Network Server Penetration Testing - Tools and Resources
Rating
0
Reviews
0
App details
About Network Server Penetration Testing - Tools and Resources
This is an Advanced Network Server Penetration Testing Guide which provides detailed guide on Modern Modes of
Network Server Penetration Testing.
The content of this guide include:
- Hacking concepts and phases
- Passive reconnaissance & Active reconnaissance
- Port scanning & Network scanning
- Vulnerability scanning & Maintaining access
- White box pentesting, Black box pentesting & Gray box pentesting
- Red teaming, Blue teaming & Purple teaming
- Using theHarvester tool for Open Source intelligence gathering.
- Installing Nexpose for Modern Server Penetration Testing
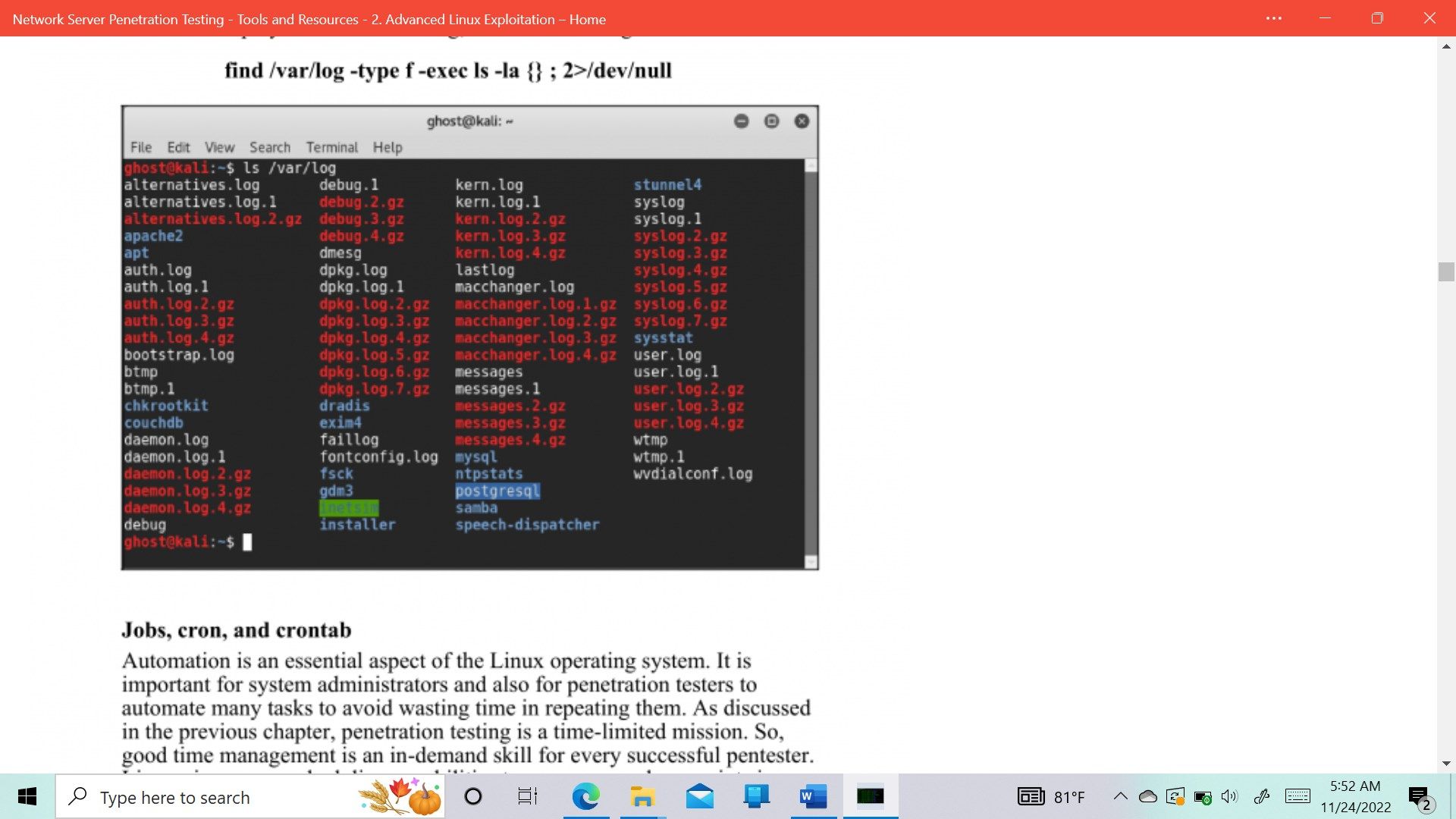
- Advanced Linux Exploitation
- Linux attack vectors - Network, Host & Application Threats
- Linux enumeration with LinEnum
- OS detection with Nmap
- Exploiting Linux services - X11 service, Wildcards, SUID abuse & Linux kernel exploitation
