
FDM II spe
App details
About FDM II spe
DEFINITION
File Destroy Manager (FDM) is a semi-professional file shredder with the free disk space sanitization module included.
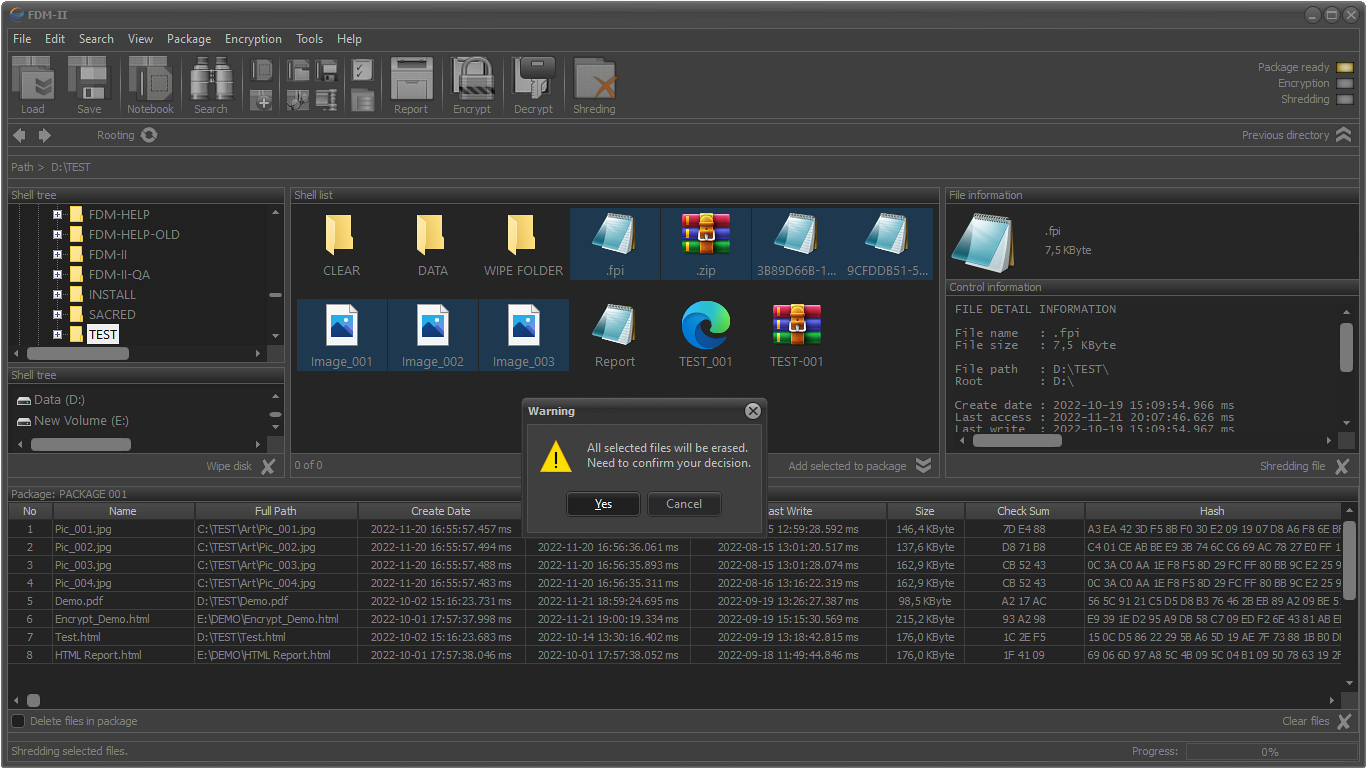
Unlike all other similar applications, FDM has the ability to destroy files whose meta information is saved in specialized file packages.
The application can be used to destroy critical information, to design and execute meta-scenarios, to protect files and folders from unauthorized access, and as an element of specialized cyber security systems.
FIELD OF APPLICATION
Deleting a file only removes the entry of the file (pointer) from the file index in a file system. Thus, the actual data still remains on the drive and can be easily recovered with the help of a specialized data recovery tools.
It’s important that you completely destroy the data from your storage devices by using a data erasure tool before disposing them off or else donating them to someone.
