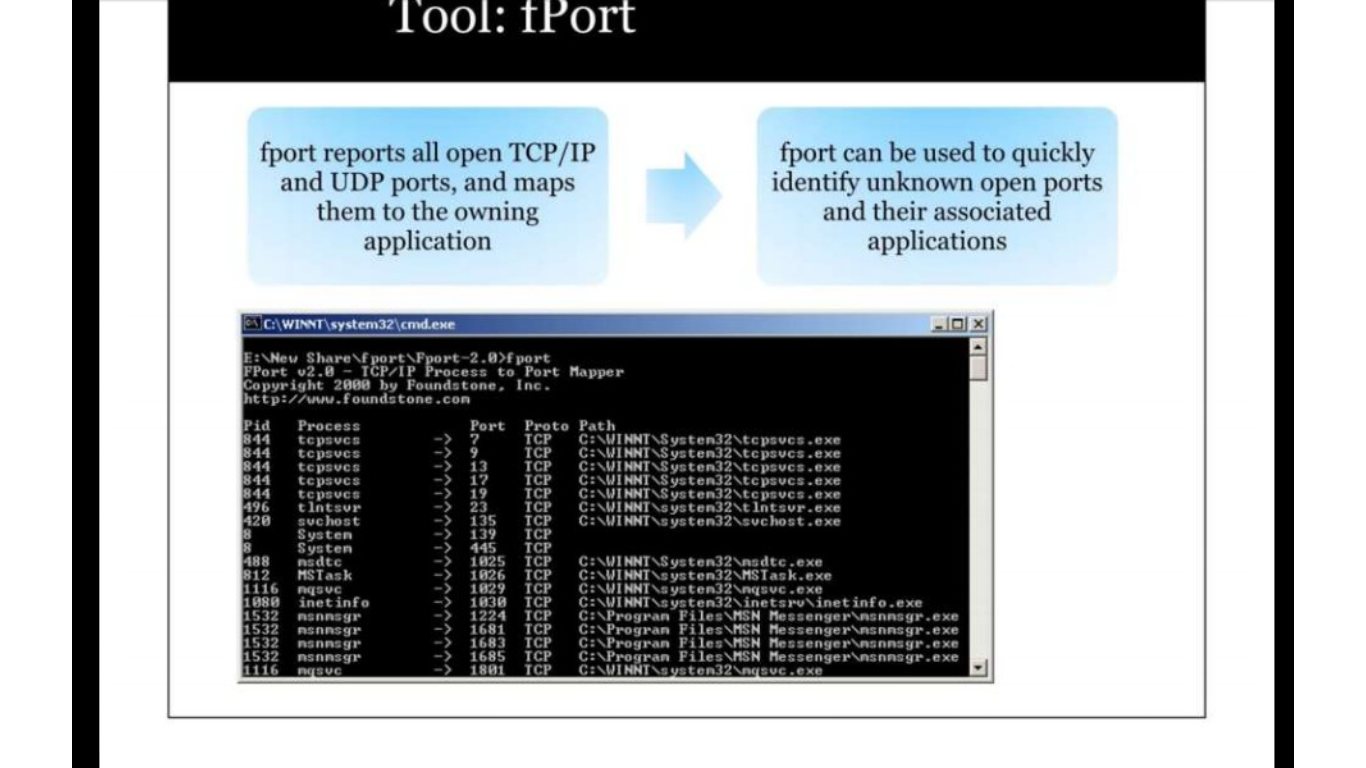
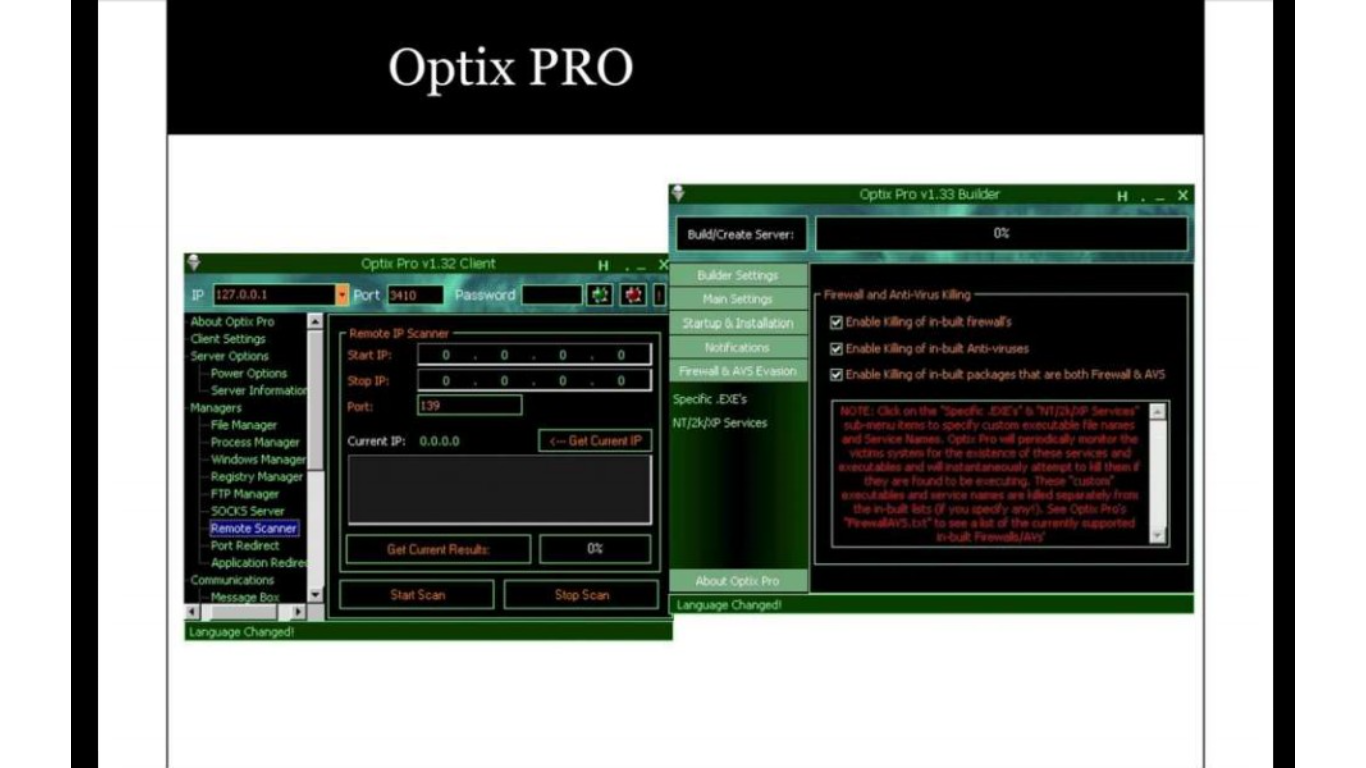
Tools for detecting trojan