- Linux privilege checker
- Linux kernel exploitation
- UserLand versus kernel land
- Linux kernel vulnerabilities
- Memory corruption & Kernel Stack vulnerabilities
- Linux Exploit Suggester
- Linux return oriented programming
- Linux hardening
- Corporate Network and Database Exploitation
- Insecure SNMP configuration
- Database server exploitations
- TCP communication
- ICMP scanning
- SSDP scanning
- UDP Scanning
- Host-based & Network-based Intrusion detection systems
- Machine learning for intrusion detection
- Insecure SNMP configuration
- DNS security
- DNS attacks
- Sniffing attacks - ARP Poisoning & MAC spoofing
- WireShark & DDoS attacks - SYN flooding, ICMP flood attack
- Defending against DDoS attacks
- Software-Defined Network penetration testing
- SDN attacks & SDNs penetration testing
- Attacks on database servers - Excessive privileges, SQL injection, Weak authentication & Exposure of backup data
- Active Directory and Kerberos - Active Directory attacks
- Lightweight Directory Access Protocol
- PowerShell and Active Directory
- Using PowerView for Active Directory Attack
- Dumping all domain credentials with Mimikatz
- Dumping LSASS memory with Task Manager (get domain admin credentials)
- Dumping Active Directory domain credentials from an NTDS.dit file
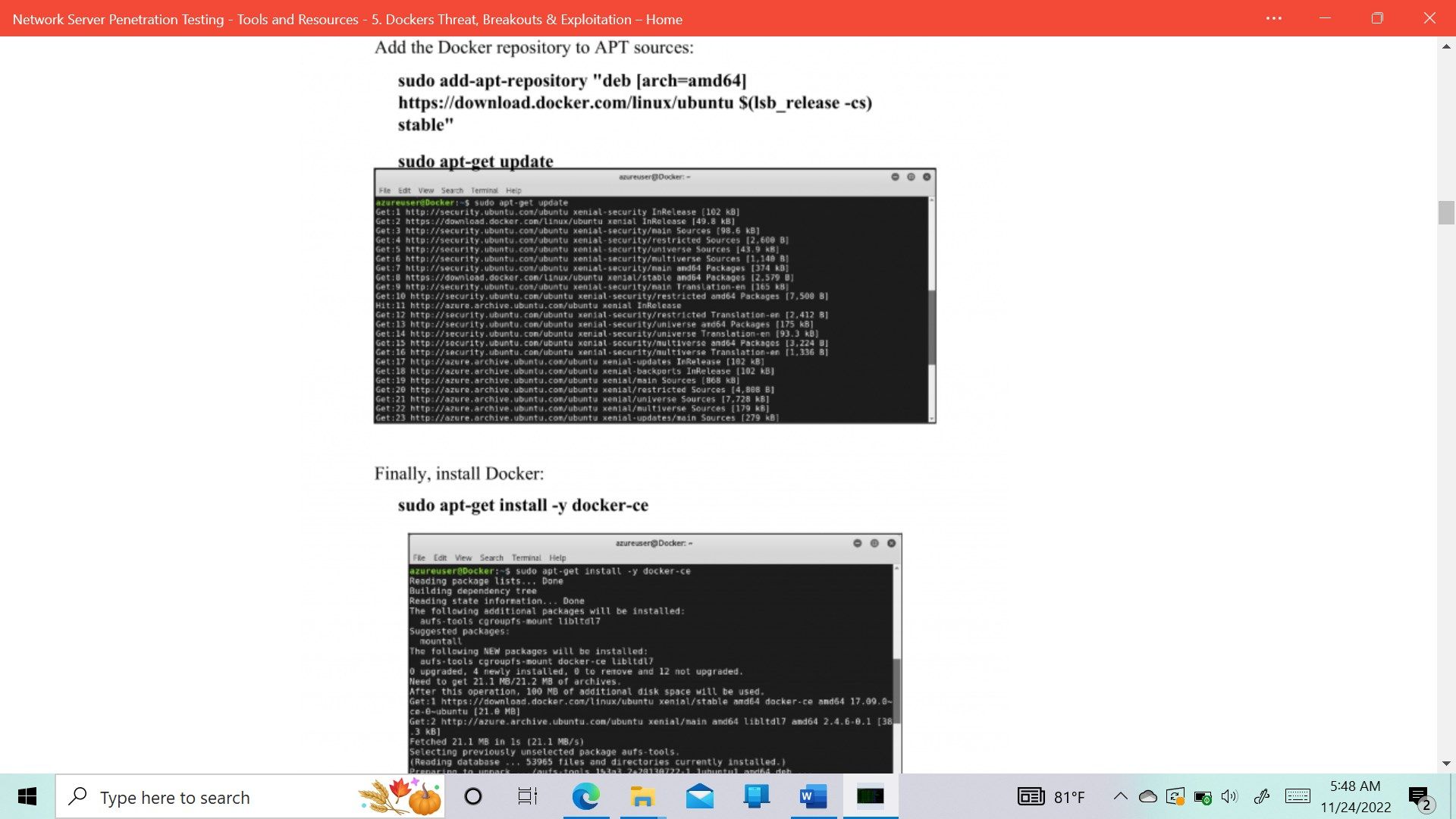
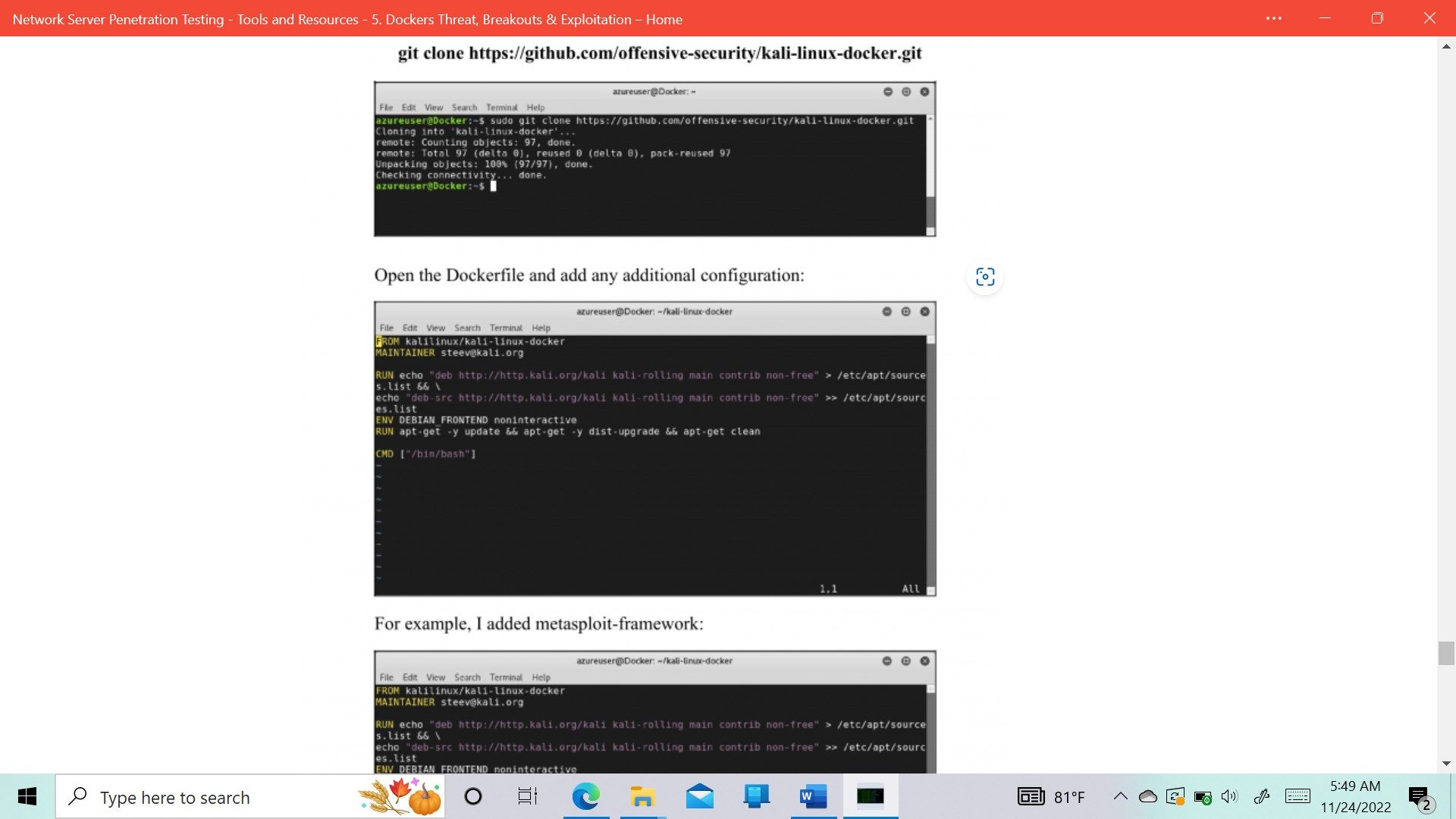
- Docker & Kernel Exploitation
- Building a penetration testing laboratory
- Exploiting Git and Continuous Integration Servers