FDM uses some of the most effective standard digital data erasure algorithms used by government organizations and corporate structures, as well as hybrid solutions that are less familiar.
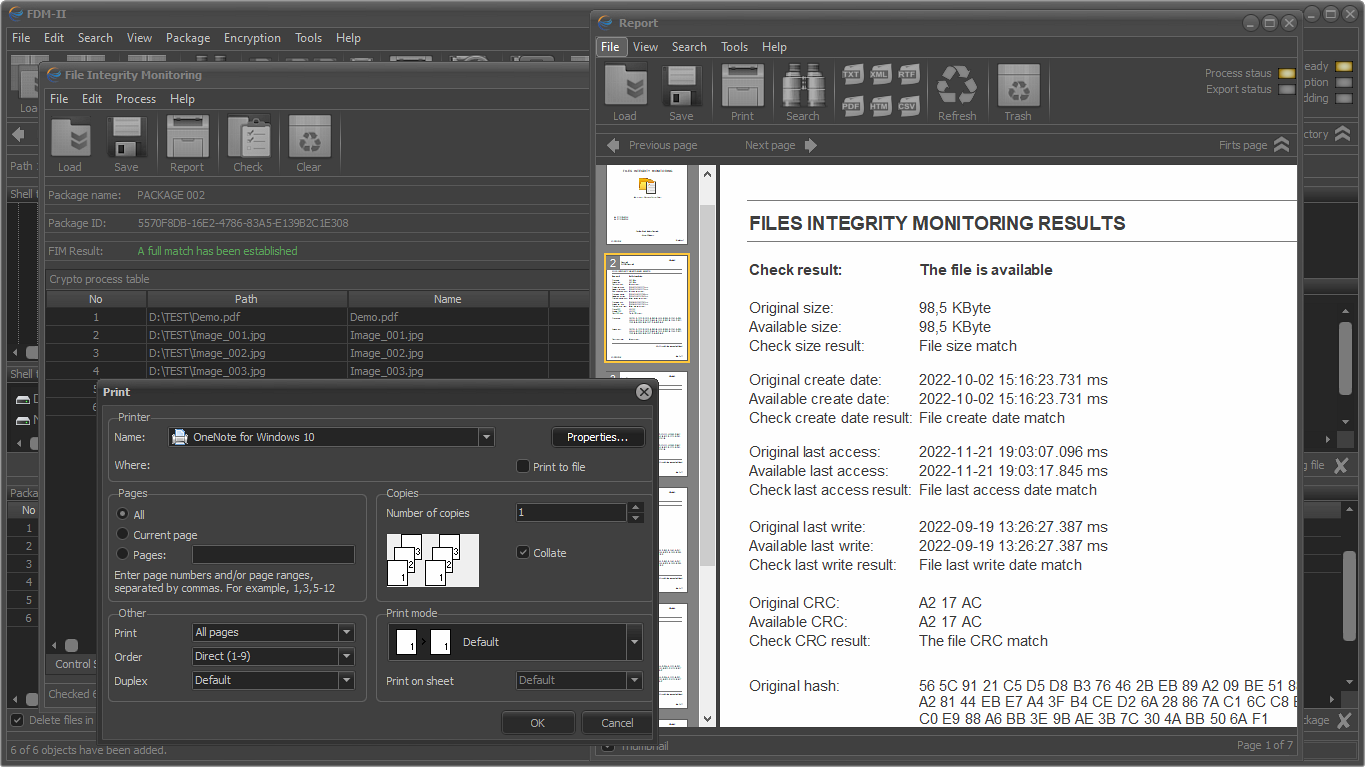
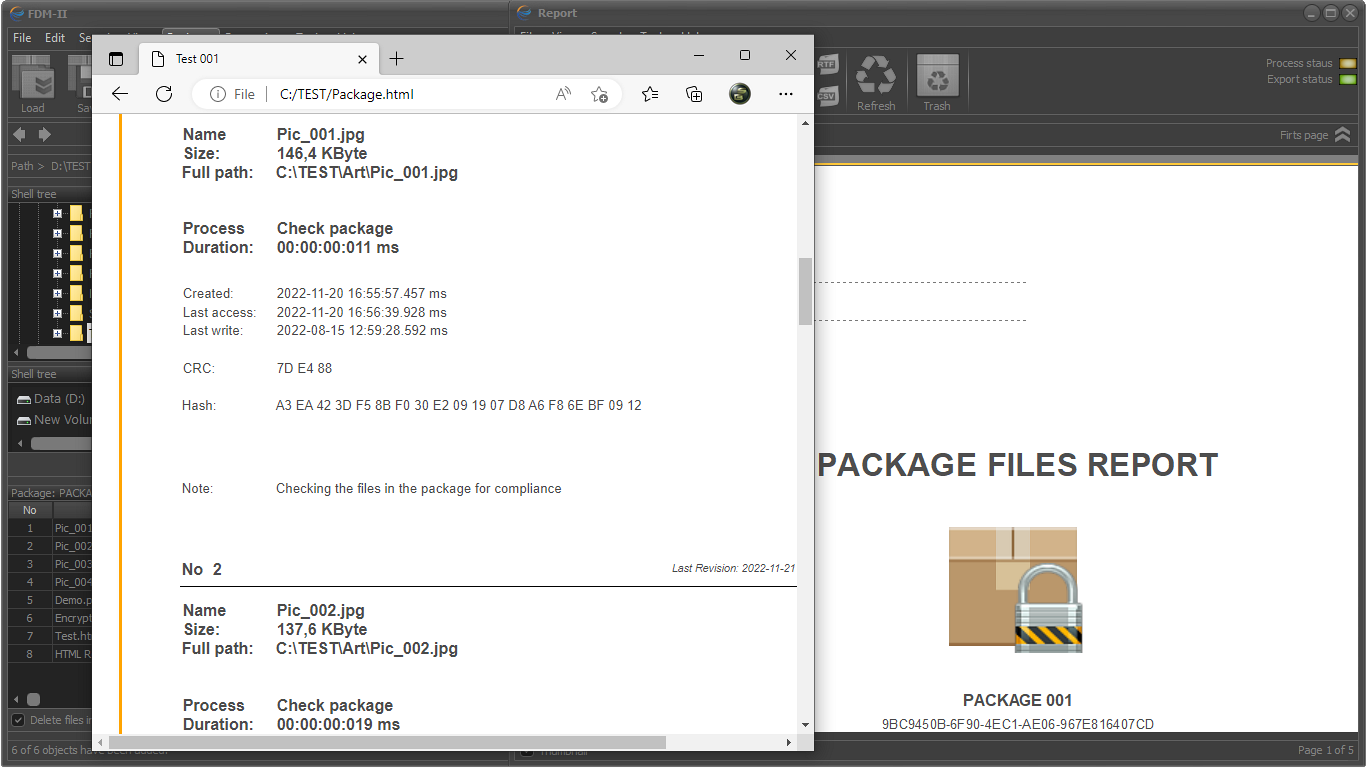
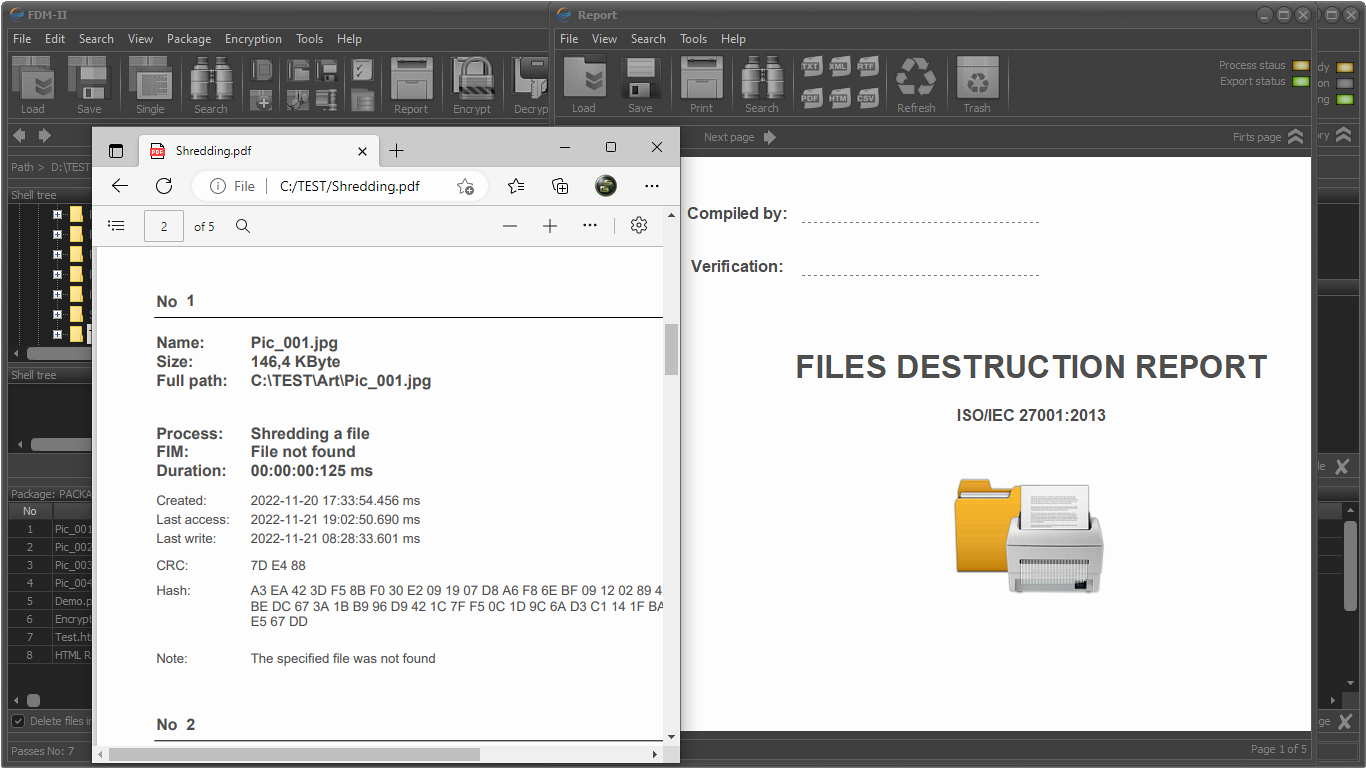