-
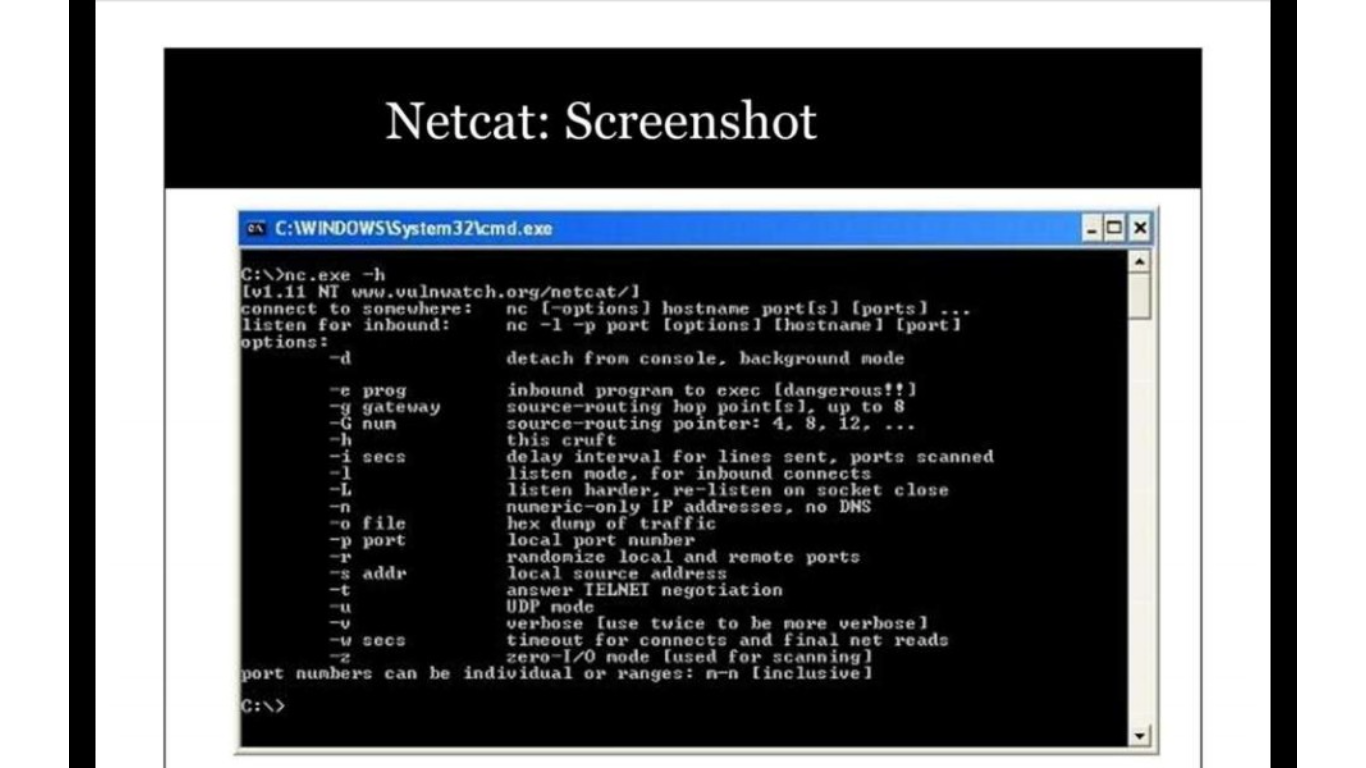
Overt & Covert Channels
-
