
SSharing Free (Store)
App details
About SSharing Free (Store)
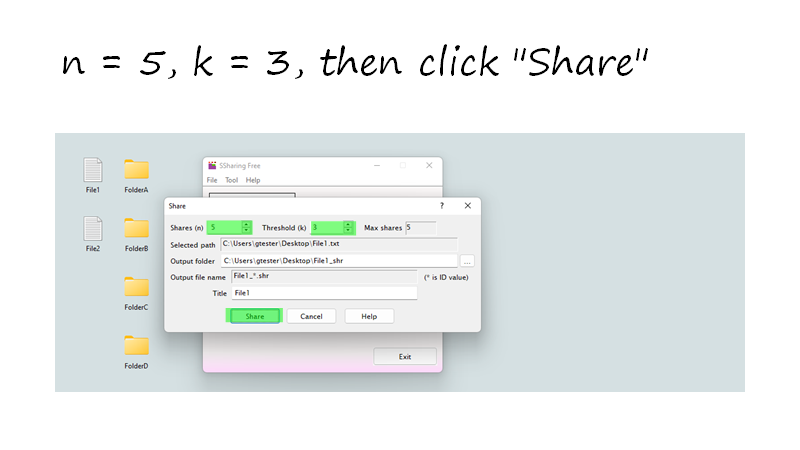
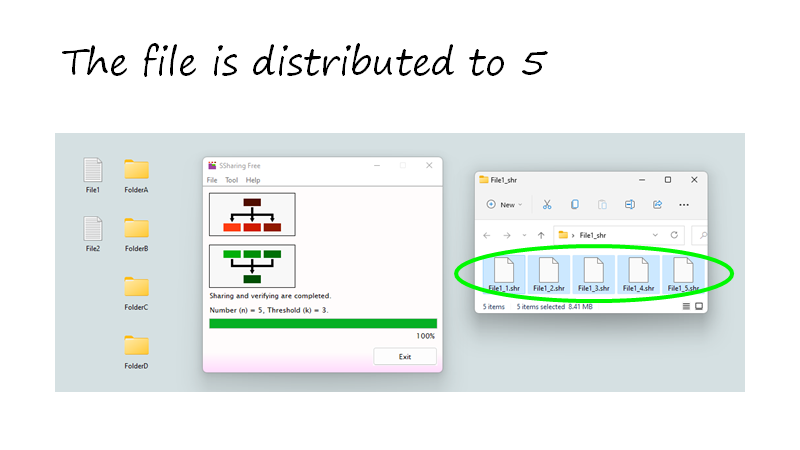
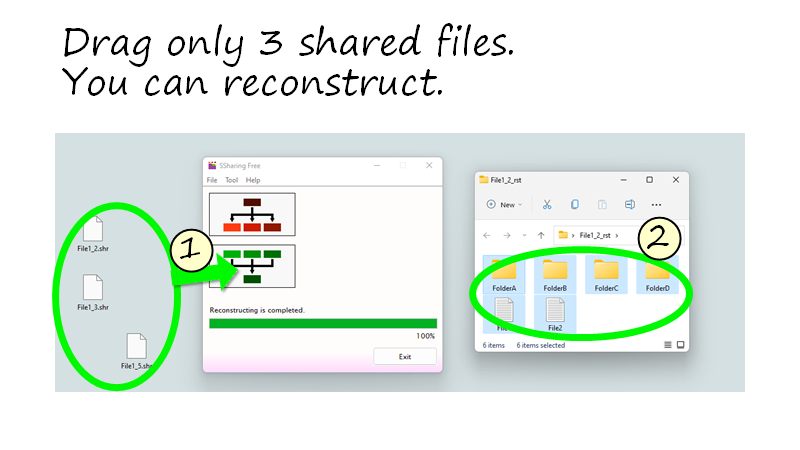
Secret sharing is a different encryption than the password method. If it is distributed to 5 with (k, n) = (3, 5), 3 information is needed to restore the original information. Since it cannot be restored without 3 or more information, there is no risk of unauthorized use even if one or two are leaked. On the contrary, if you have three, you can restore it, so even if two are damaged, you can restore it.
The theory of (k, n) threshold secret sharing was proposed in 1979. However, it was not generally used due to its large storage capacity. “SSharing” is a practical (k, n) threshold secret sharing utility.
-
This application is (k, n) Threshold Secret Sharing Scheme Utility.