One of the main advantages of FDM is the ability to automatically generate control reports. This makes the application an indispensable tool when building cybersecurity systems that meet the requirements of ISO - ISO/IEC 27001 and ISO - ISO/IEC 27002.
The application’s hybrid functions use proven algorithms described in NIST SP 800-88 and NIST SP 800-90A, which include Hash DRBG (Hash Function Based), HMAC DRBG (HMAC Based), and CTR DRBG based on block ciphers in counter mode), as well as some specific solutions used in BS 1443 technology.
TECHNOLOGICAL SOLUTIONS
The correct choice of algorithms and software technologies for the destruction of digital data is a guarantee of the high efficiency and reliability of the application.
The application uses the following algorithms to destroy digital information:
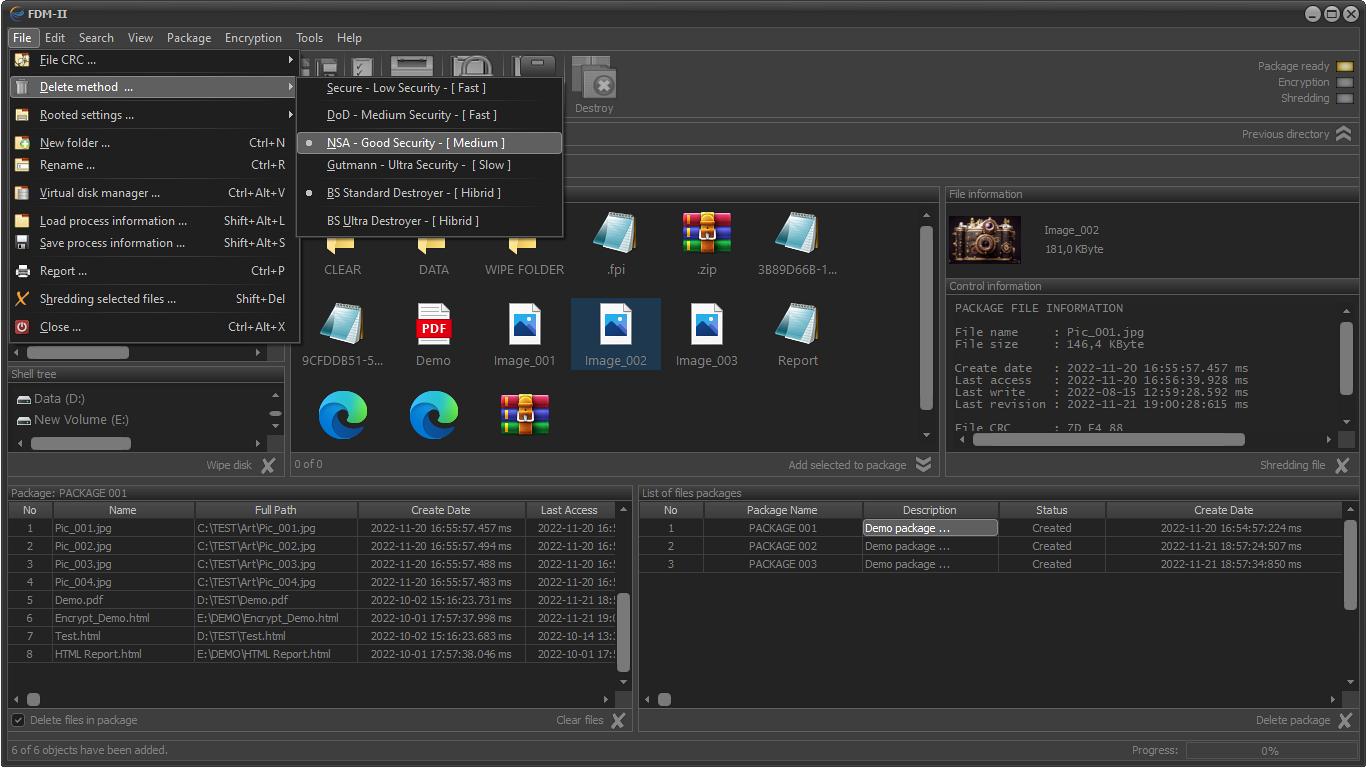
STANDARD ALGORITHMS
(basic technologies)
- NIST Special Publication 800-88
- NIST Special Publication 800-90A
- NIST Special Publication 800-90B
