
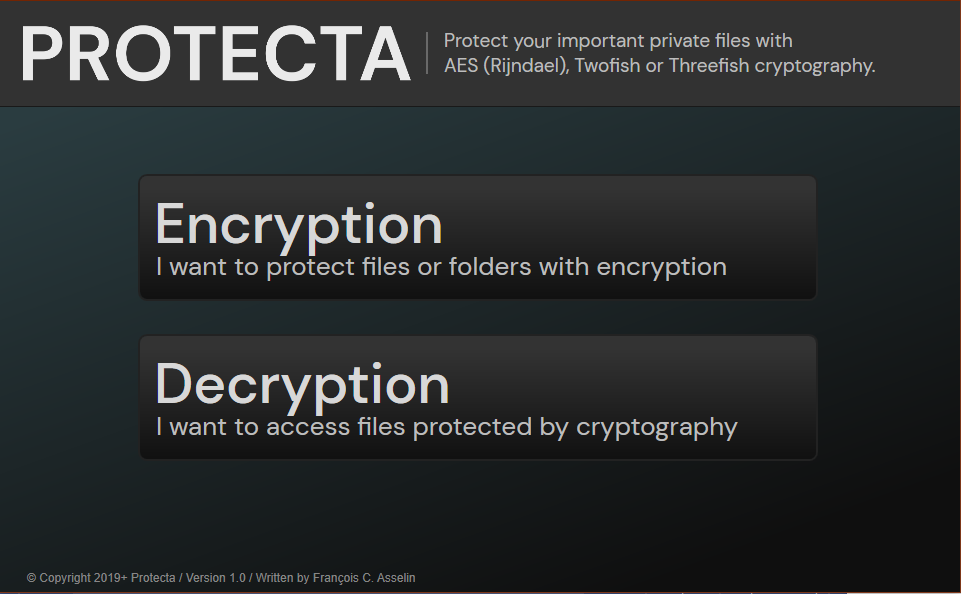
Protecta Encryption Software
App details
About Protecta Encryption Software
Protect your important private documents with strong AES (Rijndael), Twofish or Threefish cryptography using an intuitive easy-to-understand software interface.
-
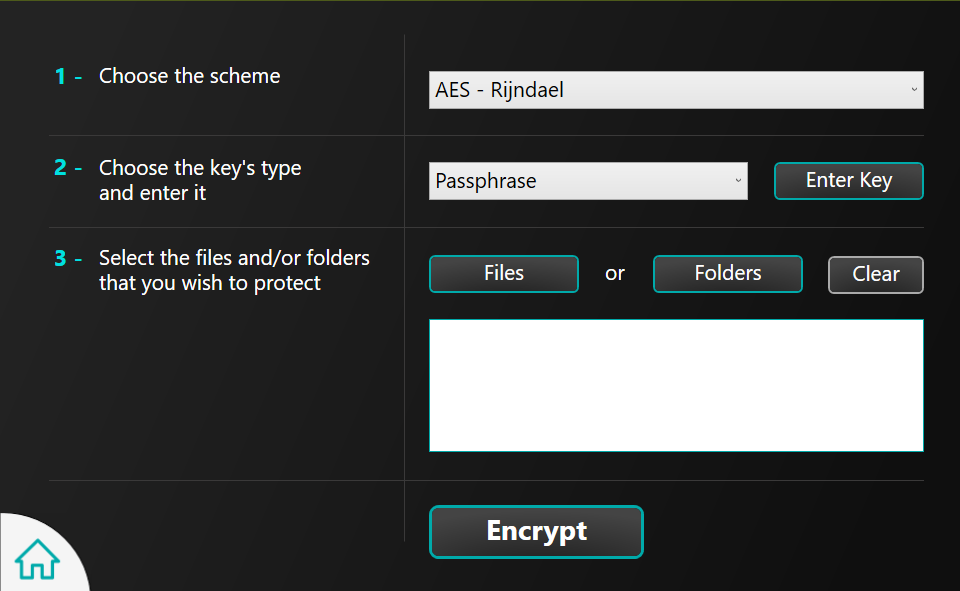
Multiple files and folders can be encoded at once.
-
Any computer file can be used as a key when keyfile is selected since it is the keyfile’s hash value that is applied. Same with passphrases, only the hash value is applicable.
-
This application has been tested successfully with files weighing up to 25GB.
-
All files and folders are first compressed before encryption.
-
Temporary files and passphrases are wiped from the hard drive and memory after each usage. However, the original files are left intact. An option to wipe the original files after usage may be included in a future version.
-
The output file is in a (*.prota) special file extension format which also contains information used in two-step data integrity verification. Note: This information does not include information about the key’s type nor the encrypting cipher used. Encoding autodetection could be added at a later date upon request, but leaving these details blank provides additional security for the protected files.
-
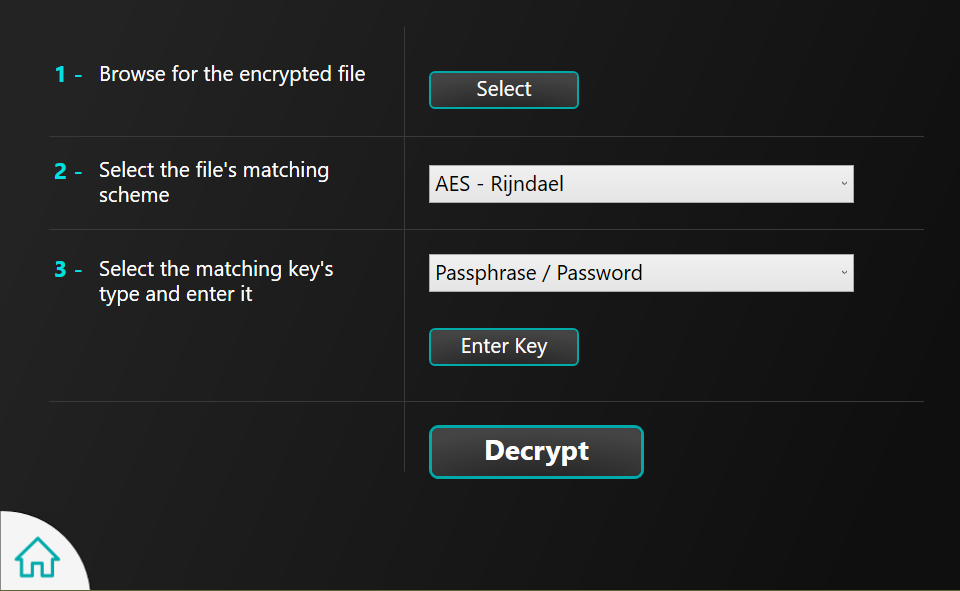
Note: This software application can only decrypt files that have been protected by PROTECTA.
-
For more information concerning the key sizes / block sizes and the encryption modes, please contact the author. These may be rendered configurable in next software versions.
-
Producing self-decrypting-upon-key-entry executable files may be made available at a later date.
-
Advanced options such as changing block chaining modes, key sizes and block sizes may be made available at a later date.
Have any questions, suggestions or concerns? Please contact the author.
Please be kind and leave a review:)
Key features
-
Strong encapsulating cryptography
-
Multiple key types
-
Integrity verification
-
Encrypted contents are first compressed
-
Works with large files
-
AES
-
Twofish
-
Threeefish