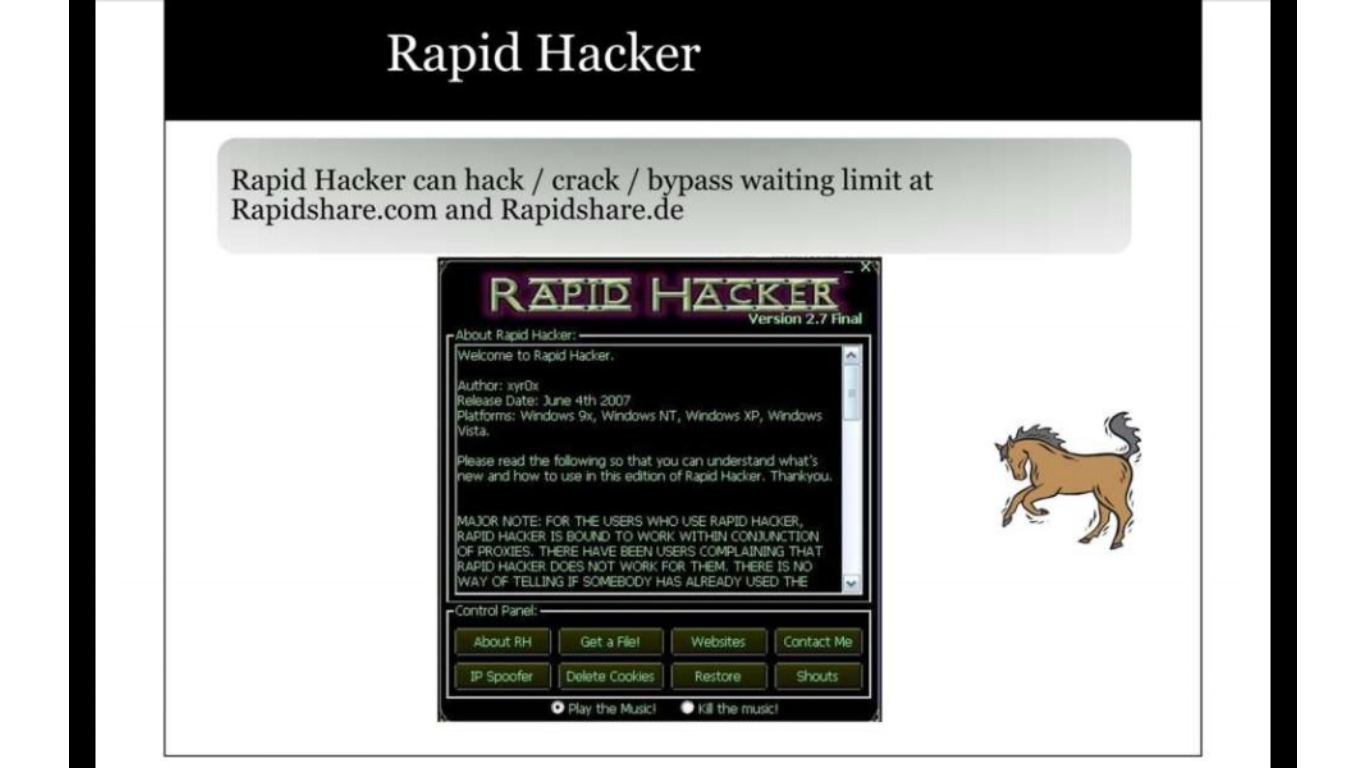
Anti Trojans & Avoiding Trojan infection
-
ICMP Tunneling
-
Wrappers