- U.S. Department of Defense DoD 5220.22-M (ECE)
- U.S. Department of Defense DoD 5220.22-M (E)
- U.S. Department of Defense DoD 5220.28-M - STD
- U.S. Army AR 380-19
- U.S. Air Force AFSSI-5020
- Canadian RCMP TSSIT OPS-II
- British HMG IS5
- Peter Gutmann
- Russian Standard – GOST-R-50739-95
SPECIAL ALGORITHMS
(hybrid technologies)
- BS Standard Destroyer - Hybrid
- BS Ultra Destroyer - Hybrid
Key features
-
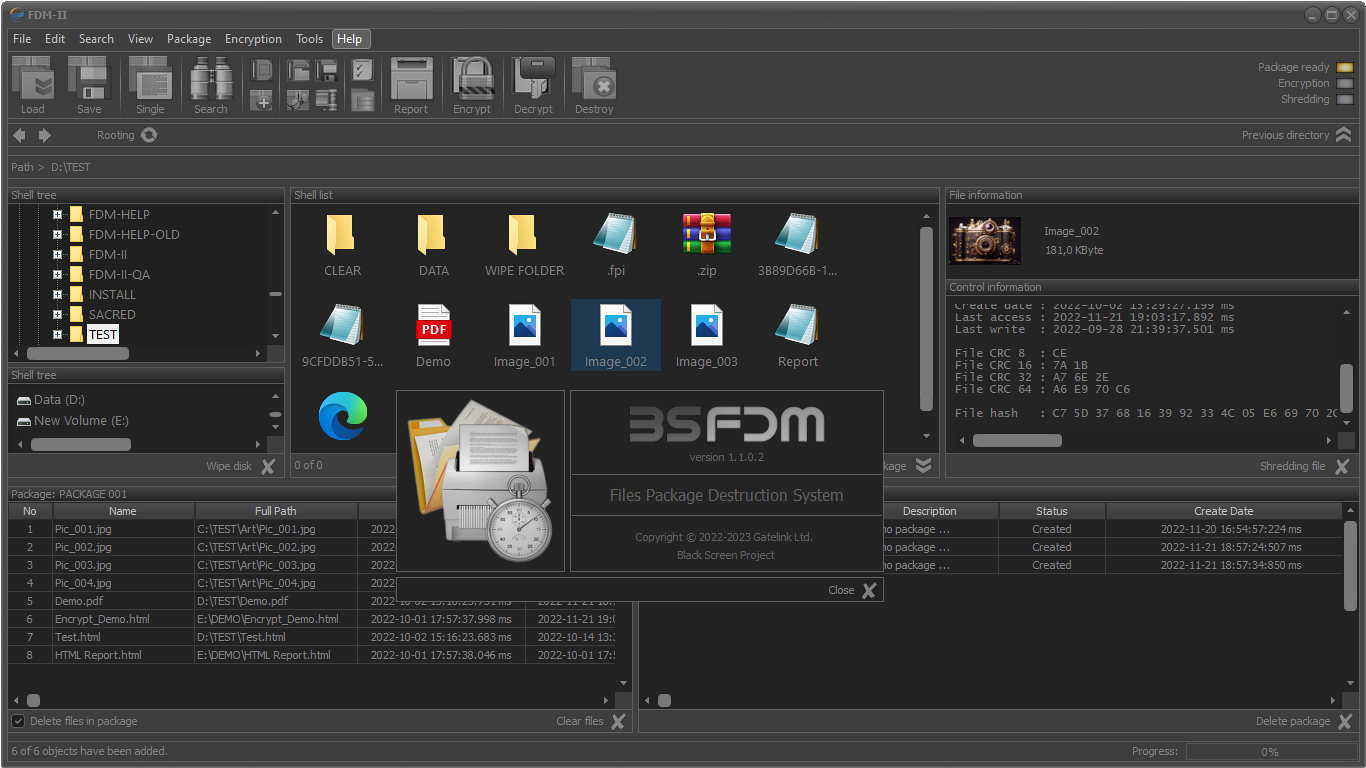
File and directories shredding
-
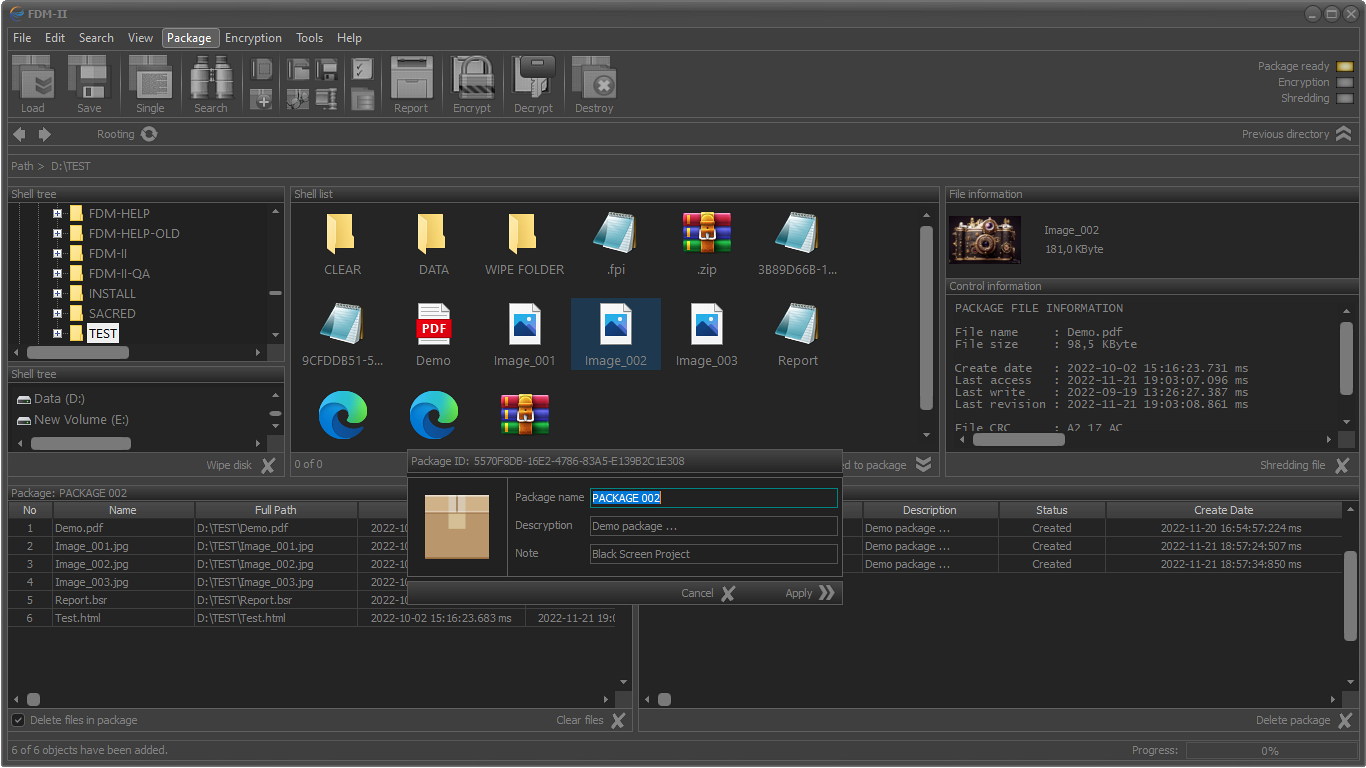
Files package sheredding (destroing files in the package)
-
Hybrid shredding methods
-
Strong security files and folders destroyer