-
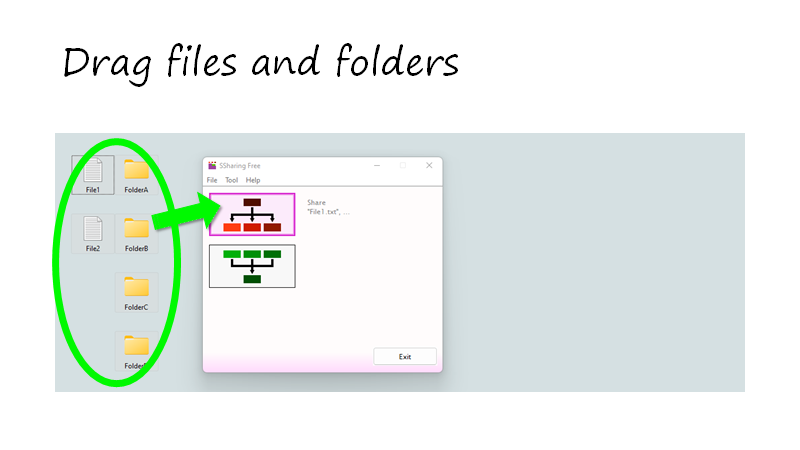
Share into multiple files.
-
The shared file is encrypted.
-
You can not reconstruct the original file in a single shared file.
-
You can freely select the number of shared files required to reconstruct.
-
You can share multiple files and folders together.
-
No need password.
-
With verify function.
-
Identify shared groups by Group ID.
-
Identify file corruption with check code.
-
High confidentiality due to encryption.
-
High reliability by sharing.
-
The shared processing has been speed up by making full use of SSE2, AVX2, AVX-512, and parallel processing.
-
OS:Windows 11 / 10
[Free Version]
-
You can use it for free.
-
Cannot be executed from the command line
-
The maximum number of shares is 5
Key features
-
Share the files.
-
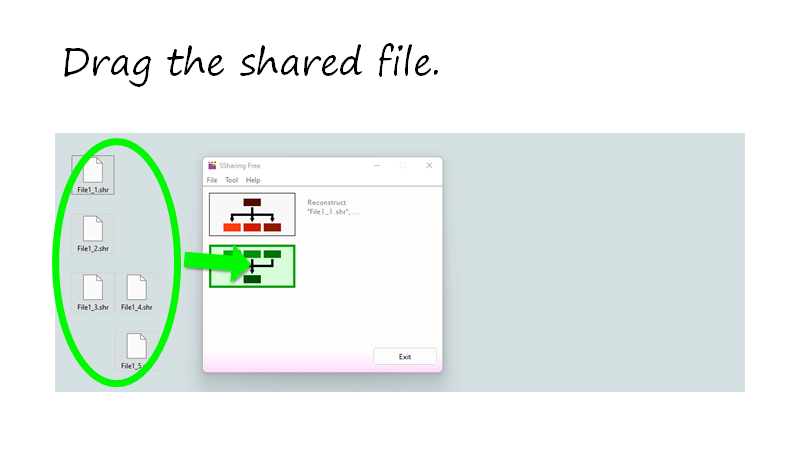
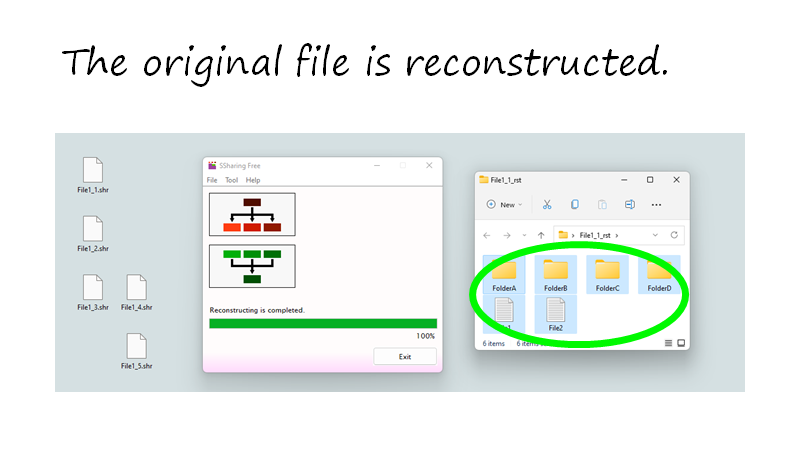
Reconstruct the shared files.
-
Validate the shared files.
-
Archive multiple files and folders.
-
Compress the file.
-
You can identify the shared group.
-
You can identify the corrupted file.
-
Generate a random number using CNG, Algorithm ID (RNG).
-
Search for thresholds during reconstruct.