- Installing Jenkins
- Continuous integration attacks
- Continuous integration server penetration testing
- Continuous security with Zed Attack Proxy
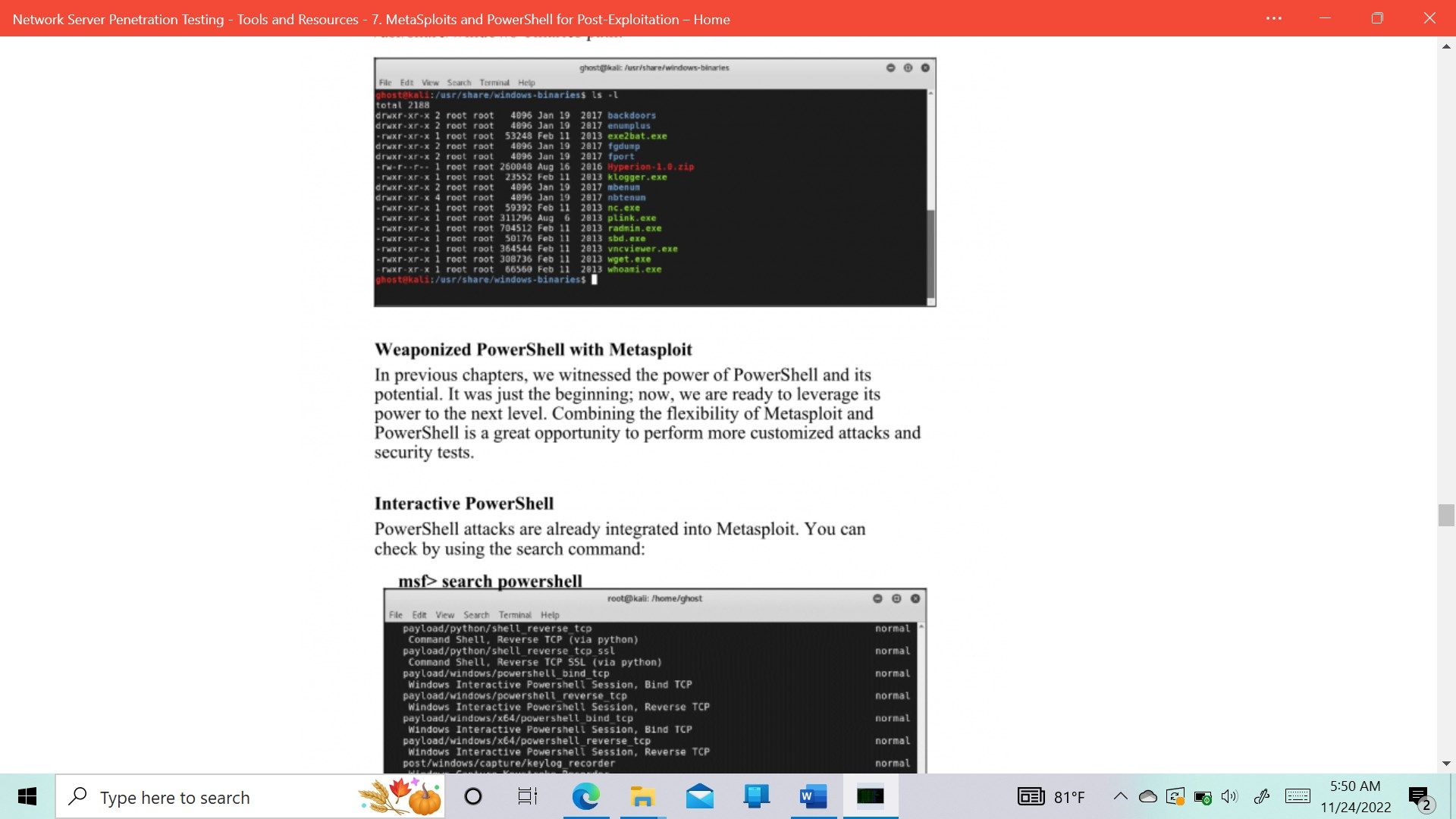
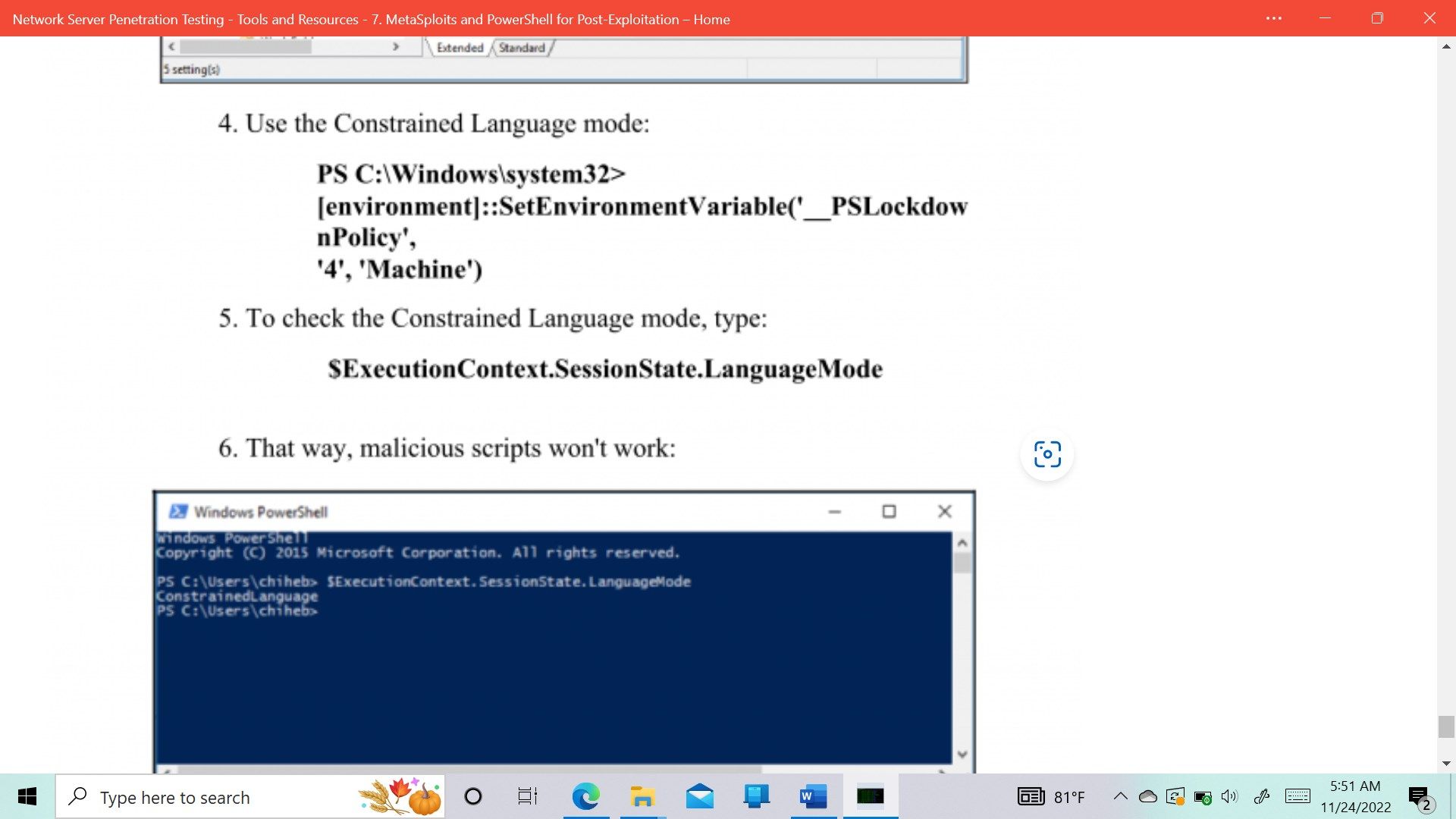
- Metasploit and PowerShell for Post-Exploitation
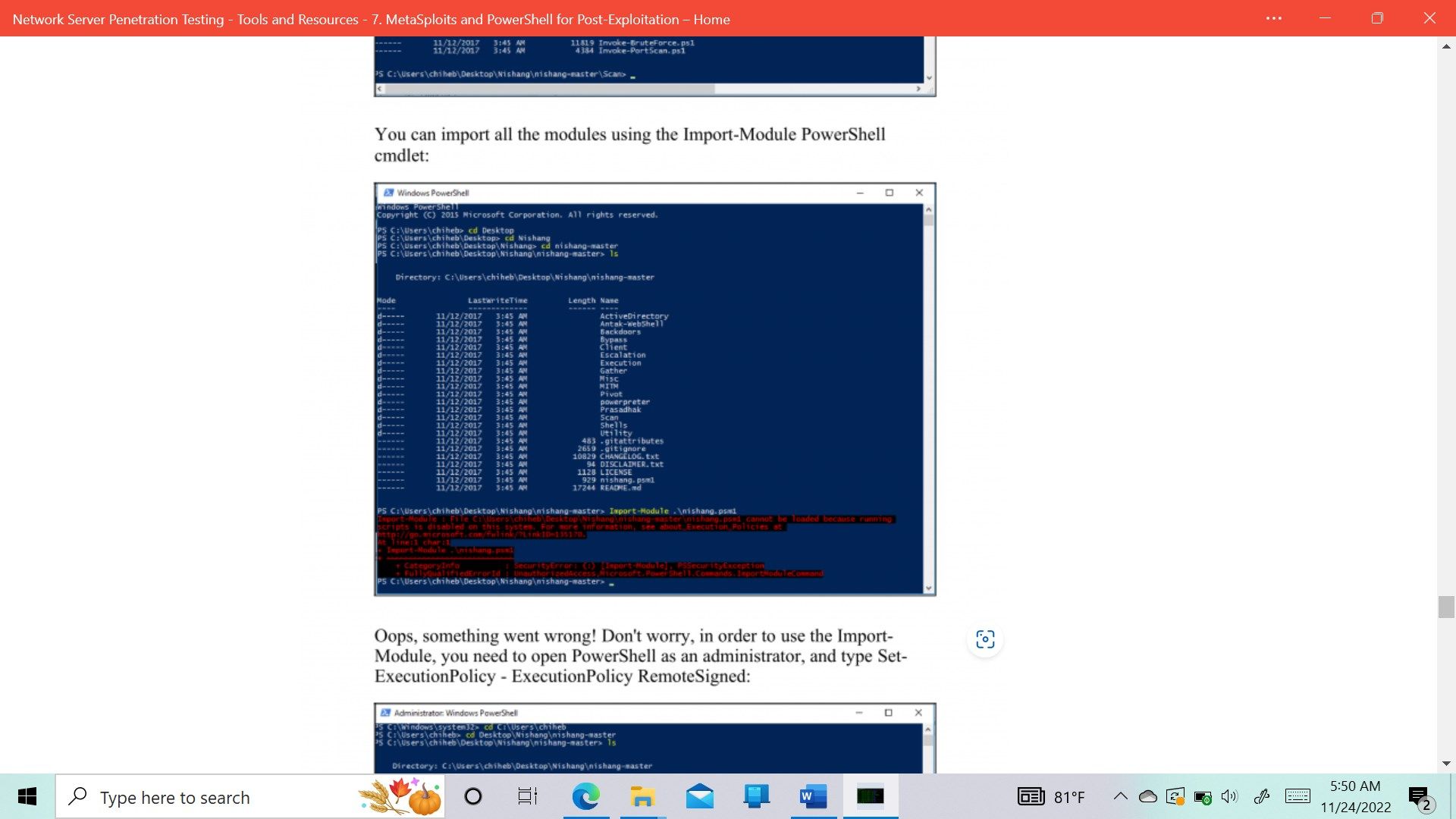
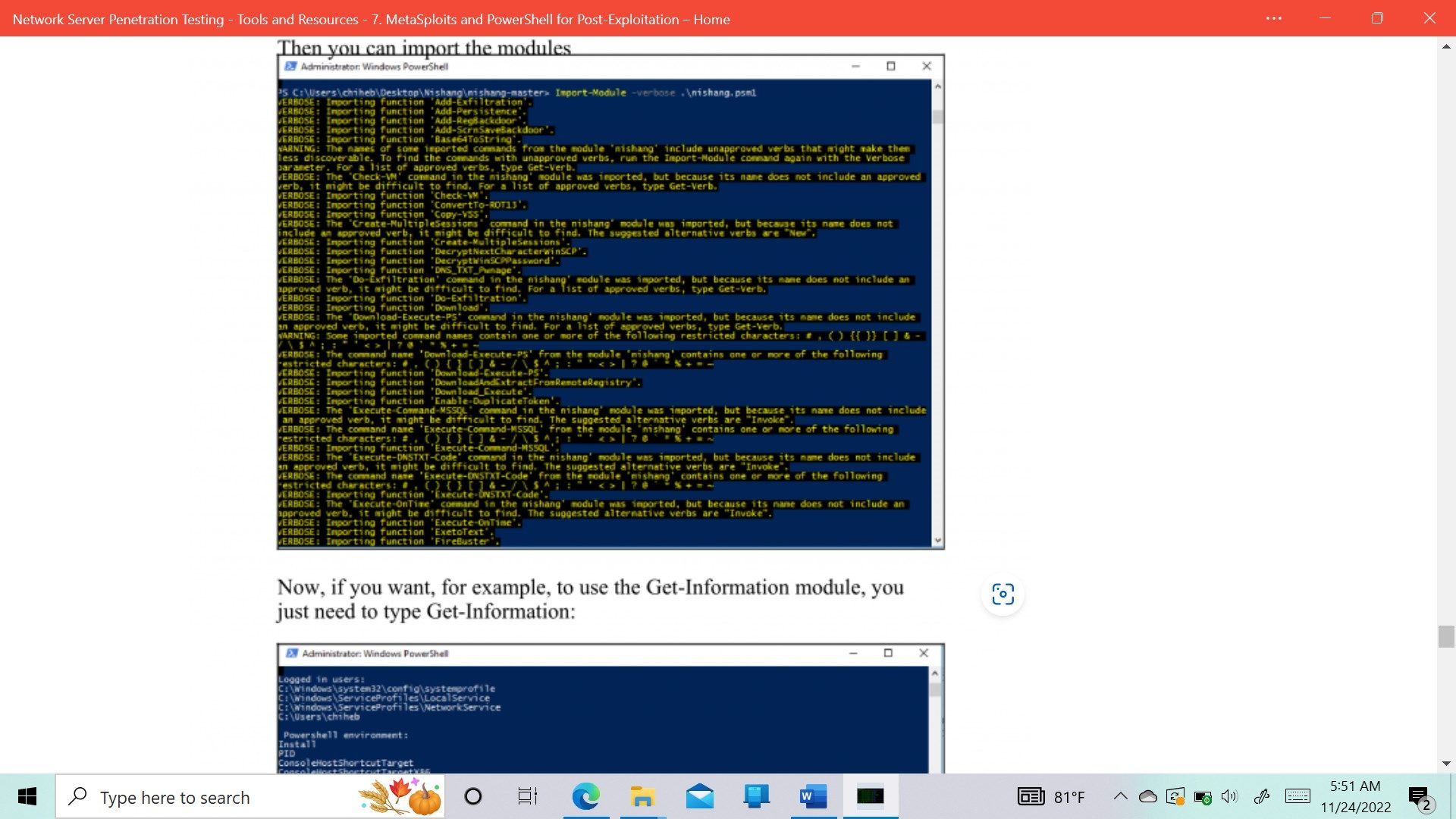
- Nishang PowerShell for penetration testing and offensive security
- Dissecting Metasploit Framework
- Bypassing antivirus with the Veil-Framework
- Writing your own Metasploit module
- Weaponized PowerShell with Metasploit
- PowerSploit - AntivirusBypass, Exfiltration, Persistence, PowerUp, PowerView
- Defending against PowerShell attacks
- VLAN Exploitation
- MAC attack
- DHCP attacks
- DHCP starvation
- Rogue DHCP server
- VLAN hopping attacks
- Spanning Tree Protocol attacks
- VoIP Exploitation
- RTP/RTCP
- Secure Real-time Transport Protocol
- Eavesdropping
- SIP registration hijacking
- Spam over Internet Telephony
- VoLTE attacks
- SiGploit – Telecom Signaling Exploitation Framework
- Insecure VPN Exploitation
- Cryptographic attacks - Brute force attack (BFA) & Dictionary attack, Birthday attack,
- Routing and Router Vulnerabilities
- Exploiting routing protocols
- OSPF attacks
- MaxAge LSAs, Seq++ attack, Persistent poisoning & Internet of Things Exploitation
Key features
-
VLAN N Exploitation
-
MAC Attacks
-
DHCP attacks
-
VLAN Hopping attacks
-
Spanning Tree Protocol Attacks
-
Advanced Linux Exploitation