-
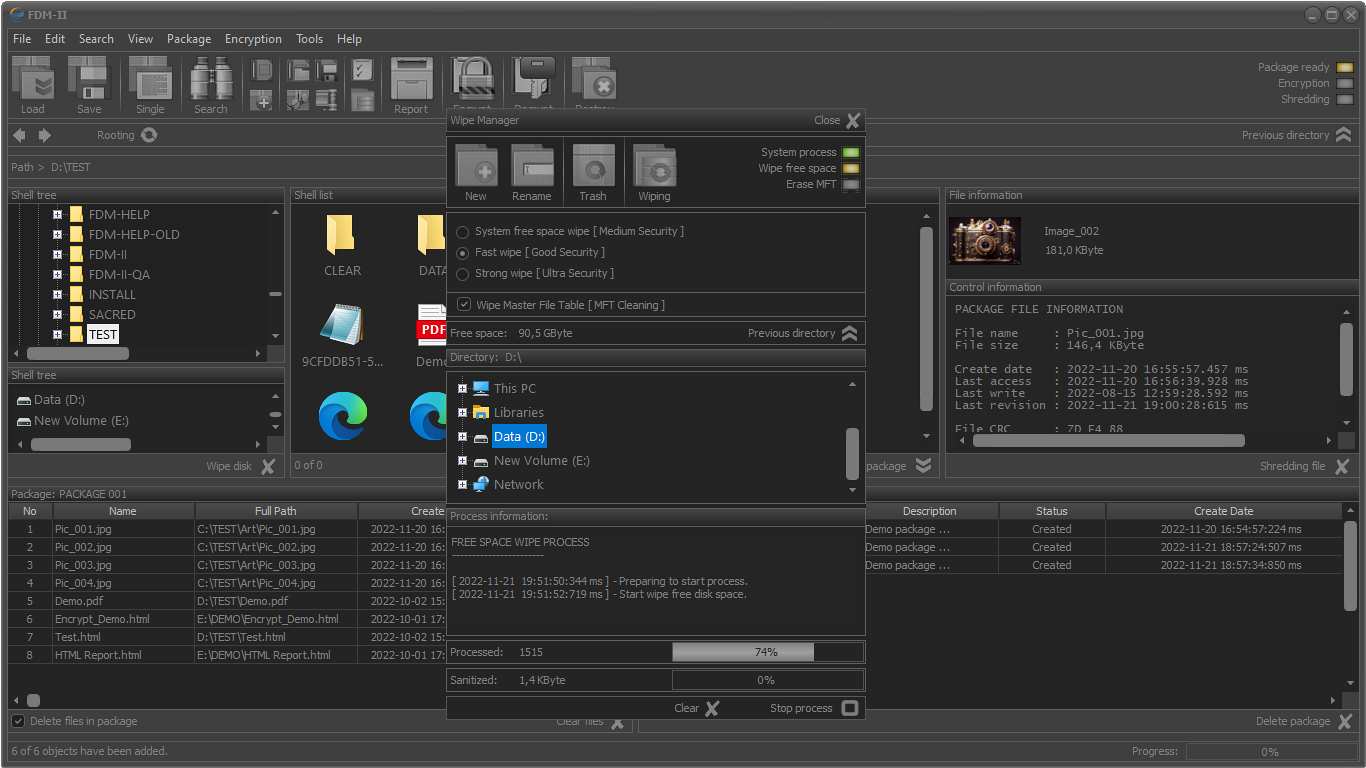
Free disk space wiping manager
-
System wiping
-
Hybrid wiping methods
-
Master file table (MFT) sanitize functions
-
Real time process control
-
Processes control reports
-
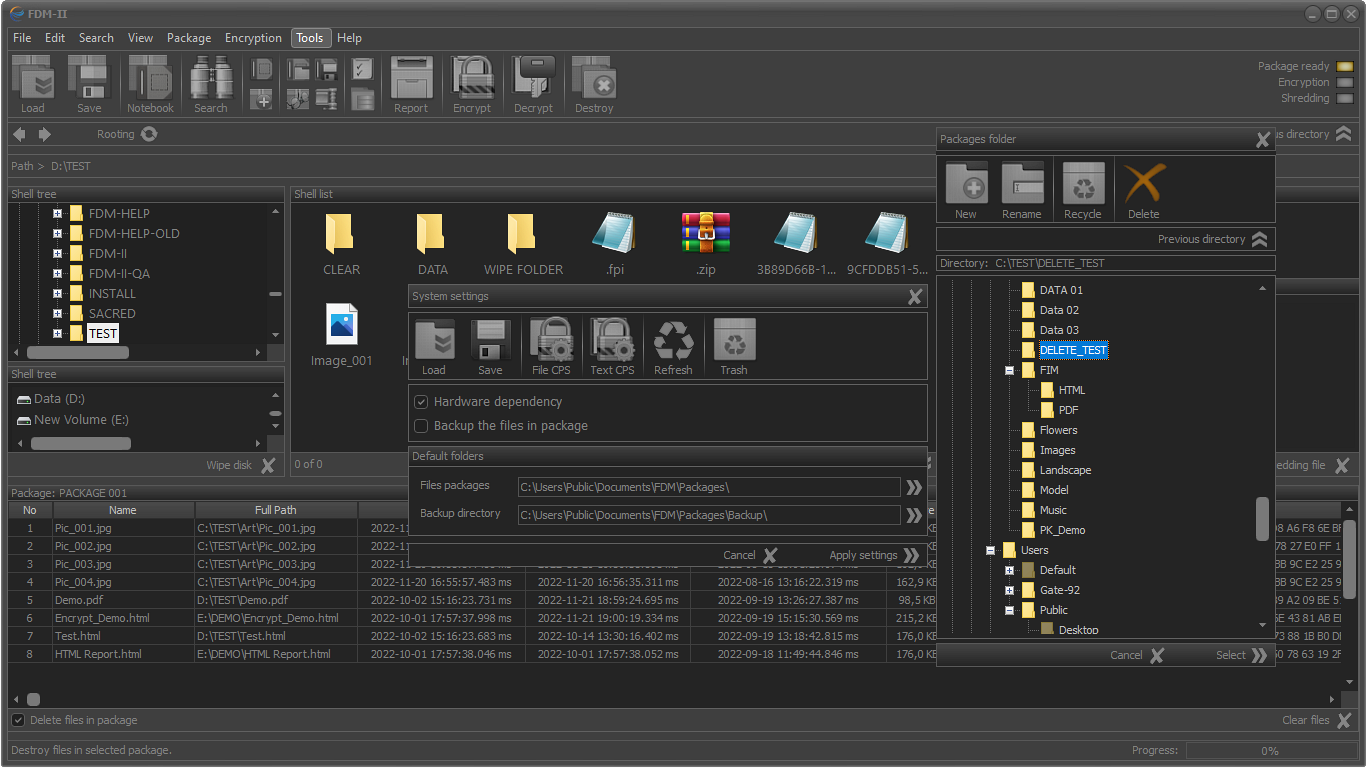
File integrity monitoring (FIM)
-
File security explorer